ACSC Essential Eight, Regular Backups
As we round out the ACSC Essential Eight, the focus becomes how to recover if something goes wrong. The strategy aligned to "Regular Backups" provides a path to recover from a cybersecurity incident. While in the context of Essential Eight, we are focusing on recovering from the actions of a cybersecurity incident, regular backups also provide us with a path to recover from other types of incidents like hardware failure.
To date we have covered Application Control, Patch Applications, Configure Microsoft Office Macro Settings, User Application Hardening, Restrict Administrative Privileges, Patch Operating Systems, and Multi-factor Authentication.
Recap: What is the ACSC Essential Eight
Before we dive in, let's recap why we are reviewing the ACSC Essential Eight. The Essential Eight is a set of hardening or mitigation strategies designed to defend and protect your windows infrastructure. These strategies are not unique to windows as they can also apply to other environments.
The Essential Eight is also a starting point in building your security posture. Additional cybersecurity strategies are available in the ACSC Strategies to Mitigate Cybersecurity Incidents Framework and the ACSC Information Security Manual (ISM)
Why focus on Regular Backups
By realistically assuming that you will lose access to your IT resources at some point, plans need to be in place to ensure business continuity. With the ACSC Essential Eight, the focus is on four key elements of the backup and recovery process.
- Performing and retaining backups
- Securing backups by ensuring only appropriate staff have access
- Protecting backups from modification and deletion
- Testing restoration of backups
The key outcome here is to ensure that, if you were to fall victim to a ransomware or other form of destructive event, important data, software, and configuration settings will not be lost and where necessary recovery can be performed in an appropriate timely manner.
