ACSC Essential 8, patch applications
As mentioned in the second article in this series, IT solution providers in Australia often discuss the Australian Cyber Security Centre (ACSC) Essential Eight with their customers. However, this conversation can sometimes be challenging or confusing because there is a knowledge gap, which is essential for managed service providers (MSPs) to address—you need to be comfortable with this subject from a cybersecurity perspective so you can communicate its importance to your customers.
This series aims to assist you with that. And today, we will dig into the second component of the ACSC Essential Eight: patch applications.
Application patching is a topic that often slips under the policy/process radar for both IT solution providers and your customers. But considering the fact that 34% of infection vectors can be attributed to vulnerability exploitation, vulnerabilities came a close second to phishing when it came to security incidents in 2021. Patch applications should be top of mind!
Your challenge here is how you can help your internal teams and customers understand why “patch applications” is an essential process and how it can help them better protect their cyber assets.
With this in mind, let's walk through what needs to be considered when patching applications.
Fortunately, if you have already had the application control strategy discussion, you are already on your way.
In case you haven’t, here’s a quick recap of the Essential Eight.
What is the ACSC Essential 8?
Briefly, the ACSC Essential Eight is a prioritised set of eight “essential” mitigation strategies for building cyber resilience and protecting Australian businesses from cyberattacks. The first of these measures is “application control,” which we explored earlier in this series.
The second strategy is patch applications, which we will explain further in this post.
Patch applications explained
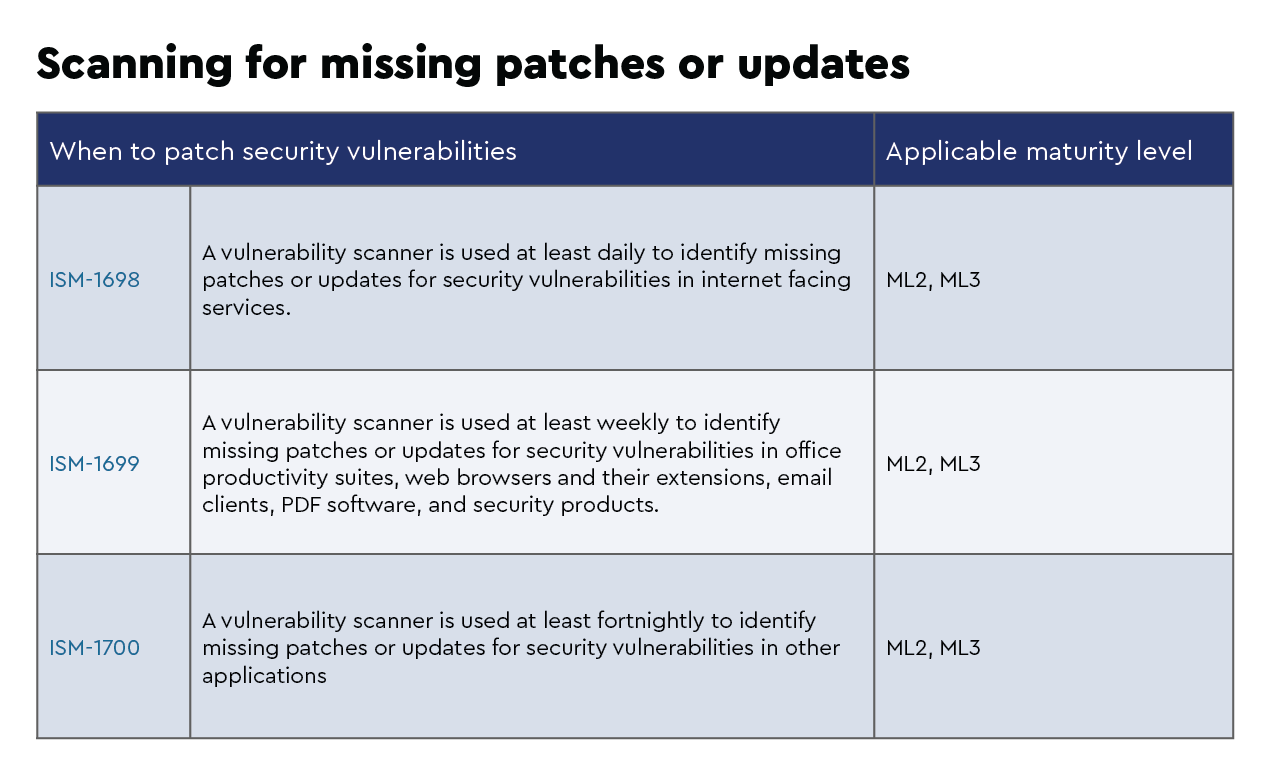
While it is likely you will build a software asset register as part of the application patching process, the use of a vulnerability scanner is critical to ensure that your applications are indeed up to date and that there are no unexpected applications that are not catalogued and patched.
