Monthly Threat Brief: September 2024
Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU). In this threat brief, we will provide raw data statistics, intel on specific threats, and a list of new detection signatures added to the ConnectWise SIEM™ throughout the month of September.
For a more detailed explanation of the overall trends and analysis of these numbers, check out the 2024 MSP Threat Report. For comparison, August’s threat brief can be found here.
September 2024 stats
IOCs
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected.
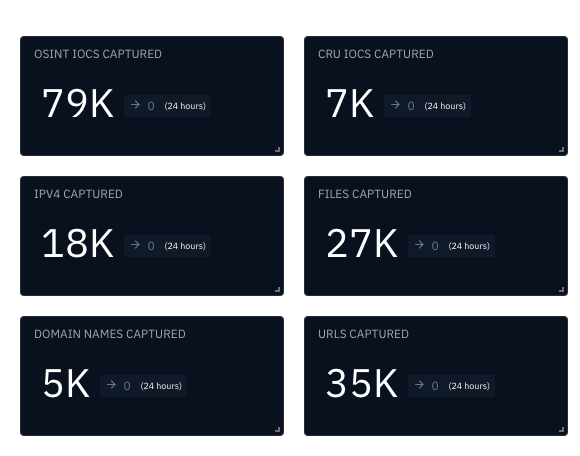
Figure 1: Summary of IOCs collected in September 2024
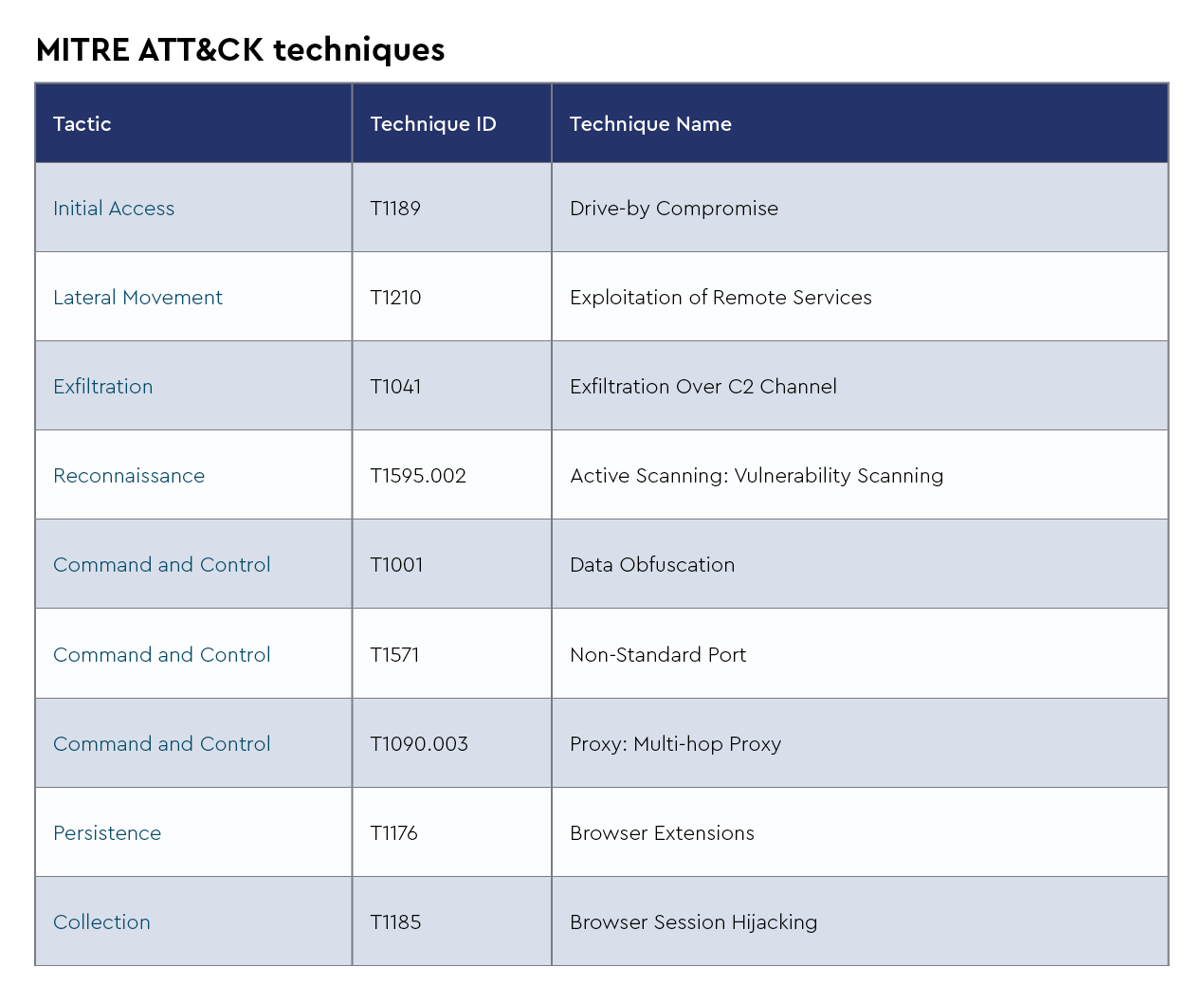
TTPs
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for August 2024—provided for comparison—and September 2024.