Challenges we regularly see with backup and restoration processes which are covered by these four key elements include:
- Many small businesses that have existing backup recovery processes have the performing and retaining backups element covered. However, we often see that they are not testing restoration of backups so there is no verification of the completeness or capabilities of the backup. Sometimes the failure to restore a backup can be attributed to the lack of experience or knowledge on how to restore a backup.
- Many businesses have controls in place to manage access to the original data sets, but to secure the backups, controls must be put in place to ensure only appropriate representatives access these backups. This can minimise the ability of a malicious actor exfiltrating data through the backup files.
- One of the first things a malicious actor will look to do is to locate and delete the backups. If they are unable to delete backups, they will often try to modify the backup process to make the backups ineffective.
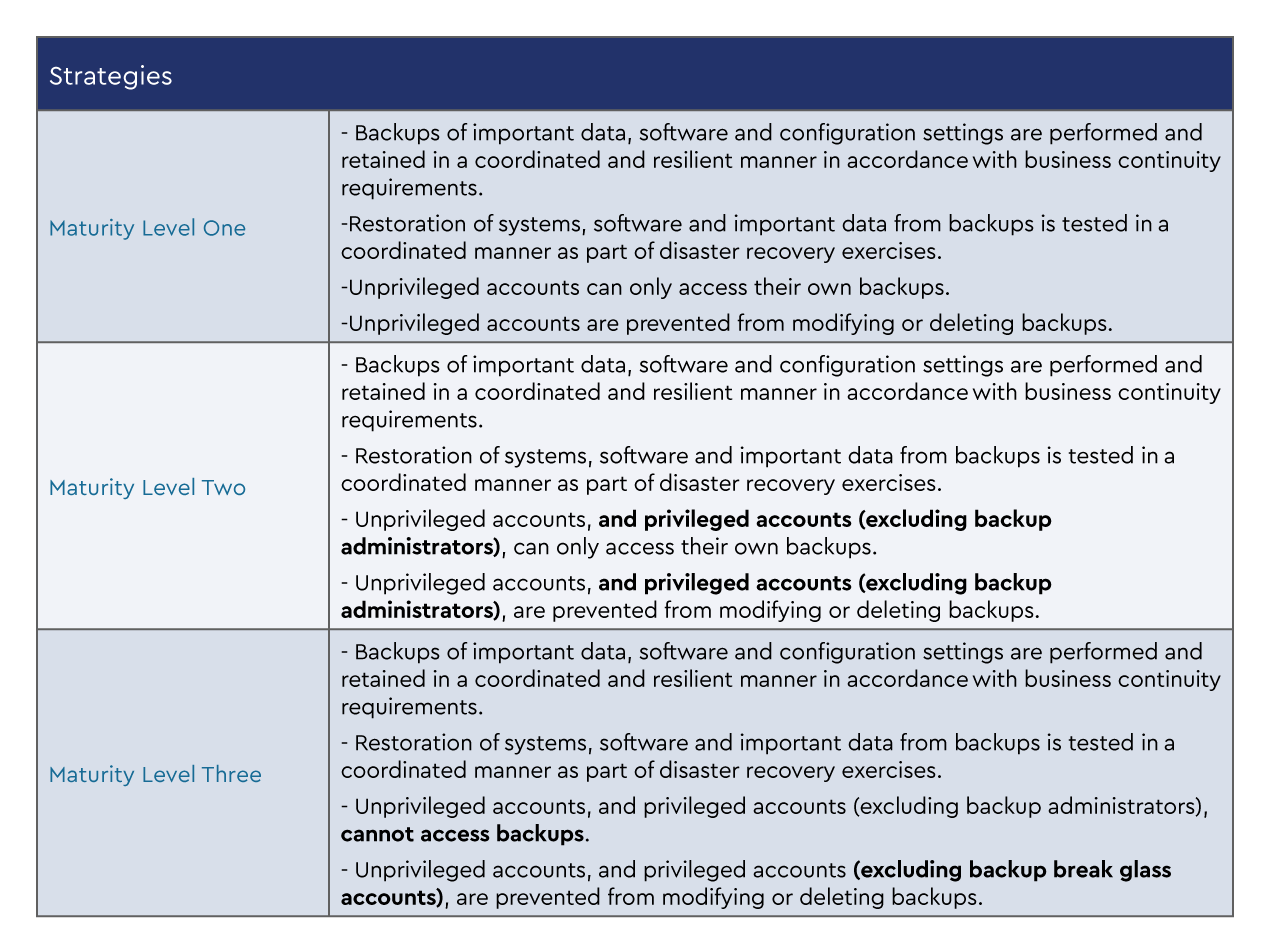
The three maturity levels of regular backups
The ACSC Essential Eight has three targeted maturity levels based on risk profiles. To determine your target profile, you will need a clear understanding of the risk profiles.
The strategies listed are taken directly from the ACSC Essential Eight Maturity Model (November, 2022). Each maturity level builds on the foundation of the lower maturity level, where lower maturity level items need to be completed before progressing to the next level.
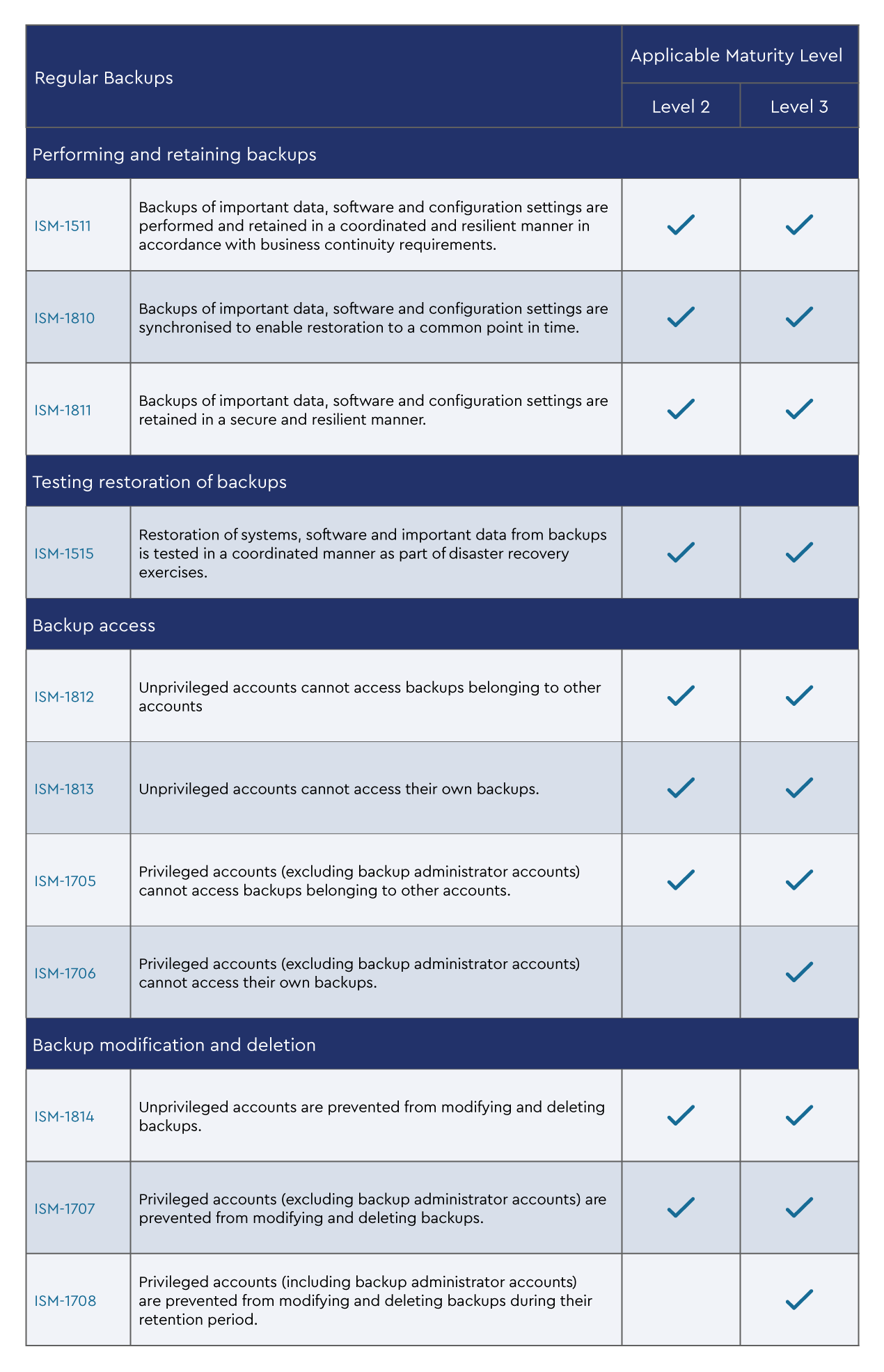
Regular Backups and the Information Security Manual
As you build out the security posture of your own business and that of your customers, you will be looking beyond the Essential Eight to a broader framework like the ACSC Information Security Manual.
