ACSC Essential Eight, user application hardening
The Australian Cyber Security Centre (ACSC) “user application hardening” mitigation strategy is aimed at reducing the attack surface on Microsoft Windows by implementing controls on common components or software. Doing this limits their ability to interact with the Windows environment in an undesired manner.
Besides macros, malicious actors can also leverage the browser and other standard system components or tools in a cyberattack. Since these tools allow users to interact with online content, they can be essential to users’ everyday productivity. As these tools are common, they are attractive to malicious actors as they are a predictable component that can be attacked.
On top of this, once compromised the same tool can then be used to further compromise the environment by downloading additional malicious software.
Recap: What is the ACSC Essential Eight?
The ACSC has established the Essential Eight as a fundamental set of mitigation measures that an organisation can implement to protect and defend their cyber environment. These are prioritised essentials and it is likely that additional mitigation strategies will also be required. More information on these additional strategies can be found in the ACSC Strategies to Mitigate Cyber Security Incidents framework and the ACSC Information Security Manual (ISM).
The three maturity levels
The strategies below are taken directly from the Essential Eight Maturity Model and the maturity level you are aiming for will depend on the risk profile of the organisation.
Remember that you will need to fully complete one level of maturity before you progress to the next level, that is, you must fully meet level one maturity before you can progress to level two maturity.
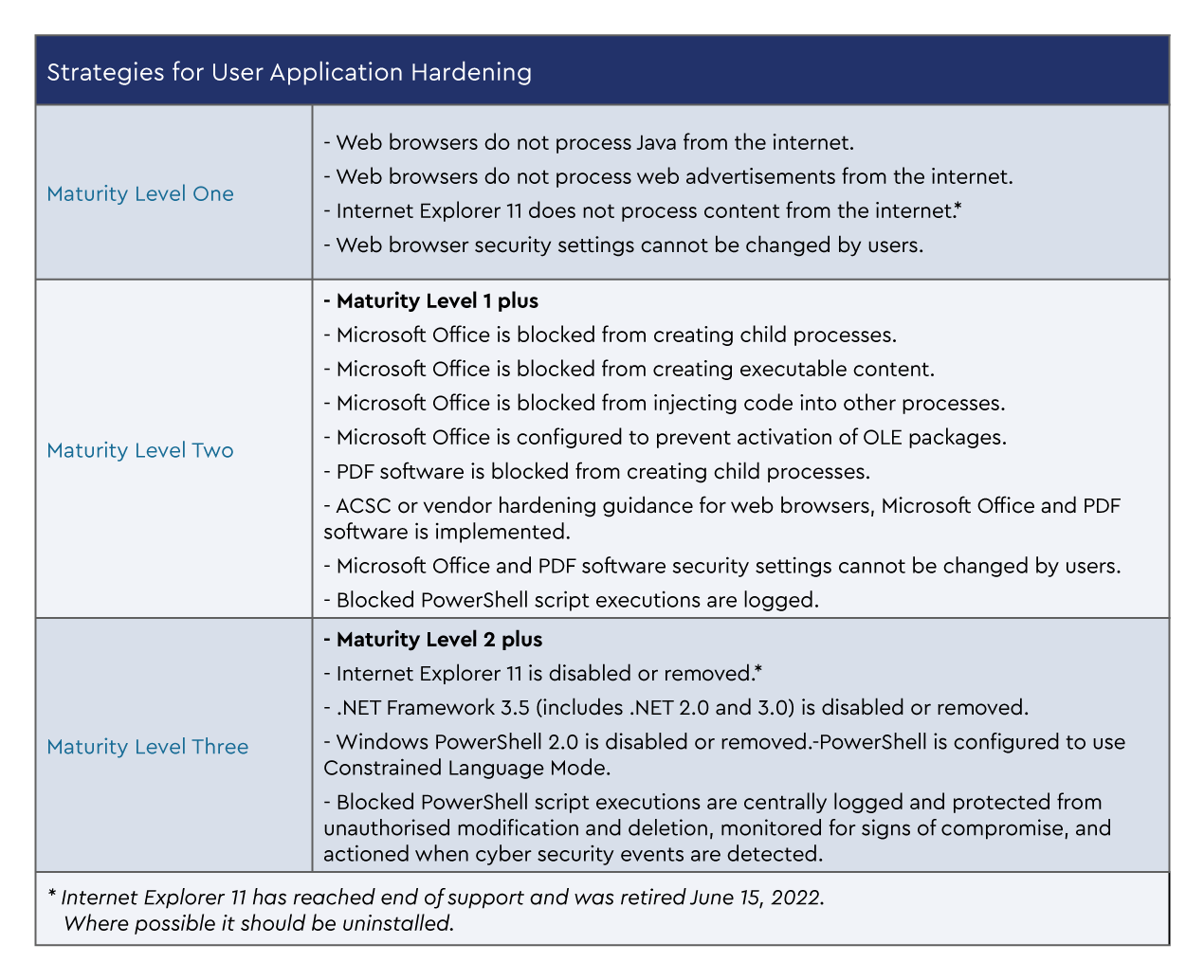
Please ensure you are referring to the complete original documentation from the ACSC when you are building out your processes to implement user application hardening.