The patching process here is supported by application control, which provides clarity on which applications are installed and therefore, need to be patched. You can get more information in the ACSC article, Assessing Security Vulnerabilities and Applying Patches, but what’s key here is that you need to know what applications a client has, before you can patch them.
The customer (or end-user) challenge
Therefore, one of the main challenges you will experience with patching applications is identifying which applications are installed and how to maintain them in the end-user computing space.
When we discussed application control, we talked about how many customers do not have an asset register of the software they use. This is typically because they allow users to install and use whatever application or browser they desire. Thus, they have no visibility of the involved risks.
Without knowing what applications are installed, where do you start when it comes to application patching? Fortunately, the patching process on servers is more regimented as they normally exist to provide specific services and are tightly controlled.
As with application control, much of your upfront process here will be educating the decision-makers in terms of standardising the applications in use. You will need to help them understand what is required when selecting applications and vendors, as well as offer support as they build a selection/validation process.
Organisational impact
The upfront and maintenance costs can be high from a time and effort, staffing, and software perspective. Much of this is because you have to establish a process to automatically identify installed applications and how they need to be maintained, as well as acquire the required maintenance tools.
Fortunately, user challenges are generally rated as low. Most users will not be concerned with which minor version of a software package is in use, assuming it works as expected and the process of updating it is, from their perspective, not onerous.
It should be noted however that if there is a major functional change (i.e., a major release) staging may need to be considered.
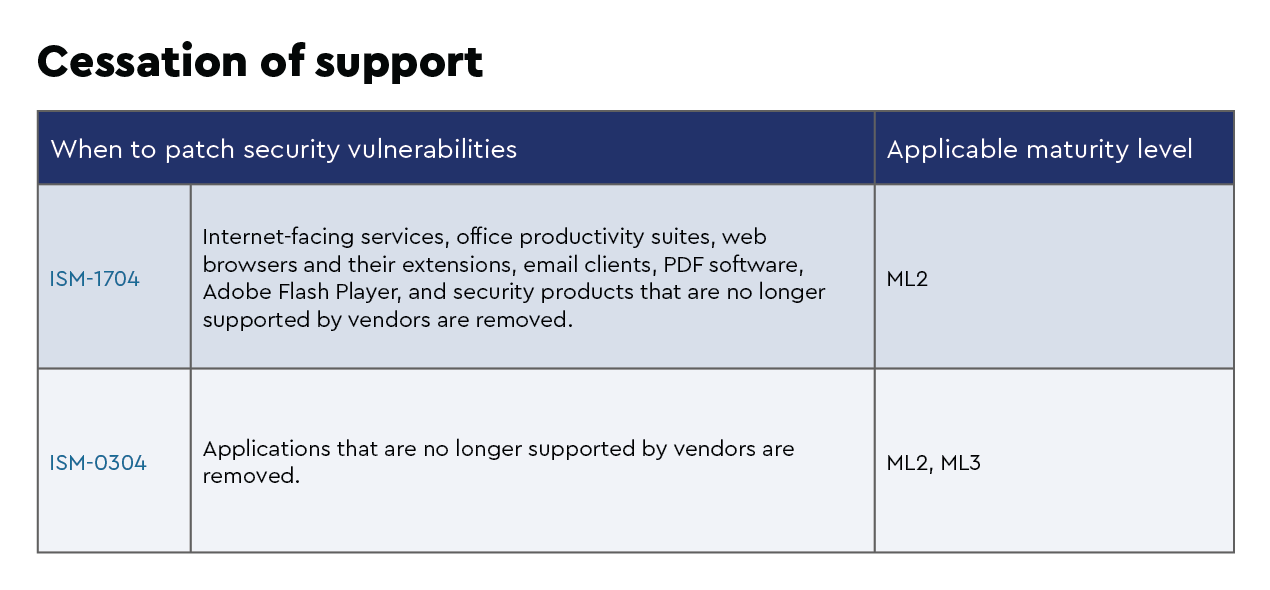
Having said that, there are times when your biggest challenge will be how to handle the discussion around software that is no longer supported and maintained by the vendor. This can arise, for example, if the vendor is no longer in business.
The application landscape is always changing, and a user will always request new software. As new applications are implemented in the environment you will need to ensure they are accounted for in the patching process.