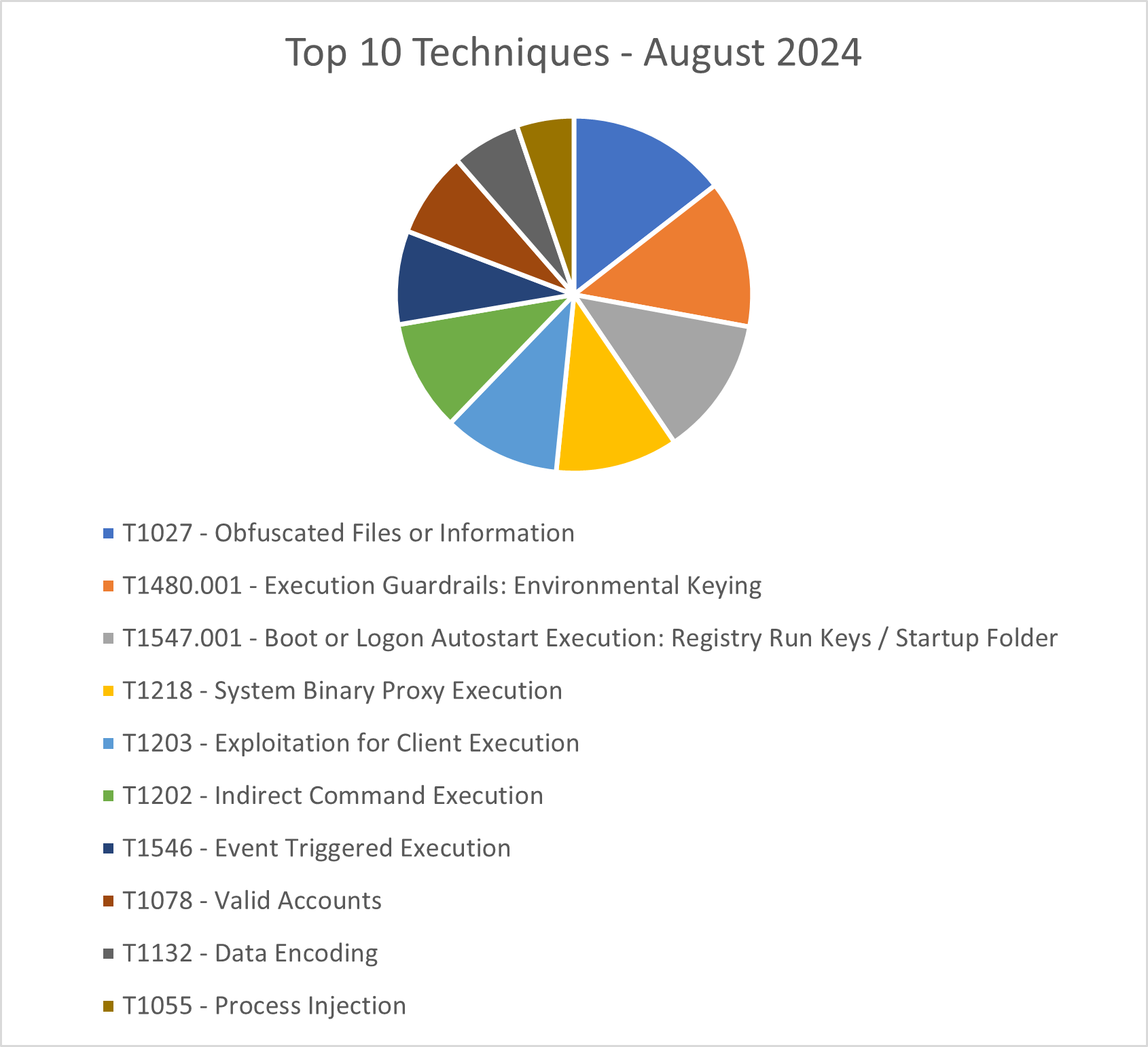
Figure 2: Top 10 MITRE ATT&CK techniques observed in August 2024
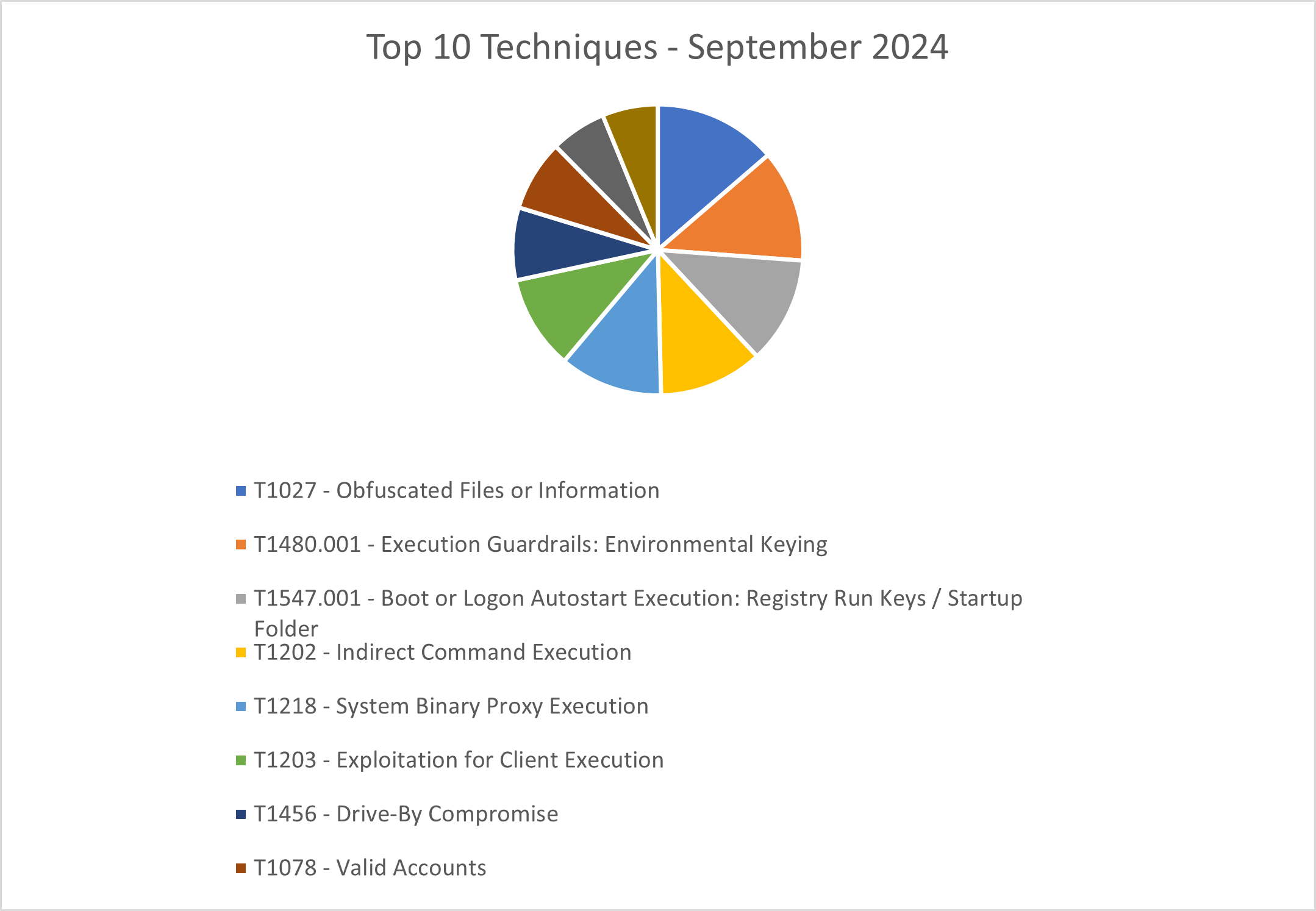
Figure 3: Top 10 MITRE ATT&CK techniques observed in September 2024
Latest threats
Each month, we highlight threats that we have seen targeting our managed service provider (MSP) partners and their clients.
