Monthly Threat Brief: October 2024
Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU). In this threat brief, we will provide raw data statistics, intel on specific threats, and a list of new detection signatures added to the ConnectWise SIEM™ throughout the month of October.
For a more detailed explanation of the overall trends and analysis of these numbers, check out the 2024 MSP Threat Report. For comparison, September’s threat brief can be found here.
October 2024 stats
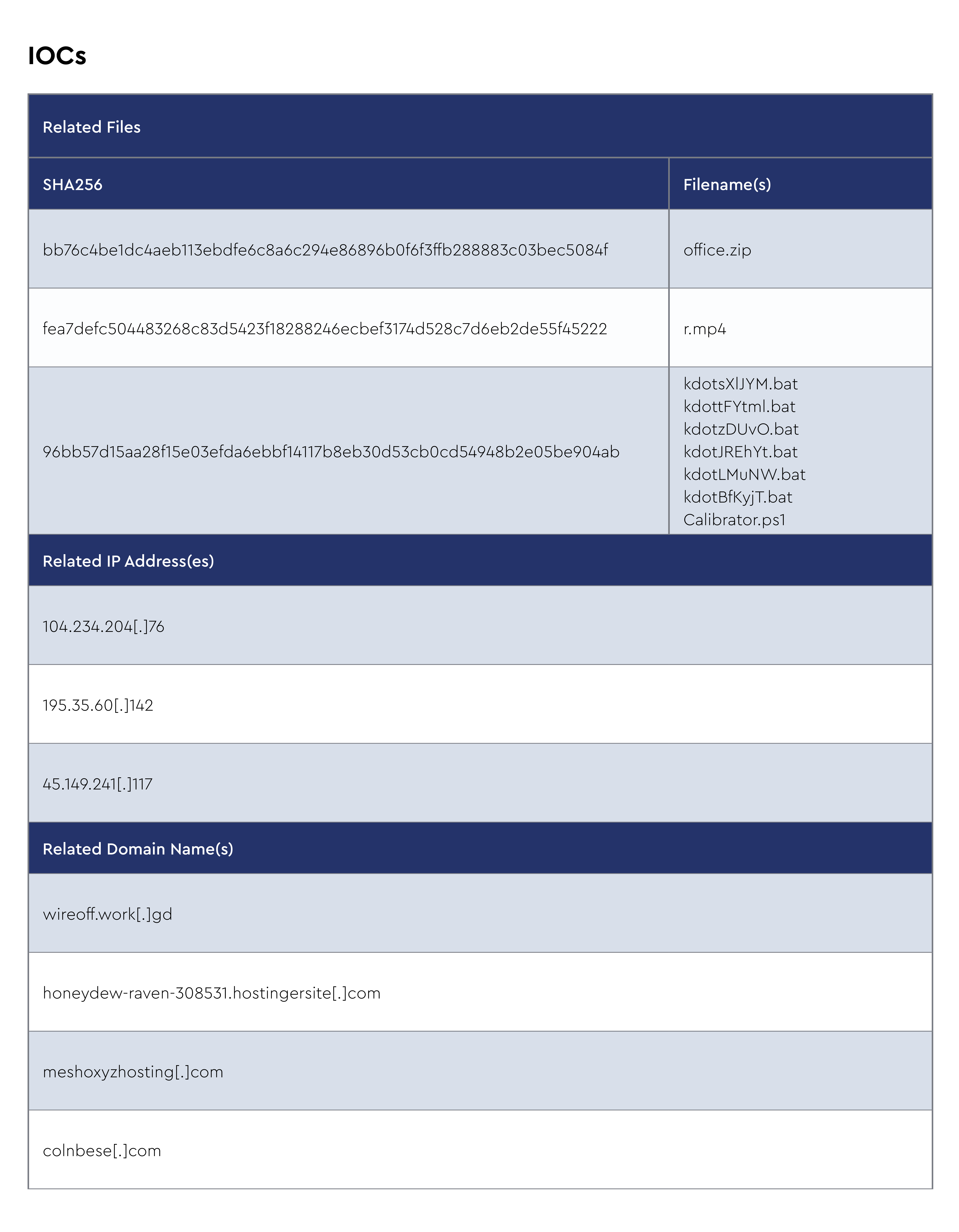
IOCs
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected.
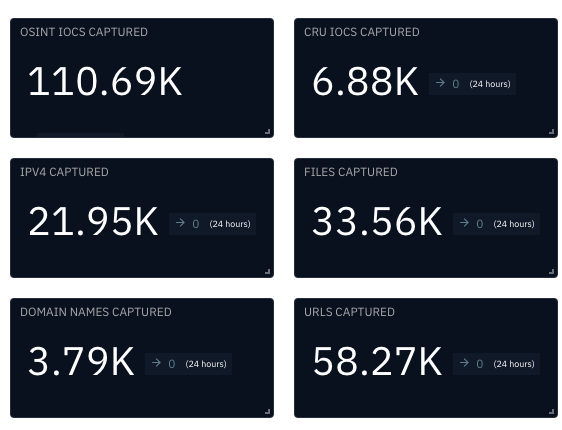
Figure 1: Summary of IOCs collected in October 2024
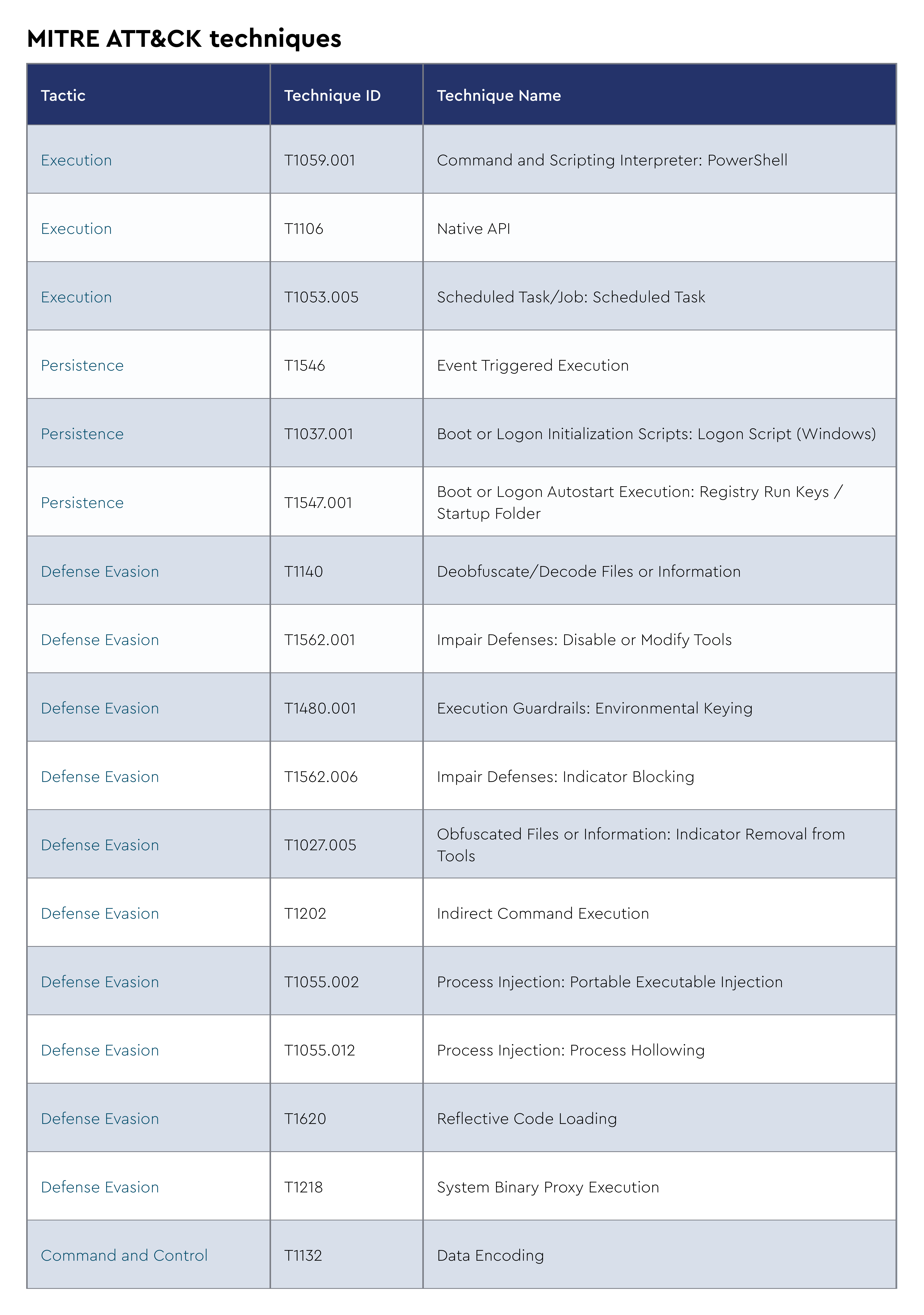
TTPs
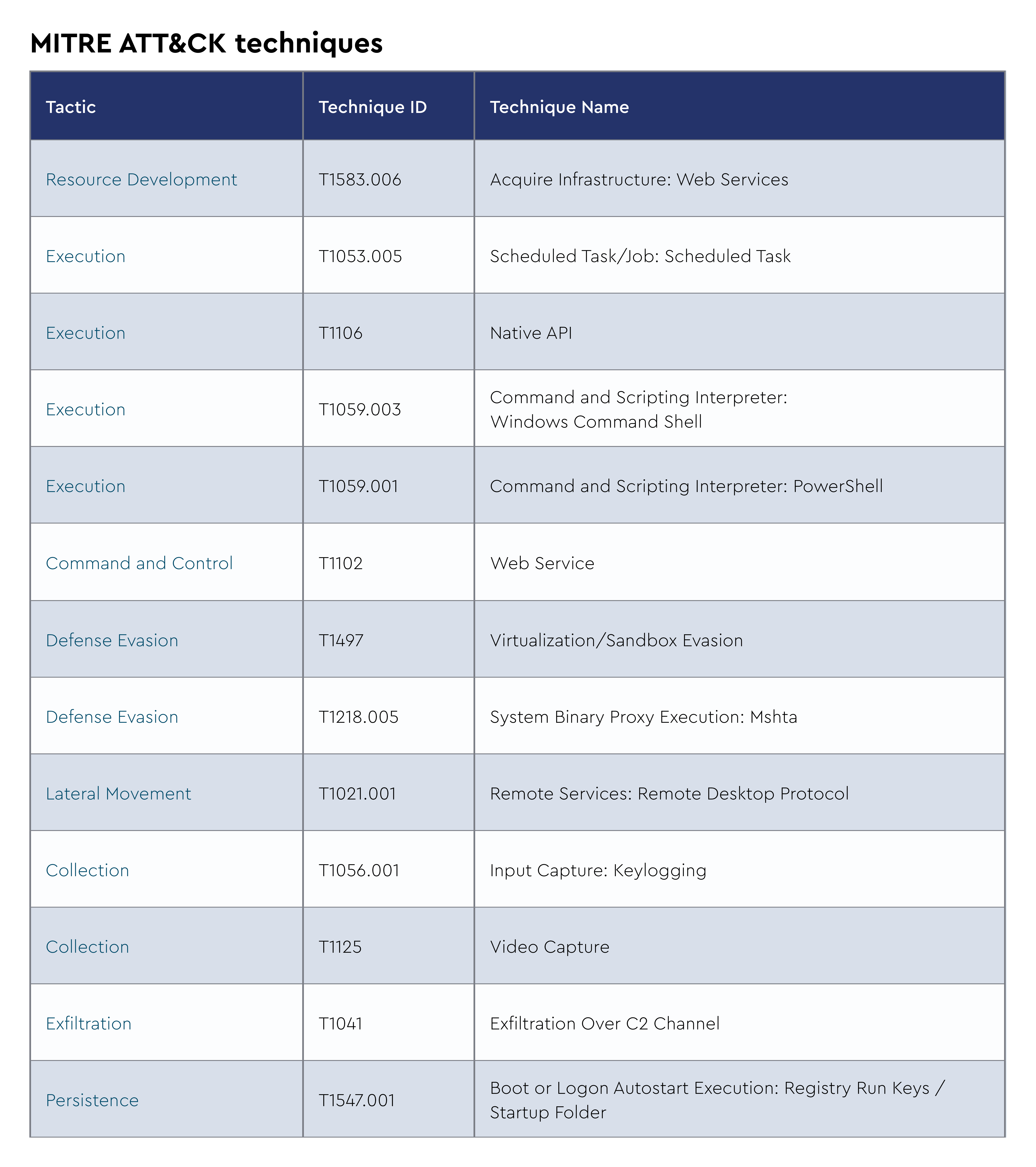
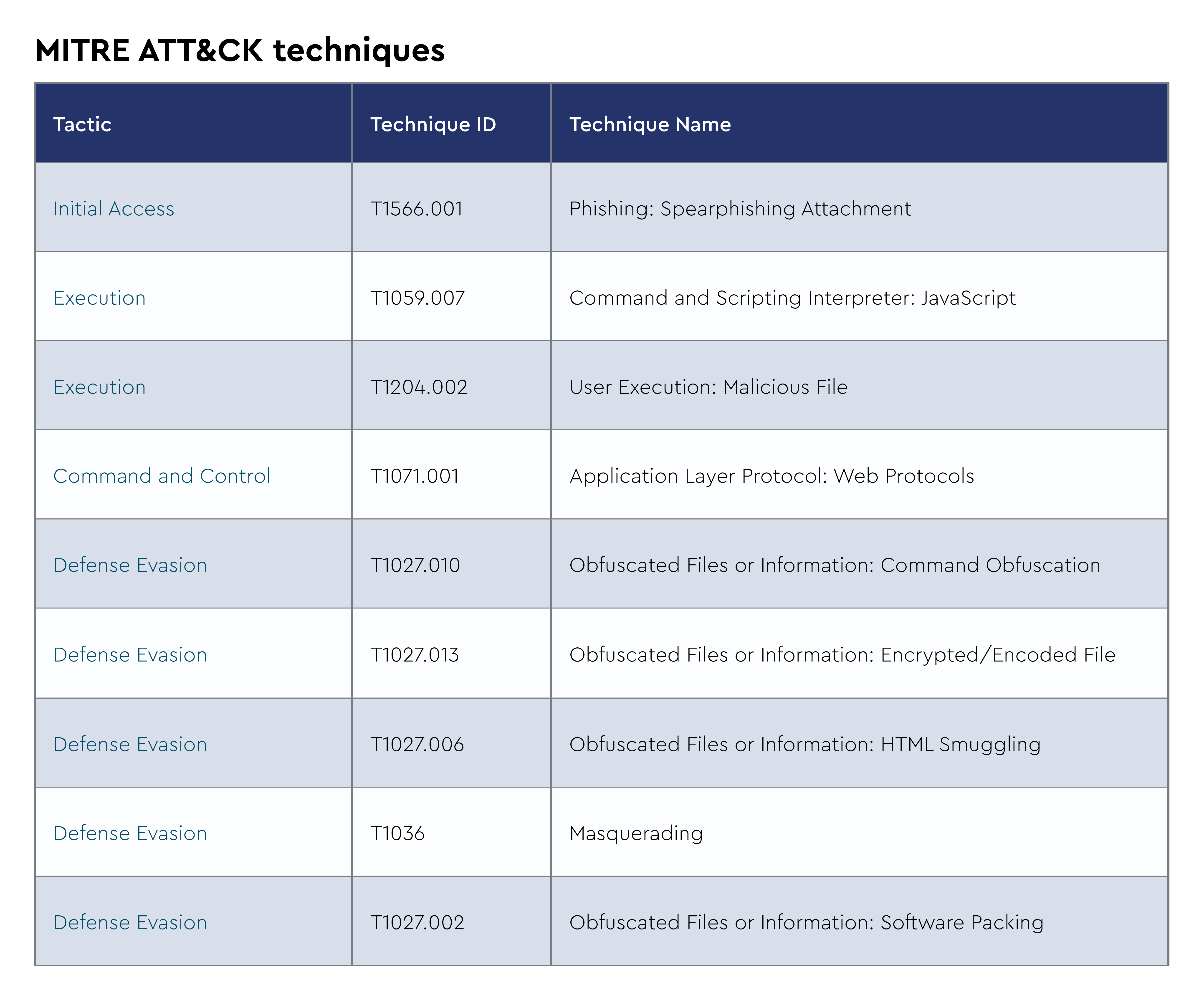
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for September 2024—provided for comparison—and October 2024.