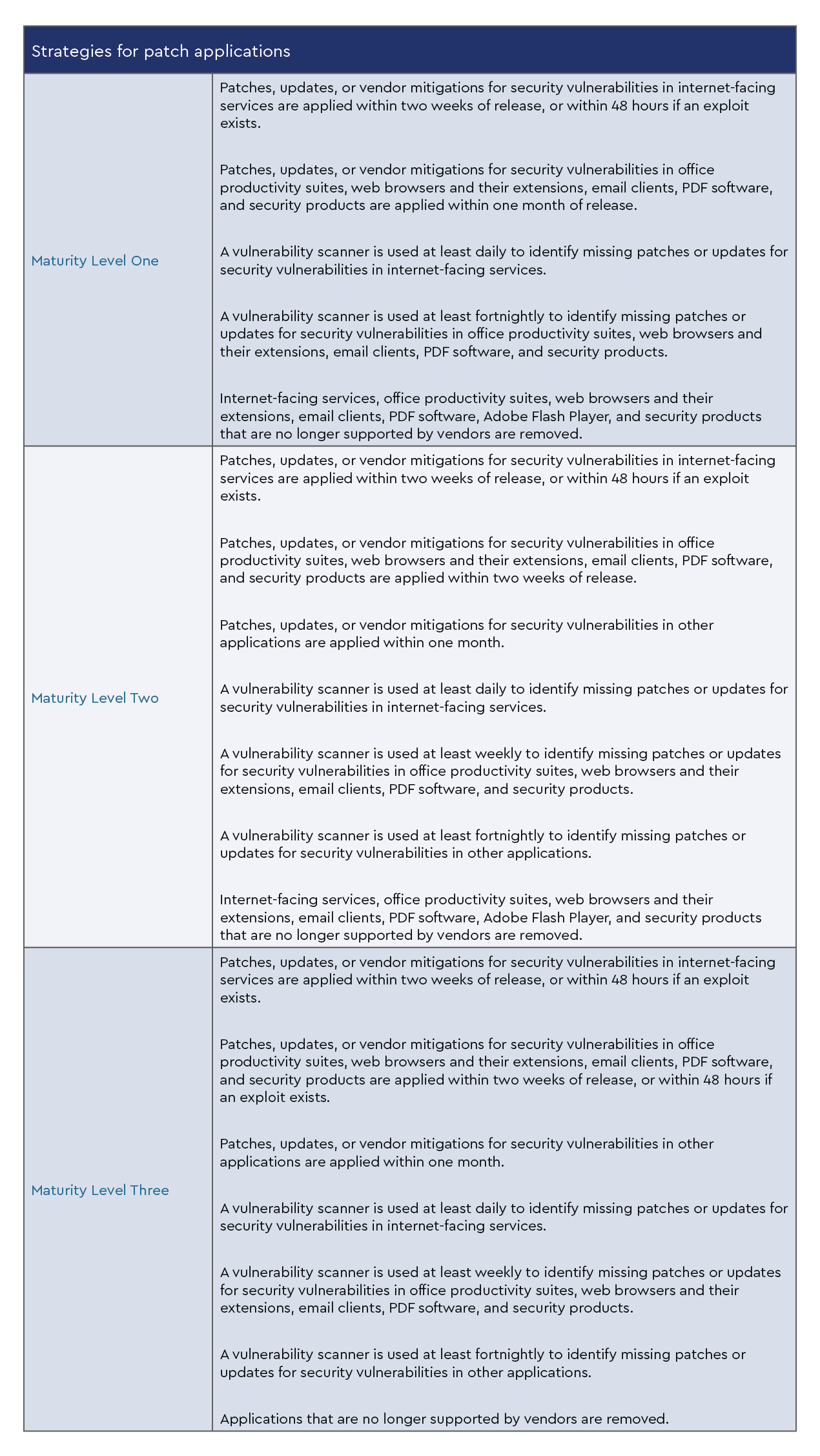
Before you start implementing the Essential Eight, you must determine which level of maturity will work for your client’s environment.
The three maturity levels
To assist with focusing this discussion, the ACSC has defined indicative risk profiles for each maturity level.

As you design your implementation strategy, remember that you will need to ramp up each of the “Eight” before progressing to subsequent maturity levels. The strategies below are taken directly from Essential Eight Maturity Model.
Please ensure you are referring to the complete original documentation from the ACSC when you are building out your application patching strategy as they have many extremely helpful resources you can use when you build your implementation framework.