Malware
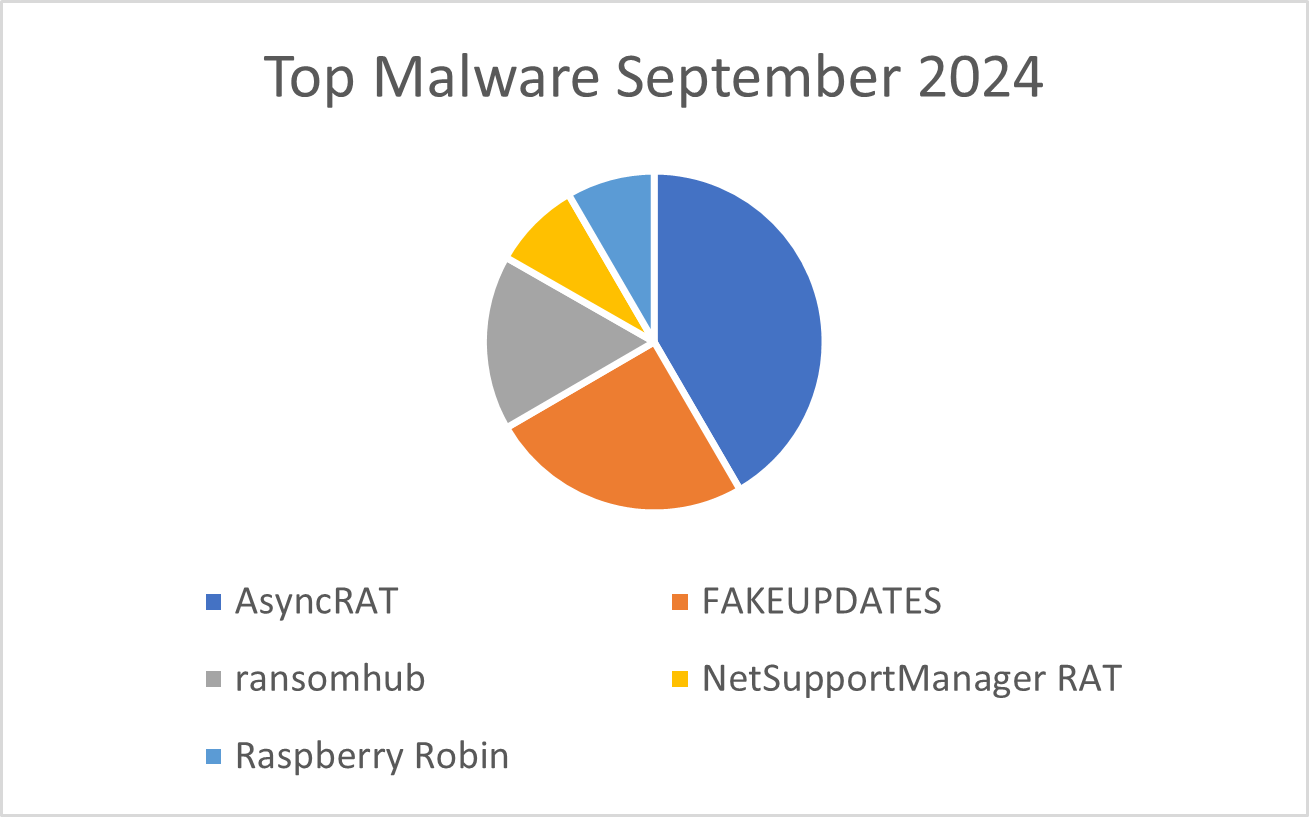
Figure 4: Top five malware observed in September 2024
AsyncRAT
AsyncRAT is a remote access trojan (RAT) that allows unauthorized individuals to gain remote control over compromised computers. It is a versatile and powerful tool used by cybercriminals to carry out various malicious activities.
AsyncRAT provides a wide range of features, including remote desktop control, file management, keylogging, webcam and microphone access, and the ability to execute arbitrary commands on the compromised system. It can be distributed through various means, such as phishing emails, malicious downloads, or exploiting vulnerabilities in software.
Once a computer is infected with AsyncRAT, the attacker gains complete control over the compromised system, enabling them to steal sensitive information, install additional malware, or use the compromised machine as a launching pad for further attacks. The trojan is designed to remain undetected by antivirus software and employs techniques to evade detection and maintain persistence on the compromised system.
