ACSC Essential Eight, Multi-factor Authentication (MFA)
Welcome back to our discussion on the Australian Cyber Security Centre (ACSC) Essential Eight, a set of fundamental mitigation strategies designed by the ACSC to help businesses proactively protect themselves from ever-evolving cyberthreats. So far, we have deep-dived into the first six strategies: Application Control, Patch Applications, Configure Microsoft Office Macro Settings, User Application Hardening, Restrict Administrative Privileges, and Patch Operating Systems.
In this blog, we will continue to concentrate on strategies to prevent malware delivery and execution and bring the next strategy—multi-factor authentication (MFA)—into focus.
Recap: What is the ACSC Essential Eight
Before we dive in, let's recap why we are reviewing the ACSC Essential Eight. The Essential Eight is a set of hardening or mitigation strategies designed to defend and protect your windows infrastructure. These strategies are not unique to windows applications as they can also apply to other environments.
The Essential Eight is also a starting point in building your security posture. Additional cybersecurity strategies are available in the ACSC Strategies to Mitigate Cybersecurity Incidents Framework and the ACSC Information Security Manual (ISM).
Why focus on MFA
According to Verizon's Data Breach Investigations Report, more than 80% of hacking-related data breaches occur due to exposed credentials. In many situations, hackers are not hacking, they are just authenticating.
While not all MFA modalities are equal, any MFA-based authentication is much more secure than your traditional single-factor authentication (i.e., username/password combination).
Multi-factor authentication makes you more secure by requiring two or more of the following authentication methods.
- Something the user knows: a password, PIN or answer to a security question
- Something the user has: a one-time code from an SMS, authenticator app, or hardware token
- Something the user is: a fingerprint, face image, or voice imprint
Even though a hacker might have some of your information, such as your username or password, it is much more difficult for them to access other authentication factors.
There is evidence of this through the analysis of authentication events. Microsoft analysed over 300 million illicit sign-in attempts to their cloud services in 2019 and found that 99.9% of the attacks were or would have been prevented through the use MFA.
The three maturity levels of multi-factor authentication
The ACSC Essential Eight is designed around the achievement of maturity levels based on risk profiles. To determine your clients’ maturity level requirements, there needs to be an understanding of the cyber risks within the business.
We discussed these risk profiles in our initial Essential Eight article: The ACSC Essential 8 risk mitigation strategies explained.
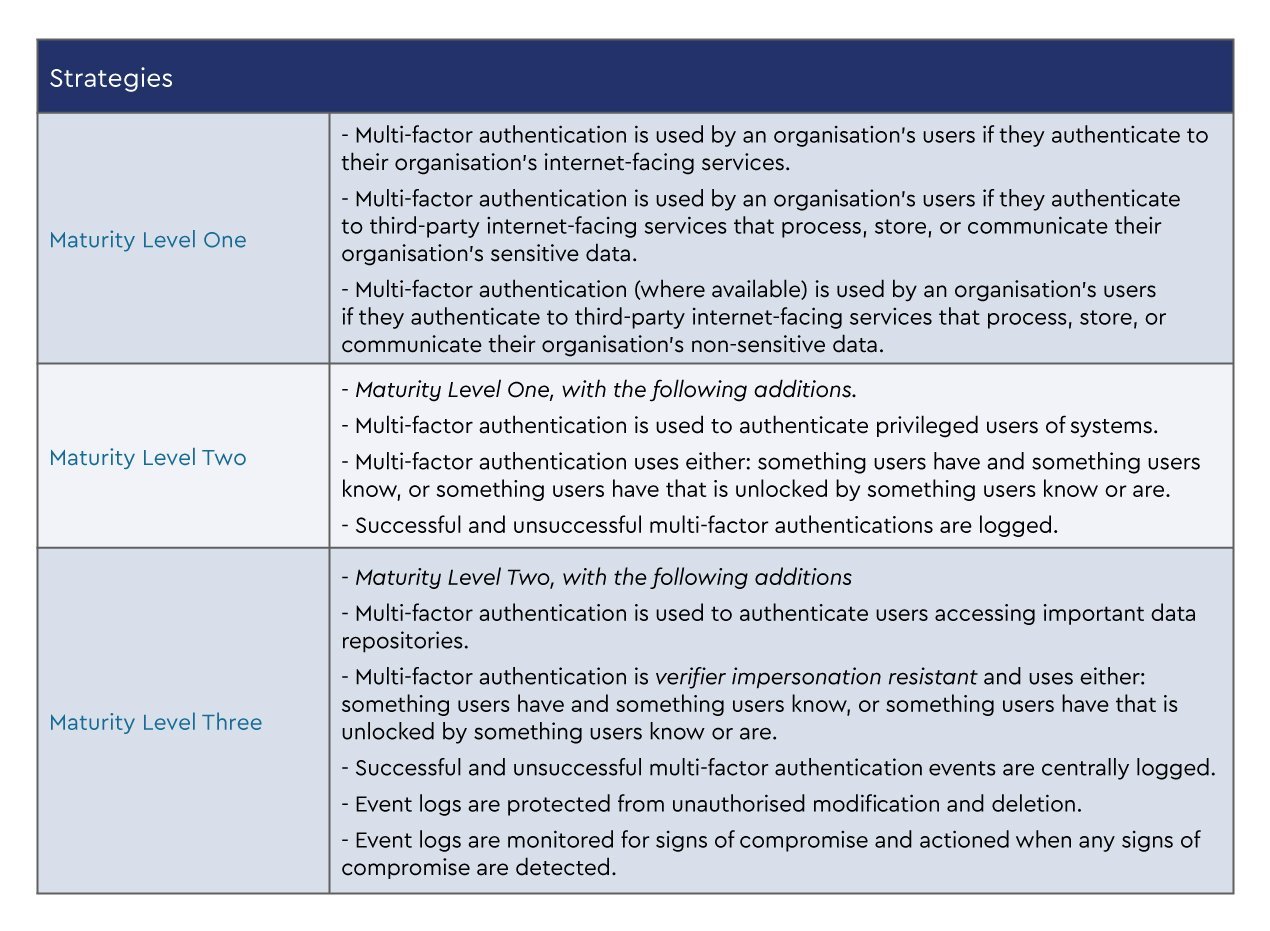
While the Essential Eight maturity levels do not focus on MFA type and authentication strength, it is worth a short discussion. We understand that any form of MFA is more secure, and the choice of MFA implementation will be impacted by your desire for authentication strength, usability, and accessibility.