ACSC Information Security Manual
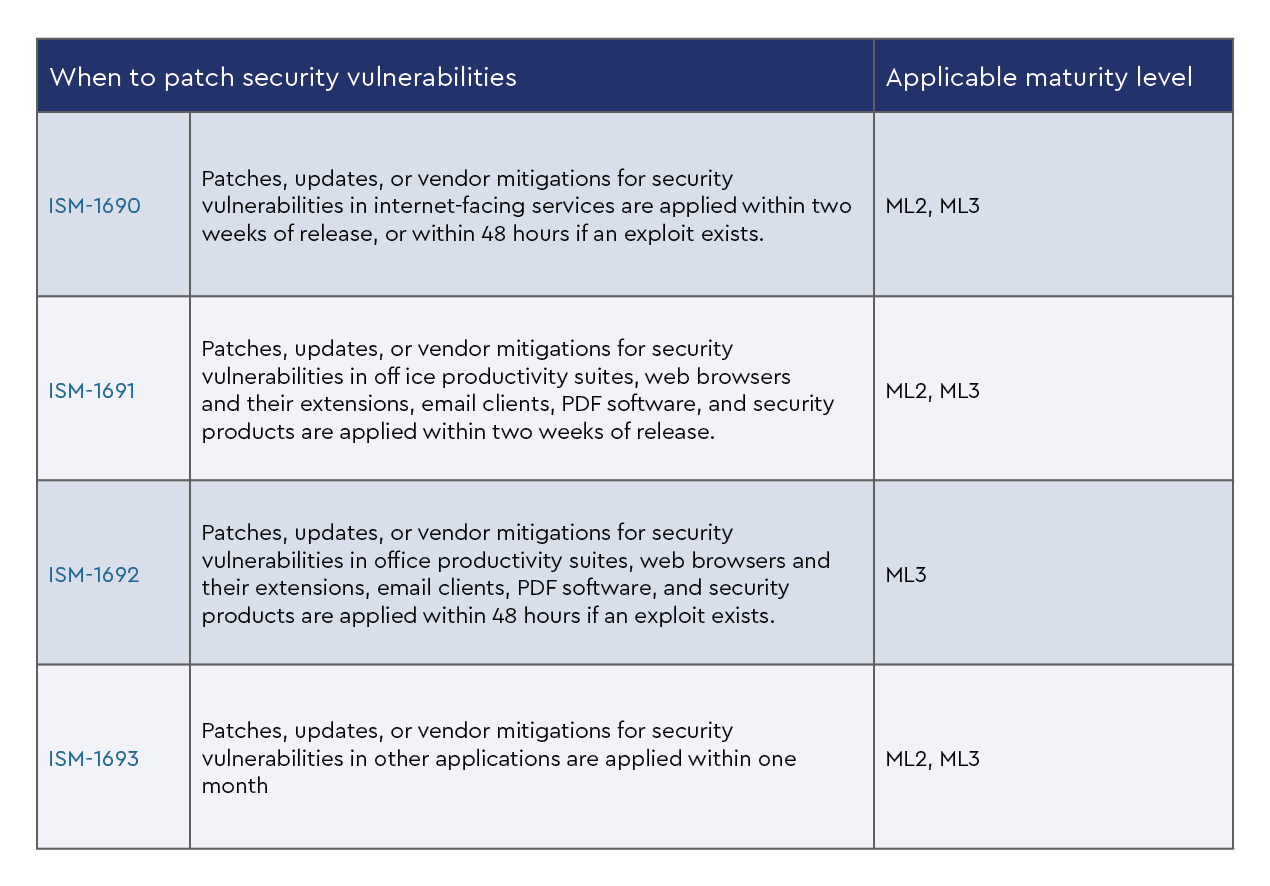
The ACSC uses the ISM to outline a cybersecurity framework using a risk management framework.
As your security posture using the ACSC Essential Eight evolves to level two and level three maturity, it can be mapped to elements of the ISM, which can assist with understanding how the Essential Eight fits within your security framework.
Conclusion
When it comes to hardening the endpoint and reducing the attack surface, implementing a solid application patching mechanism is a practical and essential part of protecting your cyber infrastructure. Its importance is featured in the ACSC Strategies to Mitigate Cyber Security Incidents framework, where it falls under “Mitigation Strategies to Prevent Malware Delivery and Execution,” and has an “essential” effectiveness rating (hence it is included in the Essential Eight).
By understanding the benefits of application patching you will be empowered to meet your customer’s specific concerns and unique challenges. This is particularly important because application patching does not just involve technical procedures; it is also about people and business processes. When you educate your customers and help them improve their cybersecurity, it helps us all be better protected.