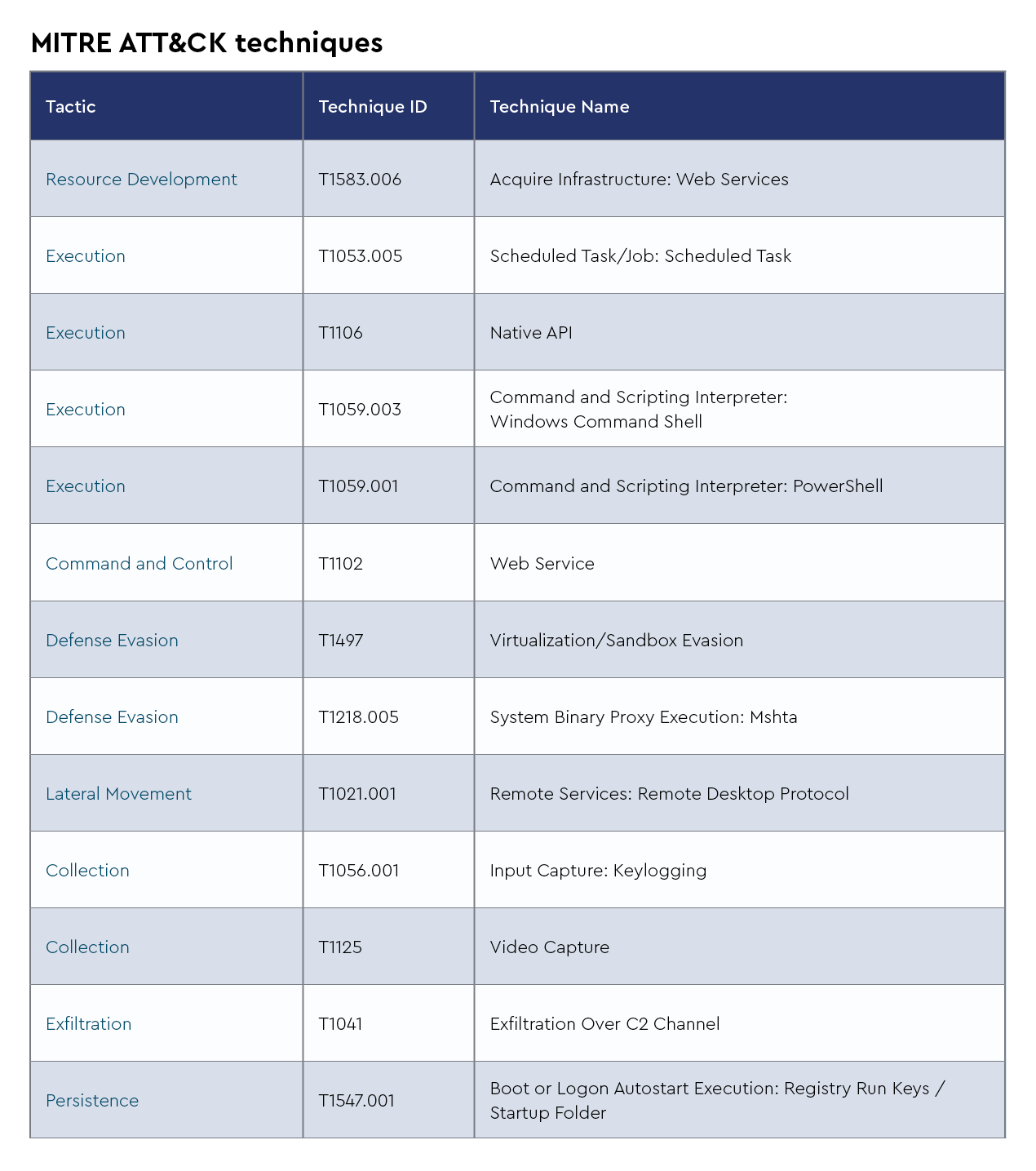
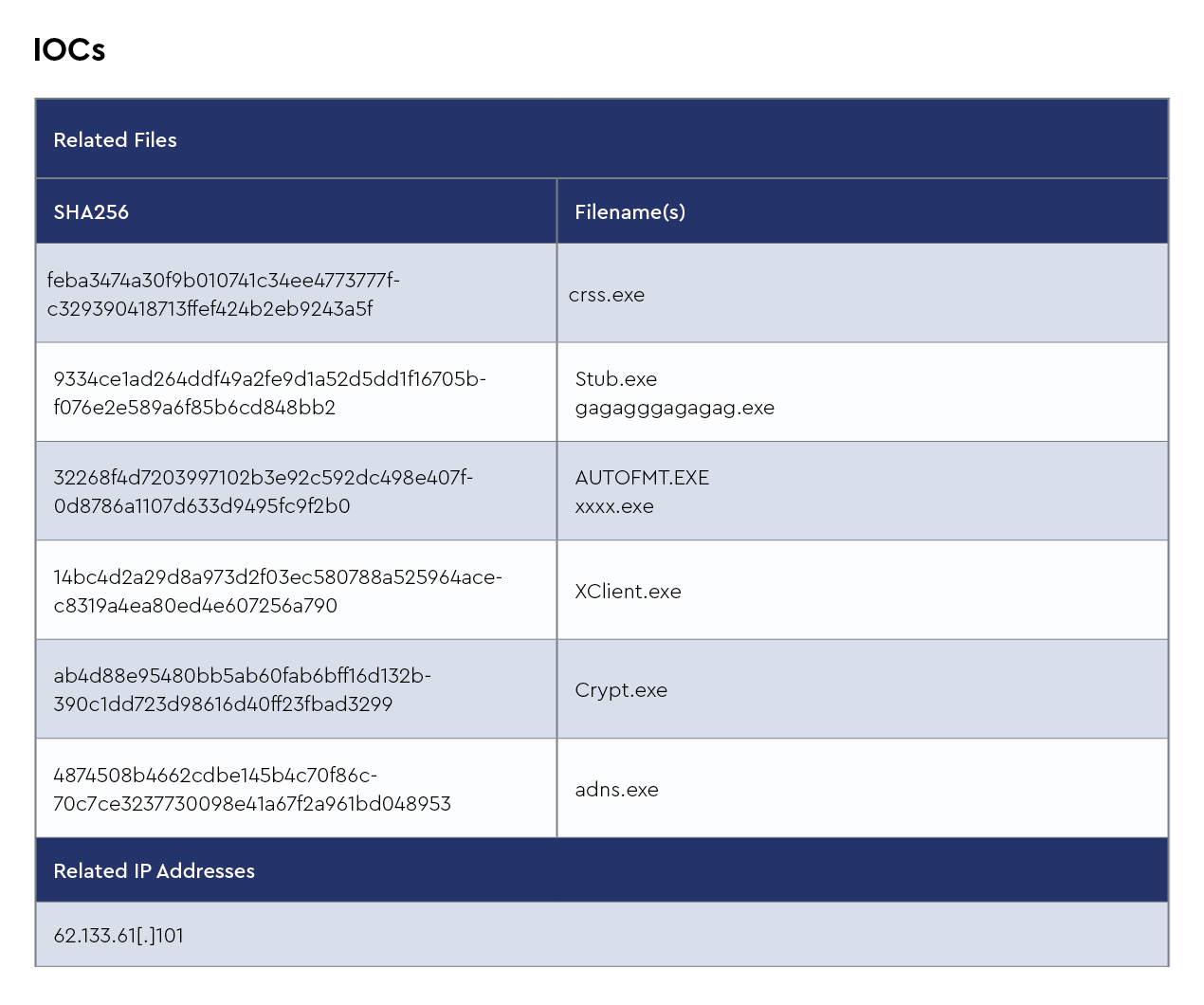
FAKEUPDATES/FakeUpdates
FakeUpdates, also known as SocGholish, is a prevalent malware campaign that emerged around 2018, characterized by its use of social engineering techniques to trick users into downloading malicious software disguised as legitimate updates. This malware is primarily delivered through compromised websites, where users are prompted with fake update notifications, typically for common software such as Adobe Flash Player or browser updates. These prompts are designed to appear authentic, exploiting users’ trust and urgency to keep their software up-to-date.