Historically, SMS one-time password (OTP) has had the broadest adoption as most users carry mobile phones, making it easily accessible. However, it is considered the weakest form of MFA, which has resulted in the adoption of app-based one-time passcodes and push notifications. However, both options have limitations. Some examples are if the user is not permitted to carry a mobile device or if you want to implement “verifier impersonation resistant” or “phishing resistant” MFA. In these situations, you should be looking at FIDO2-based MFA. Security keys provide phishing-resistant MFA as a physical key that a user can carry so that there is no dependence on a mobile device.
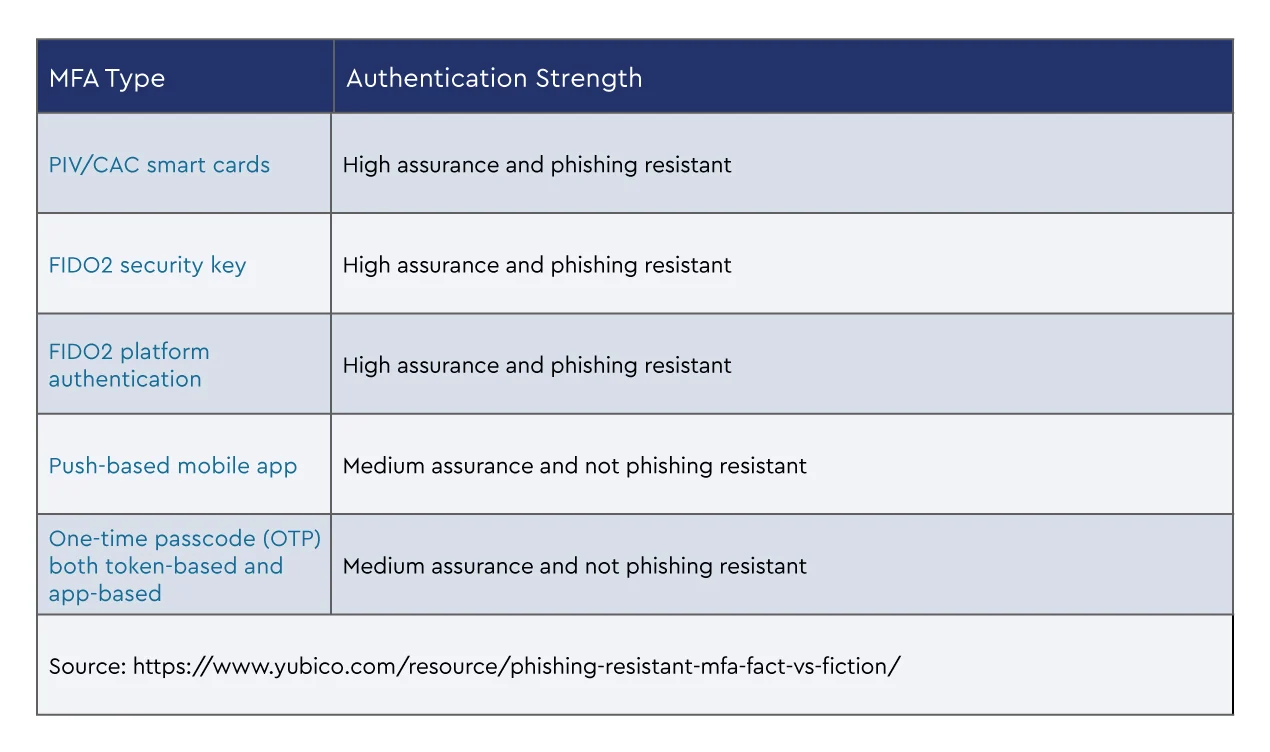
Once the decision is made to implement MFA, you will need an understanding of the cyber risk factors and use cases to determine the best MFA solution for you or your clients.
Multi-factor Authentication and the Information Security Manual
As you continue to build out the security posture for you and your customers, you will likely be looking beyond the Essential Eight to a broader security framework, such as the ACSC Information Security Manual (ISM).
The following mapping of the Essential Eight to the ISM framework will assist in building clarity. This will also make it easier to map to other cybersecurity frameworks.

Conclusion
With the most common attack vectors to the network being compromised credentials and reliance on single-factor authentication, implementing multi-factor authentication is the most effective way to prevent hackers from using compromised credentials.
The three maturity levels from the ACSC will allow you to choose and implement the best MFA solution to meet customer needs and usability requirements.