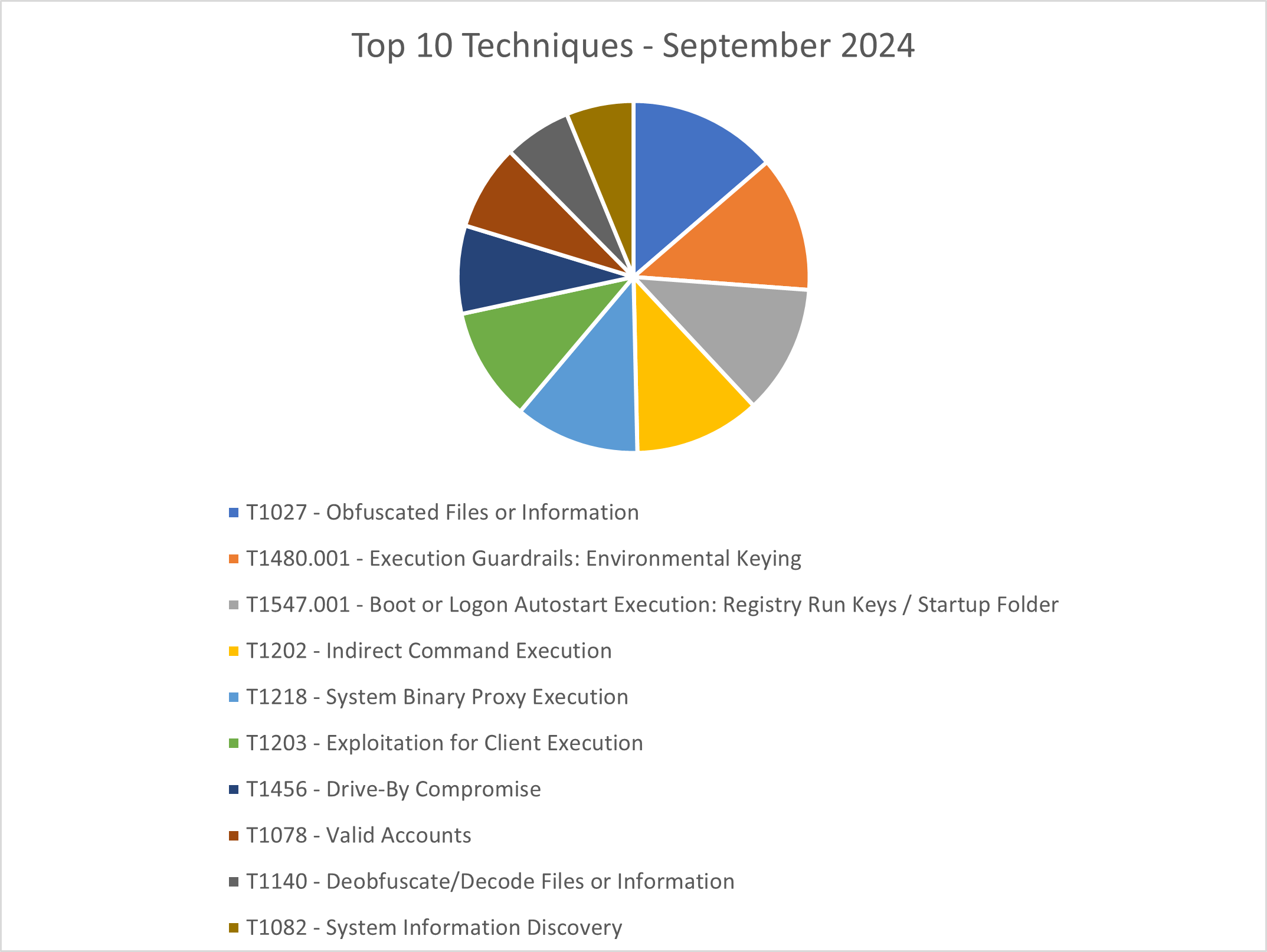
Figure 2: Top 10 MITRE ATT&CK techniques observed in September 2024
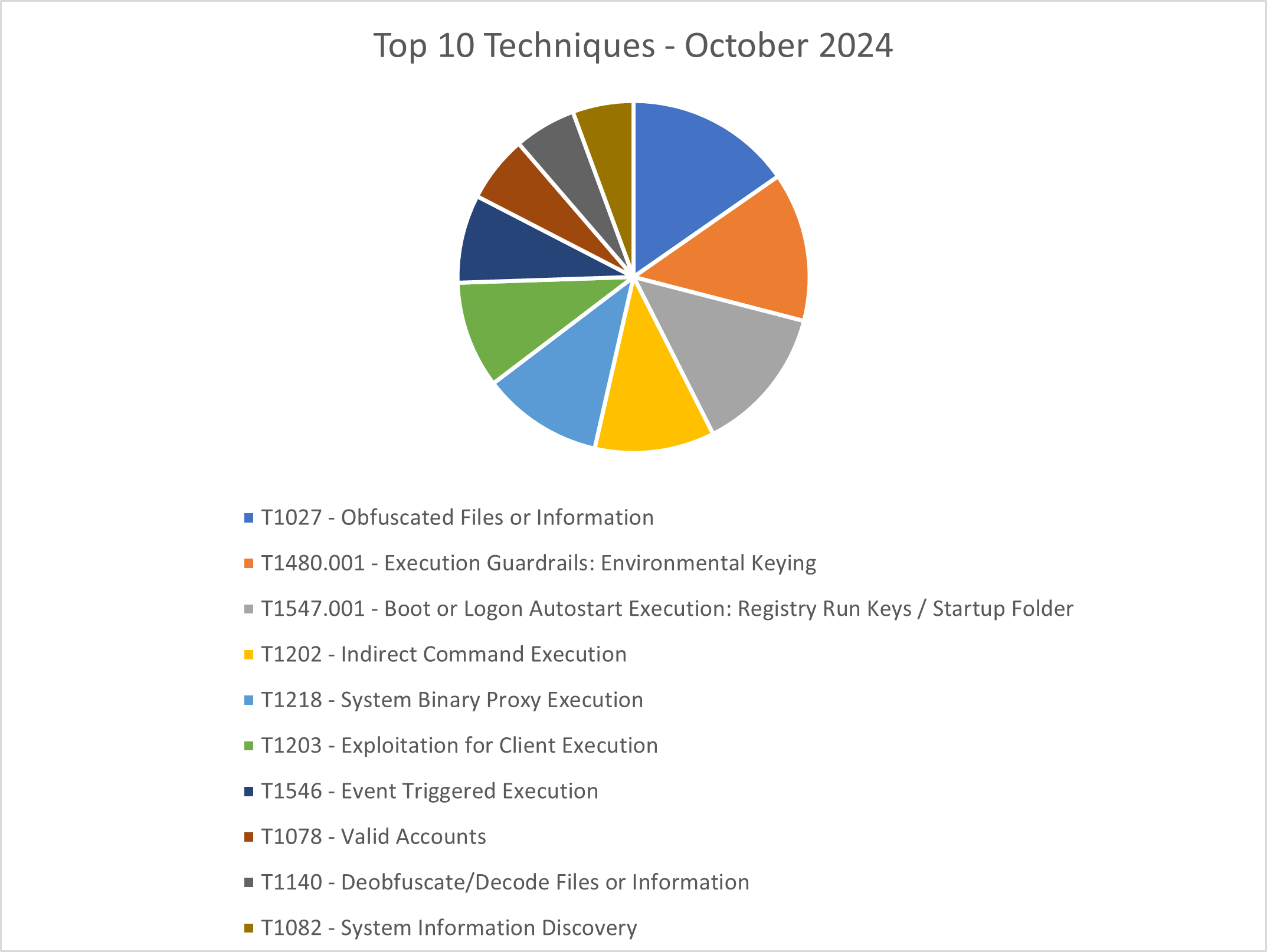
Figure 3: Top 10 MITRE ATT&CK techniques observed in October 2024
Latest threats
Each month, we highlight threats that we have seen targeting our managed service provider (MSP) partners and their clients.