Once the user initiates the download, the malware installs a backdoor on the system, providing attackers with remote access and control. FakeUpdates is often used as a delivery mechanism for additional payloads, including ransomware, banking trojans, and information stealers. The attackers leverage this access to exfiltrate sensitive data, deploy further malware, or use the compromised systems for broader campaigns.
The widespread use of compromised legitimate websites and the convincing nature of the fake update prompts make FakeUpdates a significant threat, capable of impacting a wide range of users and organizations. Its persistence and adaptability in evading detection underscore the importance of robust cybersecurity practices and user education to mitigate such threats.
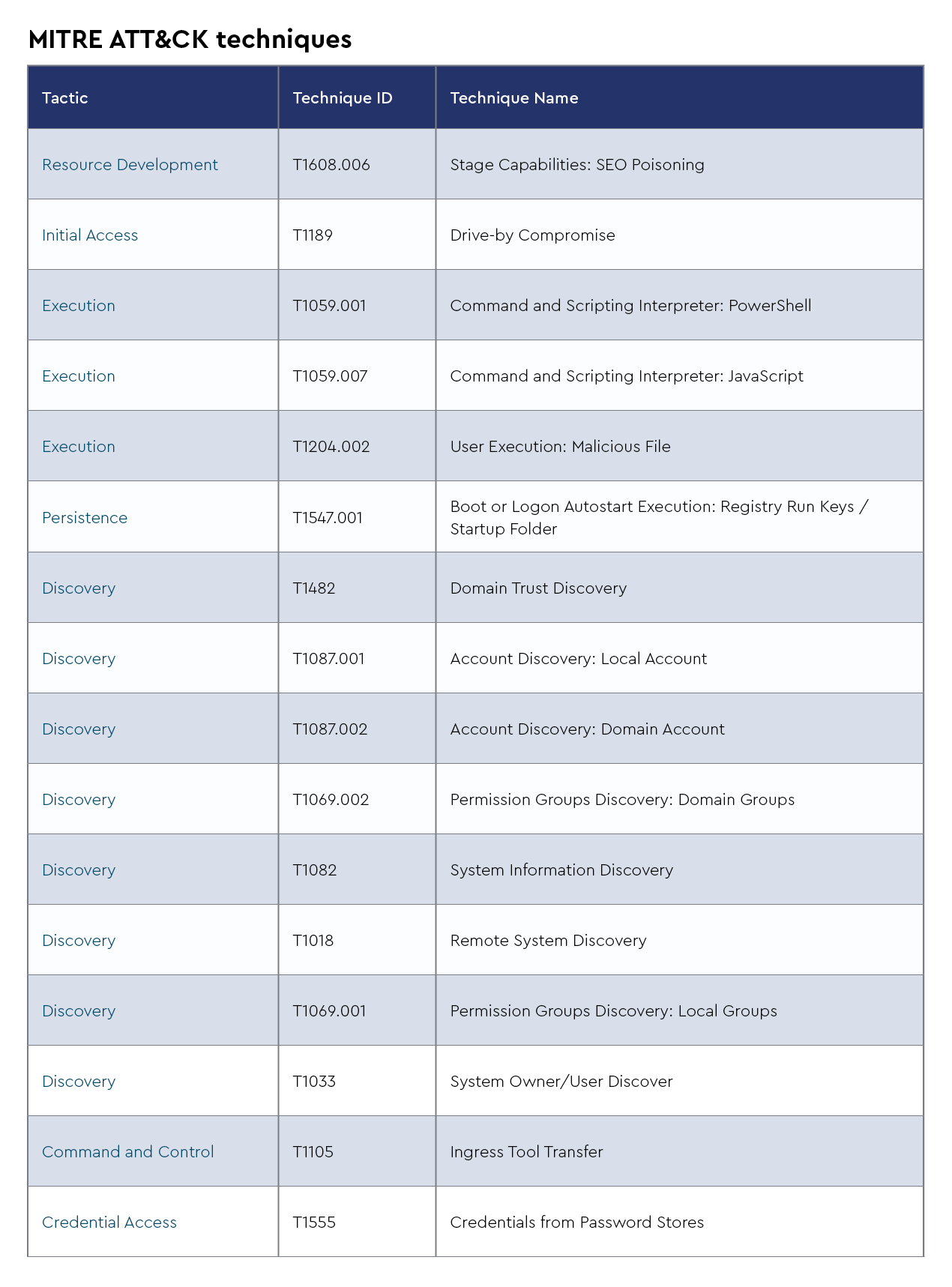
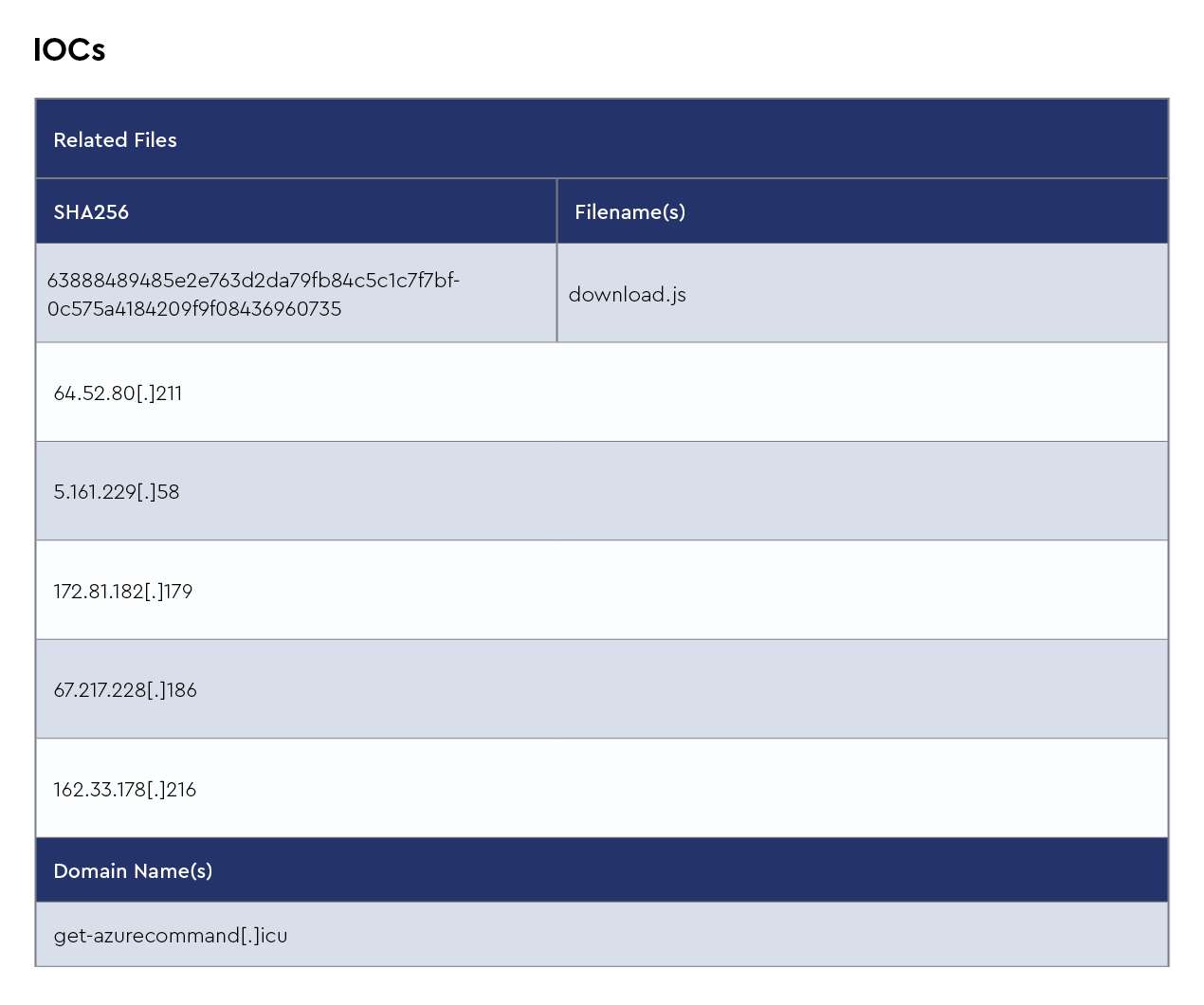
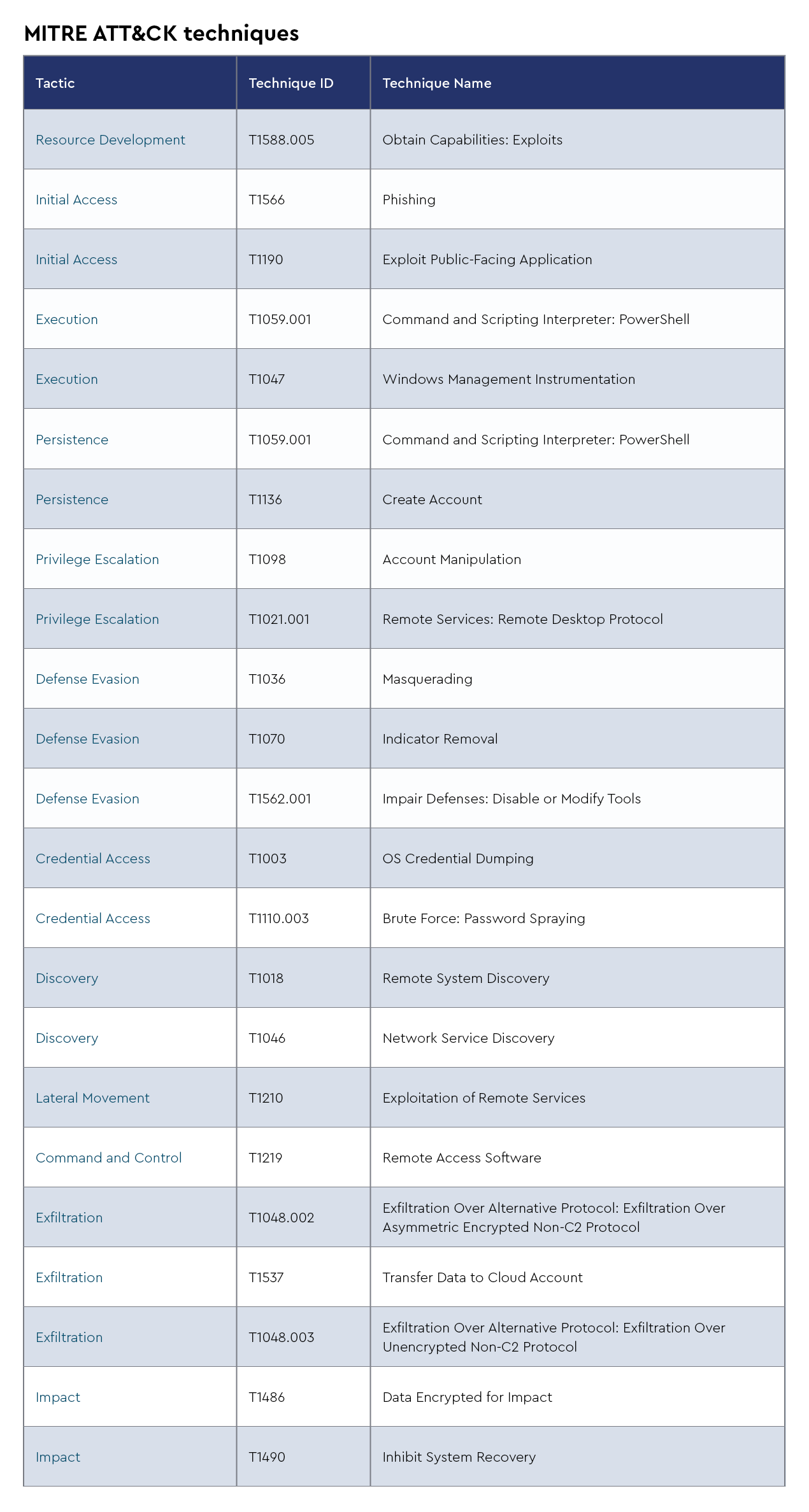
Ransomhub
RansomHub is a relatively new and growing ransomware-as-a-service (RaaS) platform that provides tools and infrastructure for cybercriminals to launch ransomware attacks. Similar to other RaaS groups, RansomHub operates by recruiting affiliates who carry out the attacks, while the core group focuses on developing and refining the ransomware software. Affiliates are given access to ransomware payloads, communication platforms, and negotiation tools to demand ransom from victims. The group typically targets corporate networks and critical infrastructure, leveraging double extortion tactics—encrypting data and threatening to release it publicly if ransoms are not paid.