ACSC Information Security Manual (ISM)
As you build out the security posture for both your organisation and your customers’, it is likely you will be looking at a broader security framework such as the ACSC Information Security Manual (ISM).
The following mapping of the Essential Eight elements to the ISM framework will assist in creating clarity for how the Essential Eight can fit into that broader security posture. You will only start mapping to the ISM as part of level 2 or level 3 maturity.
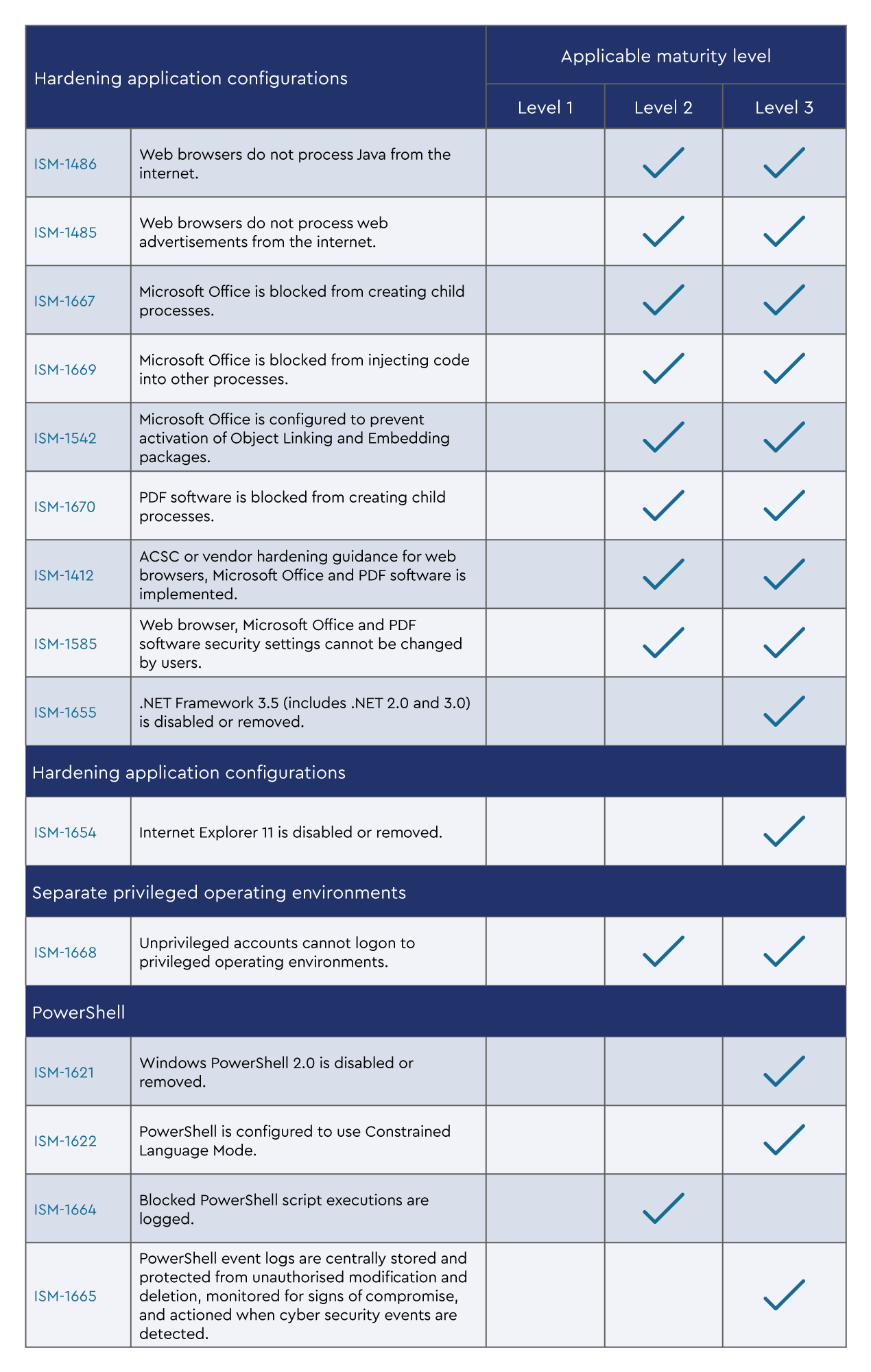
Conclusion
As we see increasing use of standard software components by malicious actors, it is important to ensure appropriate controls are in place to limit both the use, and the capabilities, of these components. Under “user application hardening,” the ACSC has provided hardening guidance on Windows components, Microsoft Office, and PDF tools. When combined with the policy settings to manage Microsoft Office Macros, "user application hardening" is a highly effective mitigation strategy.
Next time around we will discuss managing user permissions in the strategy "restrict administrative privileges." It's critical for companies to manage permissions as without these protocols in place, the user could be manipulated into reversing policy changes and open themselves to an incident.