Malware
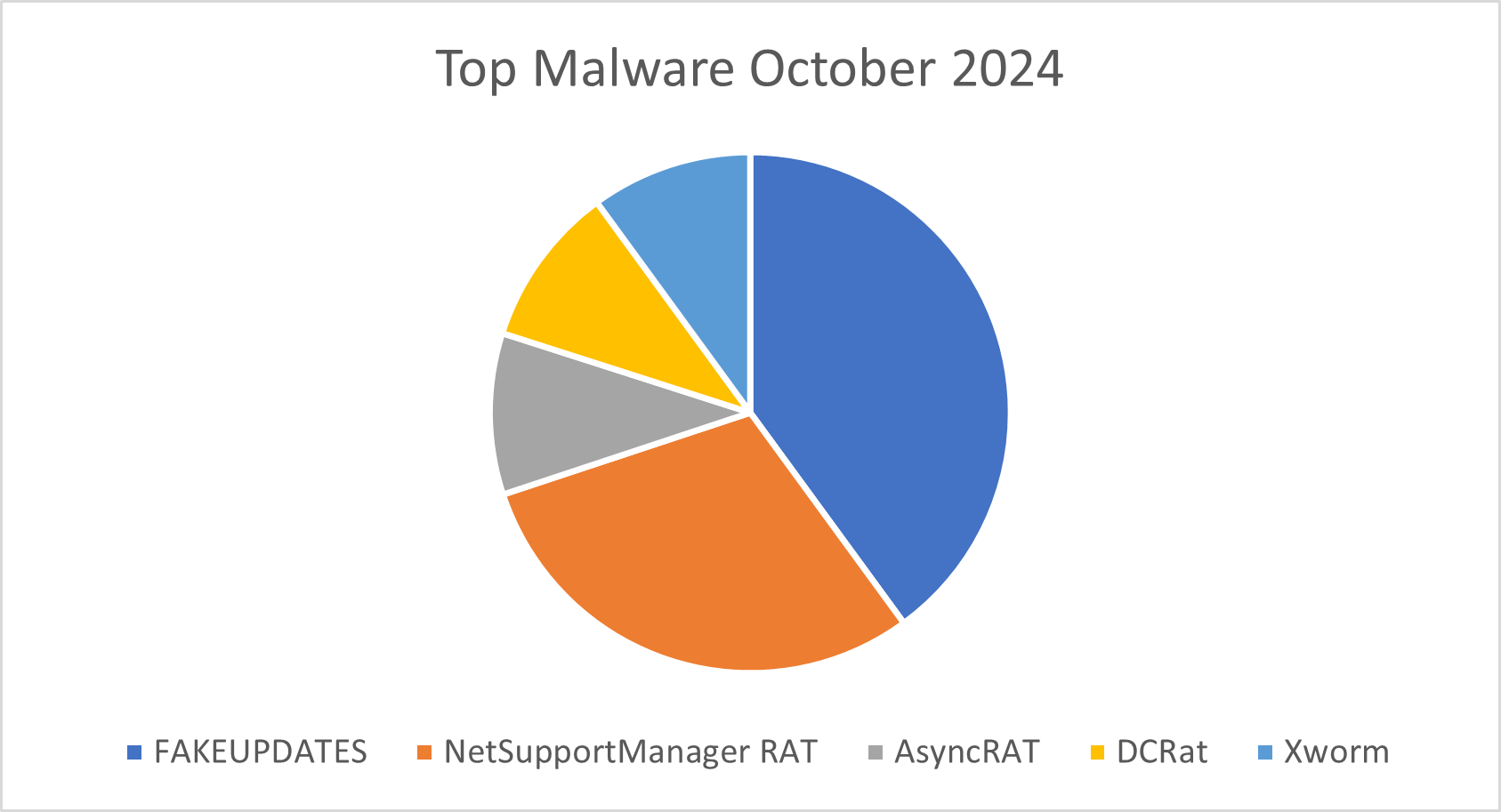
Figure 4: Top five malware observed in October 2024
FakeUpdates/SOCGholish
FakeUpdates, also known as SocGholish, is a prevalent malware campaign that emerged around 2018, characterized by its use of social engineering techniques to trick users into downloading malicious software disguised as legitimate updates. This malware is primarily delivered through compromised websites, where users are prompted with fake update notifications, typically for common software such as Adobe Flash Player or browser updates. These prompts are designed to appear authentic, exploiting user’s trust and urgency to keep their software up-to-date.
Once the user initiates the download, the malware installs a backdoor on the system, providing attackers with remote access and control. FakeUpdates is often used as a delivery mechanism for additional payloads, including ransomware, banking trojans, and information stealers. The attackers leverage this access to exfiltrate sensitive data, deploy further malware, or use the compromised systems for broader campaigns. The widespread use of compromised legitimate websites and the convincing nature of the fake update prompts make FakeUpdates a significant threat, capable of impacting a wide range of users and organizations. Its persistence and adaptability in evading detection underscore the importance of robust cybersecurity practices and user education to mitigate such threats.