Recent intelligence suggests that RansomHub has been ramping up its operations, with more sophisticated techniques emerging. They've been linked to using advanced evasion techniques, including encryption schemes that make payload detection harder, and exploiting zero-day vulnerabilities to breach networks. Recent activity indicates a shift in focus towards critical sectors such as healthcare and financial institutions, suggesting that the group is targeting organizations likely to pay larger ransoms. There's also speculation that RansomHub is experimenting with supply chain attacks to increase its impact radius, a concerning trend in recent ransomware operations. CISA recently released an advisory concerning this growing threat.
NetSupportManager RAT
NetSupportManager RAT is a program that enables users to manage and control other computers over a network. It functions as a remote access trojan (RAT), and while it's intended for legitimate uses such as technical support and corporate network management, it can also be misused.
The software offers various features, such as:
- Remote desktop control: Gives an administrator full access to the target computer's screen and inputs
- File transfer: Allows moving files between the computers
- System inventory: Provides details about the target computer's hardware and software
- Hardware and software monitoring: Tracks system performance and installed applications
- Chat functionality: Facilitates communication between the administrator and the target computer user
NetSupportManager RAT operates by installing a client component on the target computer and a control component on the administrator's computer. These components communicate via a network connection, enabling the administrator to access and control the target computer. However, remote administration tools, including NetSupportManager RAT, can be used for malicious purposes. Cybercriminals frequently use similar software to infiltrate computers, steal confidential information, or carry out harmful activities without the user's knowledge or consent.
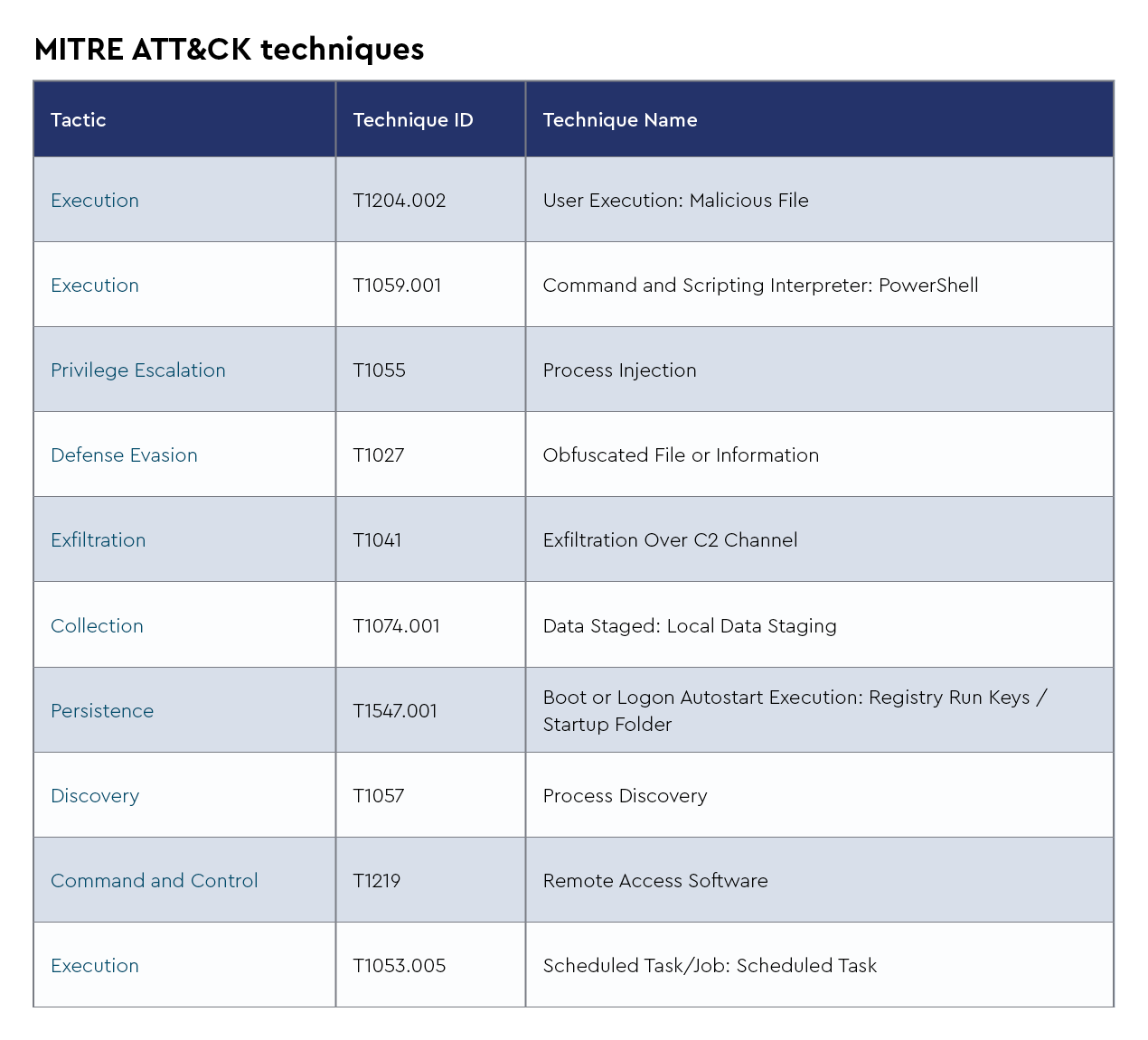
Raspberry Robin
Raspberry Robin, first identified in 2021, is a rapidly evolving malware that initially spread through infected USB drives. It acts as a key initial access facilitator for ransomware operations and other malicious payloads. In 2024, Raspberry Robin's operators, attributed to the group Storm-0856, began exploiting one-day vulnerabilities such as CVE-2023-36802 and CVE-2023-29360 within weeks of public disclosure, likely sourcing these exploits from dark web markets. The malware has adapted to use new evasion techniques, including leveraging PAExec for lateral movement and Tor-based command-and-control communications. It has also expanded its infection vectors by distributing malicious RAR archives through platforms like Discord.