The following mapping of the Essential Eight to the ISM framework will assist in building clarity. It can also help if you are looking to map to other cybersecurity frameworks.
Other elements outside of the Essential Eight which you should consider include a business continuity plan, data backup and restoration processes and procedures, as well as a “digital preservation policy.”
Conclusion
Often the challenge with recovering from an incident is knowing how to restore the backups or finding that the required data was not included in the backup. With this in mind, classification of important data, as well as software and configuration settings are critical. Without undertaking the appropriate classification process, you may find your backups are not complete or synchronised in a manner that allows you to restore all systems to an appropriate point in time. The testing process also presents an opportunity to not only ensure the recovery process is known and documented, but also that the restored environment is functional.
Alternatively, failing to secure the backups properly means that a malicious actor could steal the data, causing a serious risk to the business or the malicious actor could simply delete the backups prior to proceeding with a ransomware attack. It could be said that with unsecure backups, you don’t have backups. You should also be aware that if the malicious actor gains access to backup configuration, they could modify the back process, again making the backup ineffective.
Regular backups are a key component of your cybersecurity and business continuity plan. Backups ensure you can recover from a destructive incident. For them to be effective they need to be secured, protected, and monitored. The ACSC Essential Eight provides guidance on the fundamental requirements for successfully implementing a backup strategy.