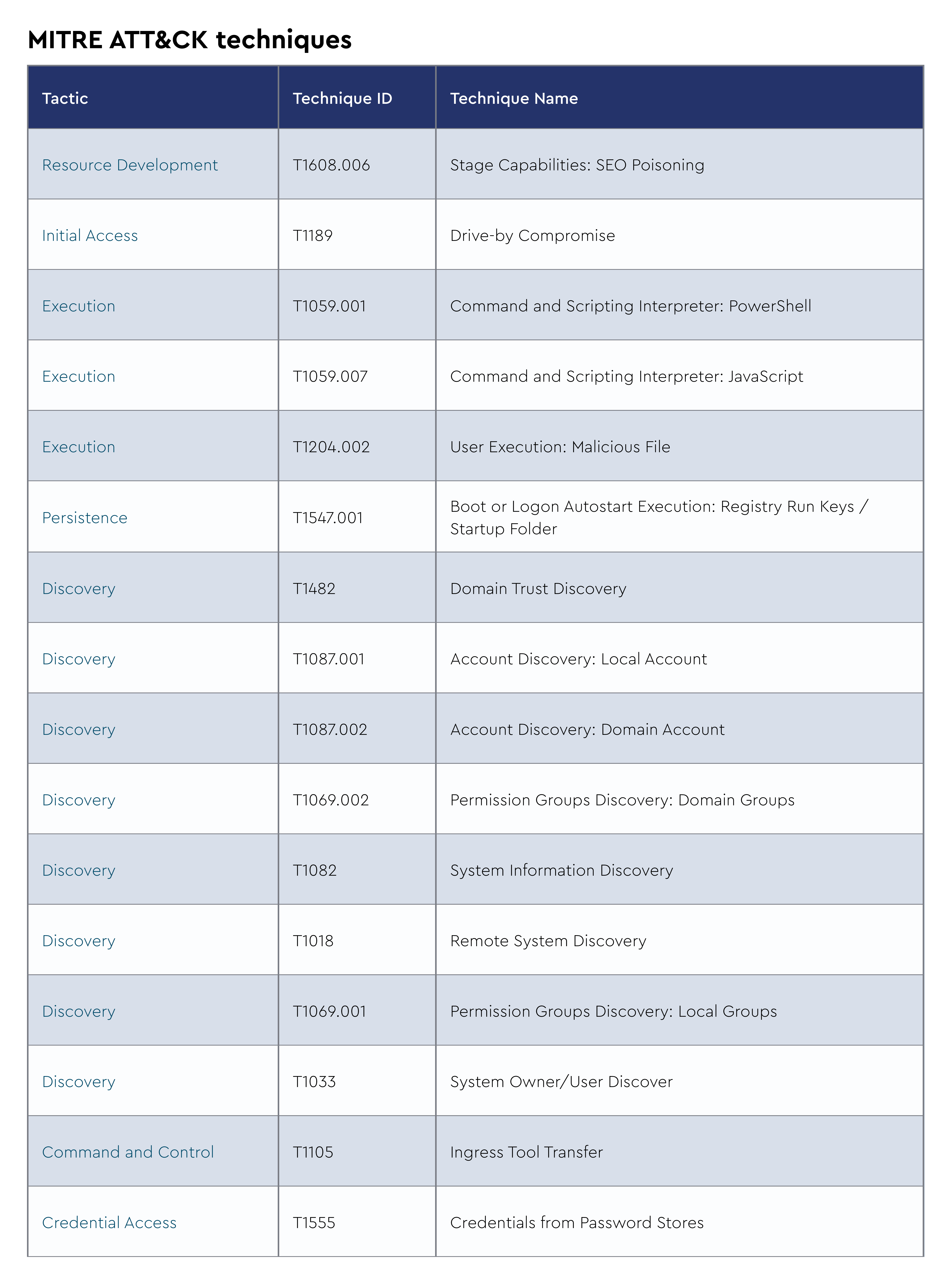
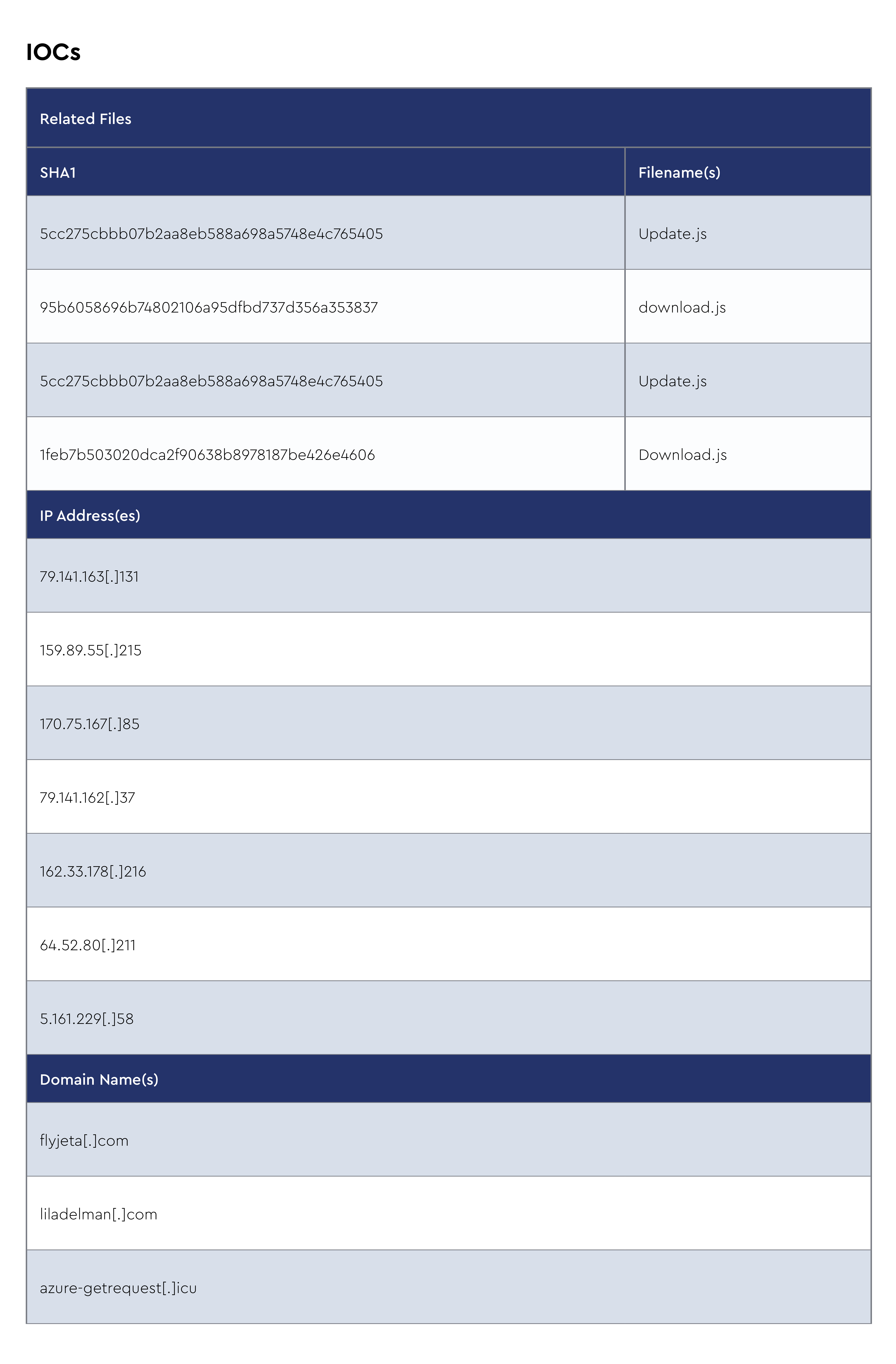
NetSupport Manager RAT
NetSupport Manager RAT is a program that enables users to manage and control other computers over a network. It functions as a “remote access trojan,” and while it’s intended for legitimate uses such as technical support and corporate network management, it can also be misused.
The software offers various features, such as:
- Remote desktop control: Gives an administrator full access to the target computer’s screen and inputs
- File transfer: Allows moving files between the computers
- System inventory: Provides details about the target computer’s hardware and software
- Hardware and software monitoring: Tracks system performance and installed applications
- Chat functionality: Facilitates communication between the administrator and the target computer user
NetSupport Manager RAT operates by installing a client component on the target computer and a control component on the administrator’s computer. These components communicate via a network connection, enabling the administrator to access and control the target computer. However, remote administration tools, including NetSupport Manager RAT, can be used for malicious purposes. Cybercriminals frequently use similar software to infiltrate computers, steal confidential information, or carry out harmful activities without the user’s knowledge or consent.