Monthly newsletter summary
The following is a summary of articles shared in the CRU newsletter during the month of September.
Spoofed GlobalProtect VPN Exploitation
A new wave of cyberattacks is targeting MSPs and their clients by exploiting fake GlobalProtect VPN portals using SEO poisoning. These fraudulent portals are used to distribute WikiLoader, a sophisticated malware loader, posing a significant threat to organizations relying on VPNs for secure remote access. Once installed, WikiLoader allows attackers to execute secondary payloads, including data exfiltration tools, ransomware, or other advanced persistent threats. The loader's stealth capabilities make it difficult to detect, enabling attackers to maintain persistence within networks without triggering security alerts. MSPs are advised to educate clients about the risks, update VPN software regularly, enable two-factor authentication, and monitor VPN logs for unusual activity. It is crucial for individuals and organizations to exercise caution when accessing websites or downloading software to reduce the risk of falling victim to malware and ensure digital security.
Ransomware Surge: An MSP Call to Action
Ransomware attacks are increasing in frequency and sophistication, and many MSPs are still falling victim despite being aware of the threat. To address this disconnect, MSPs need to take a proactive and aggressive stance against ransomware. This involves fortifying clients' networks with multiple layers of protection, including perimeter security, endpoint security, network security, data security, system hardening, and multi-factor authentication. MSPs should also prioritize security awareness training, implement proactive security measures, invest in their teams' education, communicate with clients about risks, and partner with trusted security providers. By taking these steps, MSPs can enhance their security posture, reduce the risk of attack, and protect clients' data and systems from ransomware and data exfiltration.
Microsoft's Patch Tuesday for this month addressed 79 vulnerabilities, including four zero-day vulnerabilities that were being actively exploited. One of the zero-day vulnerabilities is an elevation of privilege vulnerability in Windows Installer, which could allow attackers to gain SYSTEM-level privileges. Another vulnerability affects Microsoft Publisher and allows macro execution via a malicious document, bypassing Office macro policies. There is also a remote code execution vulnerability in Windows updates that only affects certain versions of Windows 10, allowing attackers to roll back previously patched vulnerabilities. Additionally, there are patches for Mark-of-the-Web bypasses, vulnerabilities in Microsoft SharePoint Server, Windows networking internals, MSHTML spoofing, and several elevation of privilege vulnerabilities affecting various system components.
PoC Released for Critical RCE Vulnerability in Ivanti Endpoint Manager
A critical remote code execution vulnerability (CVE-2024-29847) affecting Ivanti endpoint manager has been actively exploited. The flaw allows attackers to execute arbitrary code through insecure deserialization of untrusted data in the deprecated Microsoft .NET Remoting framework used by the Ivanti AgentPortal.exe service. Attackers can inject a malicious object into the communication process and gain control over file operations on the server. With a proof-of-concept exploit now available, organizations using Ivanti endpoint manager are at heightened risk, emphasizing the importance of patching and proactive security measures. This vulnerability adds to a series of attacks on Ivanti's products, highlighting the need for timely response strategies and patch management.
QDoor: A New Backdoor Tool in Blacksuit's Arsenal
The CRU recently reviewed a ransomware incident involving a new network tunneling backdoor called QDoor, used by the Blacksuit ransomware operators. QDoor is written using statically compiled Qt networking libraries and was found alongside the Blacksuit encryptor in the C:\Windows\SYSVOL directory during the incident. The backdoor collects system information and connects to a command and control (C2) server for communication. It responds to heartbeat commands and can establish connections with specified IP addresses and ports. The backdoor proxies traffic between the C2 and the target IP. Multiple QDoor samples have been observed, and IOCs and detection rules have been provided for analysis and mitigation purposes.
New ConnectWise SIEM signatures
Several new ConnectWise SIEM detection signatures were added in September 2024. These include:
- [EA][Windows] Suspicious scheduled task created - temp directory
Techniques detected: [T1203] Exploitation for Client Execution
Description: Scheduled tasks are a common form of persistence. Malicious actors have been observed using scheduled tasks to execute malicious files as well as writing output files in temp directories.
- [CRU][Windows] FSUTIL Symbolic Link Set
Techniques detected: [T1059] Command and Scripting Interpreter
Description: This alert triggers when FSUTLI is used to enable remote-to-local or remote-to-remote symbolic links. Symbolic links can point to local targets, remote targets, or both. An actor might try to use this technique to allow the redirection of links to tools or resources from a remote source.
- [EA][CRU][Windows] Windows Defender Exclusion Set
Techniques detected: [T1070] Indicator Removal
Description: Add-MpPreference, Set-MpPreference, and reg.exe can be used by attackers to add exclusions to Windows Defender. All activity should be verified for authorization. Suspicious executables or exclusions made in suspicious directories, such as temp folders, should be investigated further for system compromise.
- [CRU][Windows] Command Processor AutoRun Registry Alteration
Techniques detected: [T1112] Modify Registry
Description: This alert triggers when an AutoRun value is added, removed, or changed within the registry path HKEY_LOCAL_MACHINE\Software\Microsoft\Command Processor and HKEY_CURRENT_USER\Software\Microsoft\Command Processor. Designating a value to this key causes the value to be executed whenever the command prompt is started. Pay attention to the value that is designated and suspicious activity following this event.
- [EA][CRU][Windows] Suspicious Policy Modifications
Techniques detected: [T1484.001] Domain or Tenant Policy Modification: Group Policy Modification
Description: These rules check for policy modifications in PowerShell script block logs and process command line for System—DisableTaskMgr, DisableCMD, and DisableRegistryTools—and Explorer— NoRun, HidePowerOptions, DisableNotificationCenter. Modifications could be attributed to malicious executables attempting to hide or impair defenses from detecting the malicious processes.