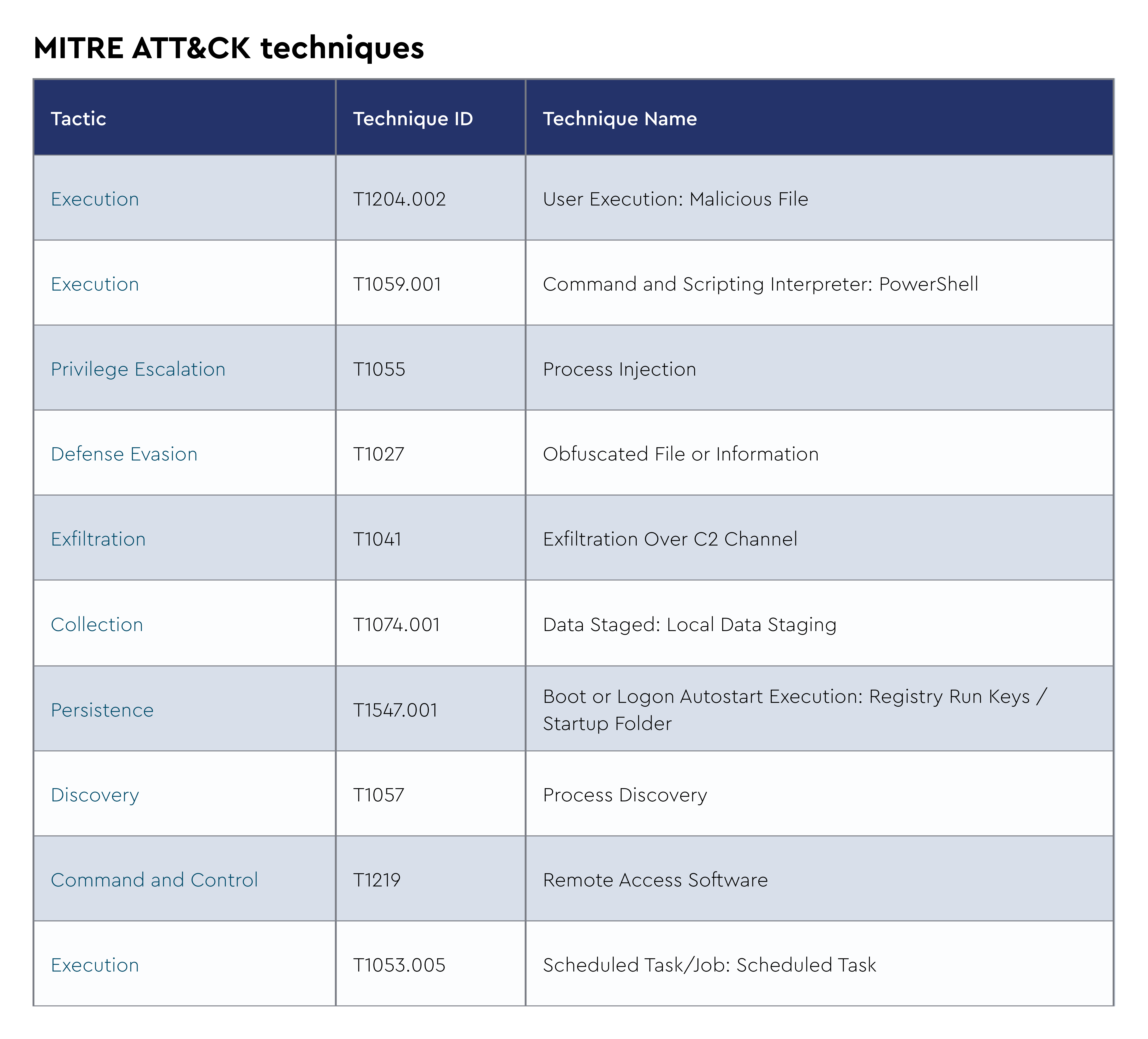
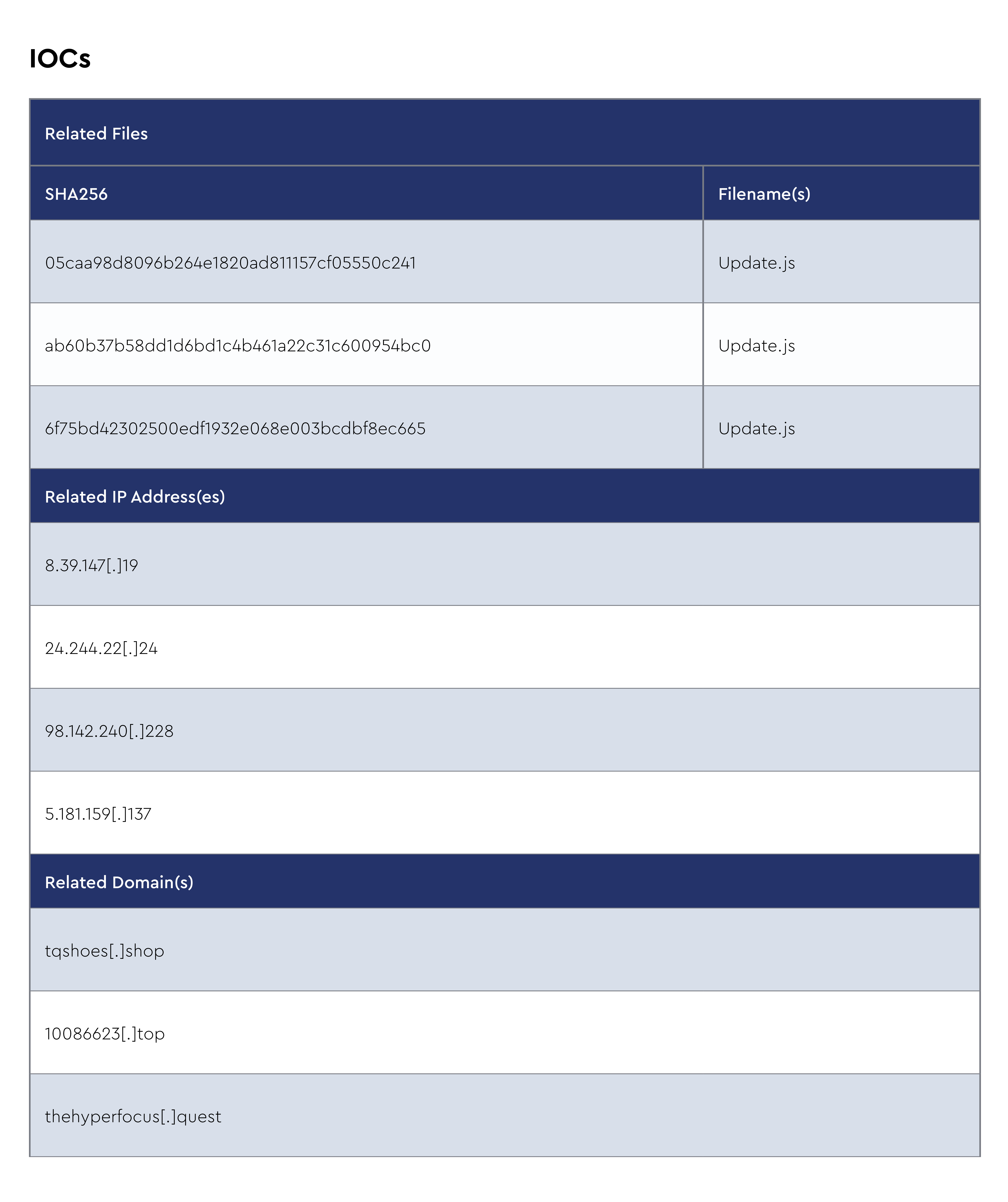
AsyncRAT
AsyncRAT is a remote access trojan (RAT) that allows unauthorized individuals to gain remote control over compromised computers. It is a versatile and powerful tool used by cybercriminals to carry out various malicious activities.
AsyncRAT provides a wide range of features, including remote desktop control, file management, keylogging, webcam and microphone access, and the ability to execute arbitrary commands on the compromised system. It can be distributed through various means, such as phishing emails, malicious downloads, or exploiting vulnerabilities in software.
Once a computer is infected with AsyncRAT, the attacker gains complete control over the compromised system, enabling them to steal sensitive information, install additional malware, or use the compromised machine as a launching pad for further attacks. The trojan is designed to remain undetected by antivirus software and employs techniques to evade detection and maintain persistence on the compromised system.
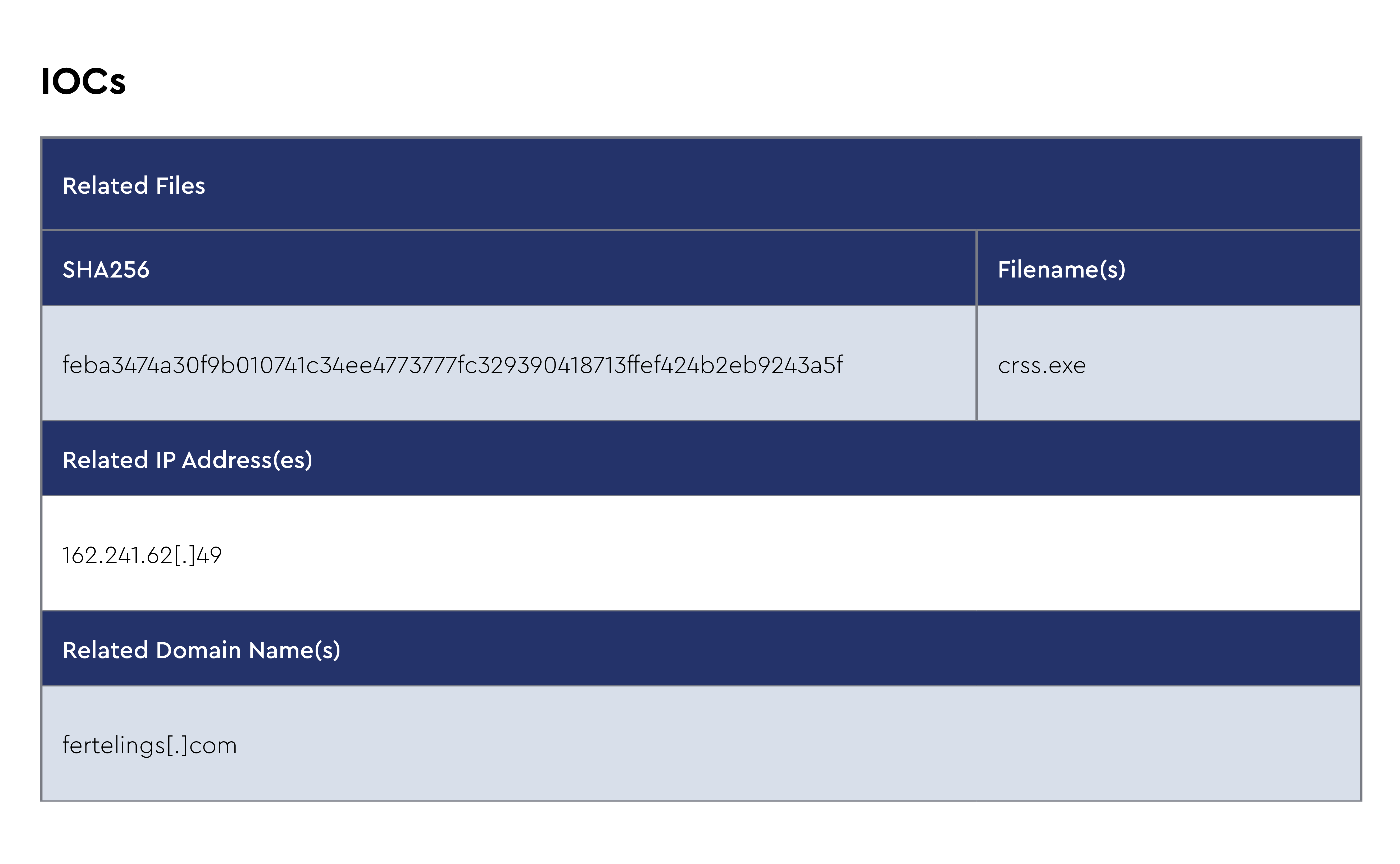
DCRat
DCRat, or Dark Crystal RAT, is a versatile and modular remote access trojan (RAT) that has been active since at least 2018. It enables cybercriminals to control infected systems, steal credentials, log keystrokes, execute shell commands, and exfiltrate files. Distributed as malware-as-a-service (MaaS), DCRat is popular with a broad spectrum of threat actors, making it a common tool in various cybercrime campaigns. Its recent evolution includes delivery through HTML smuggling, a technique that bypasses traditional security by embedding the malicious payload in HTML files. These files, mimicking Russian-language apps like VK Messenger, trick users into downloading a password-protected ZIP archive that ultimately installs DCRat.
Recent campaigns primarily target Russian-speaking users and employ sophisticated social engineering techniques to increase infection rates. The HTML smuggling approach, seen more commonly in 2024, allows DCRat to evade standard detection, as the malicious payloads are concealed within seemingly legitimate HTML files. This trend coincides with a broader adoption of generative AI by cybercriminals to create obfuscated scripts, enhancing the complexity and stealth of these attacks. Security professionals recommend enhanced monitoring of HTTP/HTTPS traffic, blocking known malicious domains, and reinforcing employee training to mitigate such evolving threats.
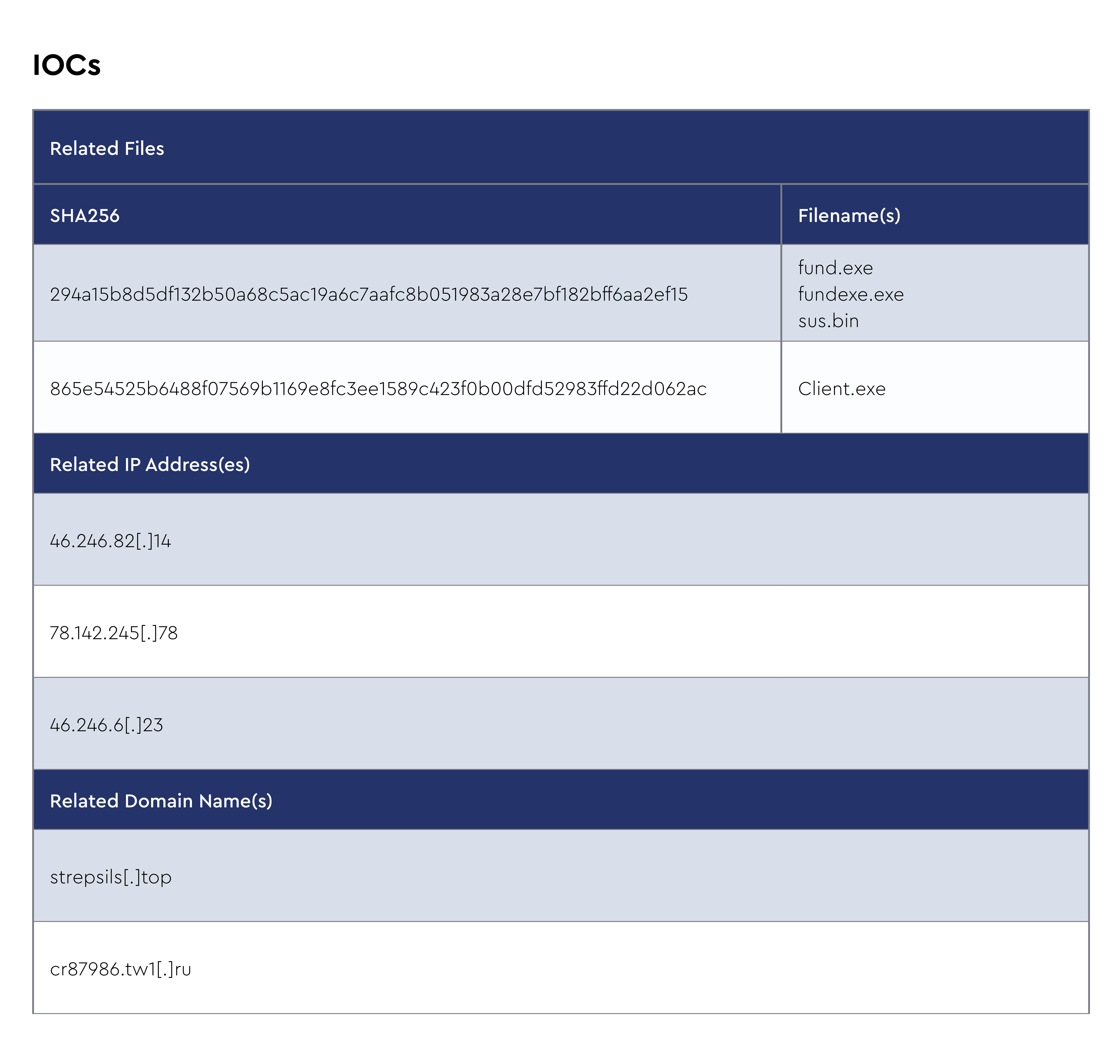
XWorm
XWorm is a remote access trojan (RAT) that has been gaining traction among cybercriminals due to its versatility and stealth. Distributed primarily through phishing emails and malicious attachments, XWorm enables attackers to take full control of an infected system. Once installed, it provides remote access, allowing for keylogging, screen capturing, data exfiltration, and the ability to run arbitrary commands. XWorm is lightweight, which makes it harder to detect, and is often obfuscated to avoid antivirus detection. It can spread laterally within a network, making it particularly dangerous for corporate environments.
Recent intelligence suggests that XWorm has been updated with additional functionalities, including more advanced evasion techniques and modular components that make it adaptable to various attack scenarios. Cybercriminals are increasingly using it in targeted attacks, often against organizations with weak email security controls. There have been reports of its use in financial sector attacks, where XWorm was deployed to steal credentials and banking information. Furthermore, the malware has been spotted in campaigns linked to both espionage and financial gain, indicating its growing popularity among different threat actors. Its evolving capabilities and widespread availability on underground forums make it a persistent and adaptable threat.
Monthly newsletter summary
The following is a summary of articles shared in the CRU newsletter during the month of October.
Ransomware Poses as IT Support in Microsoft Teams
Black Basta ransomware has recently started using Microsoft Teams to impersonate corporate IT support in their attacks. They create external Teams accounts with names that resemble legitimate help desks and initiate chat messages to assist employees with email spam issues. Their goal is to gain trust and convince targets to install remote access tools or enable screen sharing. Once connected, Black Basta deploys various payloads, including proxy malware called “AntispamConnectUS.exe,” to establish a persistent foothold on corporate systems. Their ultimate objective is to deploy Cobalt Strike for lateral movement, privilege escalation, data exfiltration, and eventually ransomware deployment. The group has also used QR codes in some Teams chats, possibly to bypass traditional email-based security defenses. To mitigate this threat, ReliaQuest recommends limiting external communication on Teams to known, verified domains for MSPs and businesses.
Thousands of WordPress sites Hosting Infostealers
A wave of cyberattacks has targeted over 6,000 WordPress websites, exploiting vulnerabilities in themes and plugins to install malicious plugins that deliver infostealer malware. These plugins allow attackers to steal sensitive data, including login credentials and cryptocurrency wallets, from visitors. The Raccoon Stealer malware is commonly used in these attacks, posing a significant risk to businesses and individuals by gathering personal data from various applications. Attackers focus on WordPress due to its widespread use, injecting backdoors into legitimate themes and plugins to maintain long-term access. Organizations are advised to monitor for compromise, update plugins regularly, and implement robust security measures. Vigilant patch management and proactive defenses are crucial as threat actors refine their methods to exploit vulnerabilities in common software.
SharePoint, OneDrive, and Dropbox used for Phishing Attacks
A recent report by Microsoft highlights a surge in phishing attacks that exploit legitimate file-hosting services such as SharePoint, OneDrive, and Dropbox for identity theft. Attackers are using these platforms to send phishing links disguised as genuine file-sharing notifications, bypassing security tools by leveraging trusted platforms. They compromise accounts at trusted vendors or partners to distribute notifications, convincing users to re-authenticate through seemingly legitimate file-sharing services. This allows attackers to steal session tokens and bypass multifactor authentication defenses. The social engineering techniques used in these phishing attempts are becoming more advanced, with time-sensitive restrictions on files and urgent requests to prompt users to click on malicious links. To mitigate these risks, organizations are advised to implement stronger security measures, enforce conditional access policies, transition to passwordless authentication, continuously monitor file-sharing services, and educate employees about phishing attempts.
New ConnectWise SIEM signatures
Several new ConnectWise SIEM detection signatures were added in October 2024. These include:
- [EA][CRU][Windows] Windows Defender settings changed via WMI
Techniques detected: [T1562.001] - Impair Defenses: Disable or Modify Tools
Description: Attackers have been observed adding exclusions and disabling functionality in Windows Defender. Changes through WMI are suspicious because, typically, the PowerShell functions specific to Defender are used.
- [EA][CRU][Windows] Powershell Executing dotNET Framework Binary Without Arguments
Techniques detected: [T1059.001] - Command and Scripting Interpreter: PowerShell
Description: This alert attempts to detect a PowerShell process injecting malicious code into .NET binaries. This pattern has been observed in malware incidents to execute subsequent stages and establish C2. https://www.trendmicro.com/en_us/research/23/l/analyzing-asyncrat-code-injection-into-aspnetcompiler-exe.html
- [EA][CRU][Windows] Suspicious Password Filter Activity
Techniques detected: [T1556.002] - Modify Authentication Process: Password Filter DLL, [T1547.001] - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
Description: This alert triggers when commands related to enabling a password filter in the “Notification Packages” registry path are executed. A threat actor may introduce a DLL into the environment and modify this registry key, which would cause the DLL instruction to be loaded into the LSASS process. Following the DLL registry activity, these reg commands would be entered, allowing an attacker to enumerate the existing password filters and modify the registry key to include the arbitrary password filter.
- [EA][CRU][Windows][LOLBAS] Makecab.exe abuse
Techniques detected: [T1560.001] - Archive Collected Data: Archive via Utility
Description: Makecab.exe is a Windows binary used to move existing files into a .cab file. Attackers have abused makecab.exe to copy malicious files to the ADS of an existing file and to download remote files. Surrounding activity and both the input and output files should be investigated.
- [CRU][Windows] Suspicious Process Masquerading as svchost
Techniques detected: [T1036] - Masquerading
Description: This detection identifies potential process masquerading attempts where malicious processes are disguising themselves as legitimate Windows system processes. Specifically, it looks for processes named “svhost.exe” or “scvhost.exe”, which are slight misspellings of the legitimate “svchost.exe” Windows process. This tactic has been used by threat actors, including groups like Storm-0501, to evade detection and blend in with normal system operations.
- [CRU][Windows] Potential Impacket atexec Execution Detected Via Scheduled Task
Techniques detected: [T1053] - Scheduled Task/Job
Description: This detection identifies the potential use of Impacket’s atexec.py tool for remote command execution via scheduled tasks. Atexec.py creates a temporary scheduled task on a remote system to execute commands, which can be used by attackers for lateral movement and remote code execution.
- [CRU][Windows] SQL Server Spawning CMD to Execute WMIC Commands
Techniques detected: [T1047] - Windows Management Instrumentation, [T1059.003] - Command and Scripting Interpreter: Windows Command Shell
Description: This detection identifies instances where the SQL Server spawns a command prompt (cmd.exe) to execute WMIC commands. This activity could indicate an attacker attempting to perform reconnaissance or execute malicious actions on the system using SQL Server’s elevated privileges.
- [CRU][Windows] Possible atexec.py Command Line Execution
Techniques detected: [T1053] - Scheduled Task/Jobe
Description: atexec.py is an Impacket collection module that can perform remote execution via scheduled tasks. This detection attempts to trigger on this activity by matching on command line patterns commonly observed on target machines.





