Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU).
In this threat brief, we will provide raw data statistics, intel on specific threats, and a list of new detection signatures added to the ConnectWise SIEM™ throughout the month of August.
For a more detailed explanation of the overall trends and analysis of these numbers, check out the 2024 MSP Threat Report. For comparison, July’s threat brief can be found here.
August 2024 stats
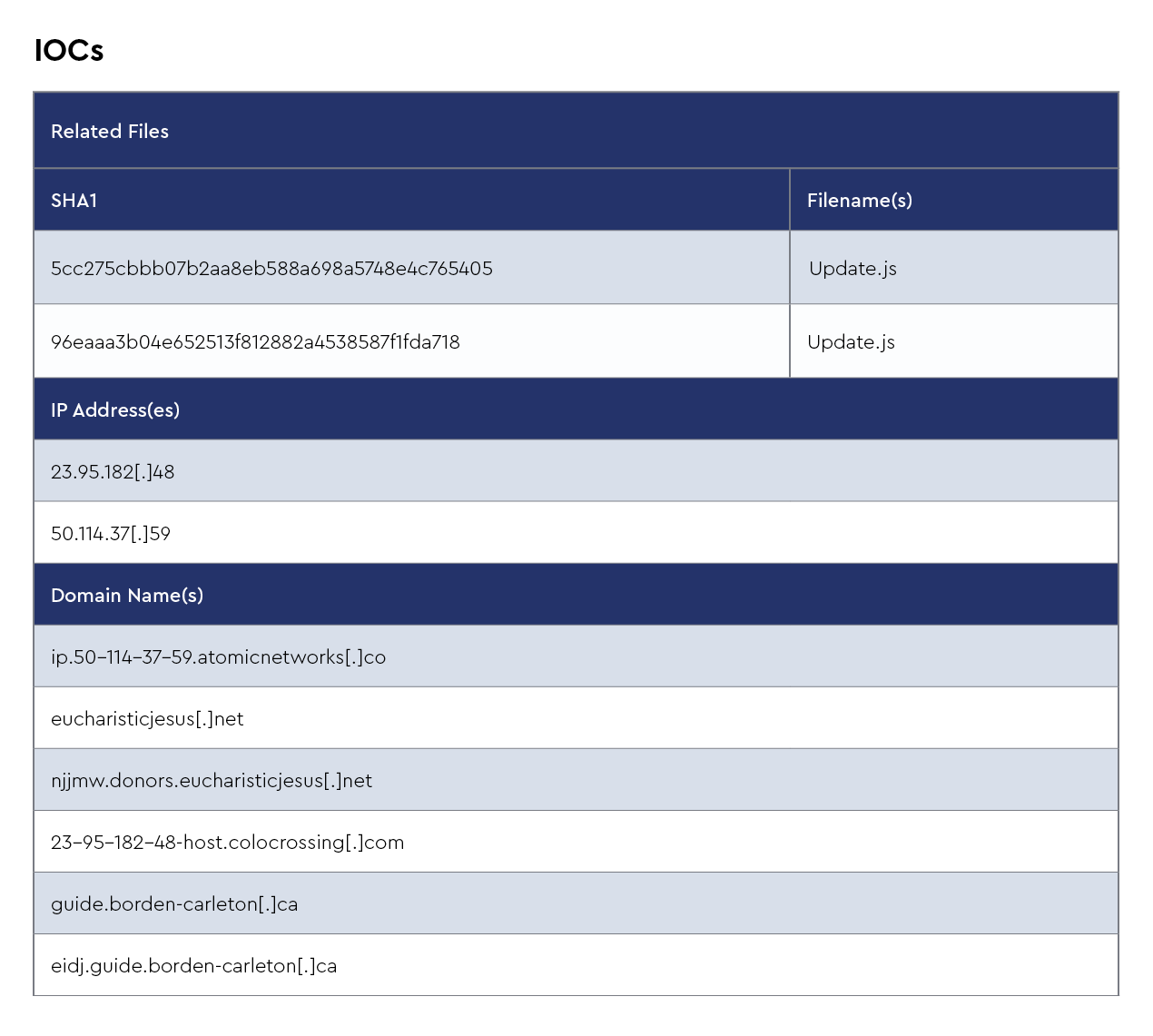
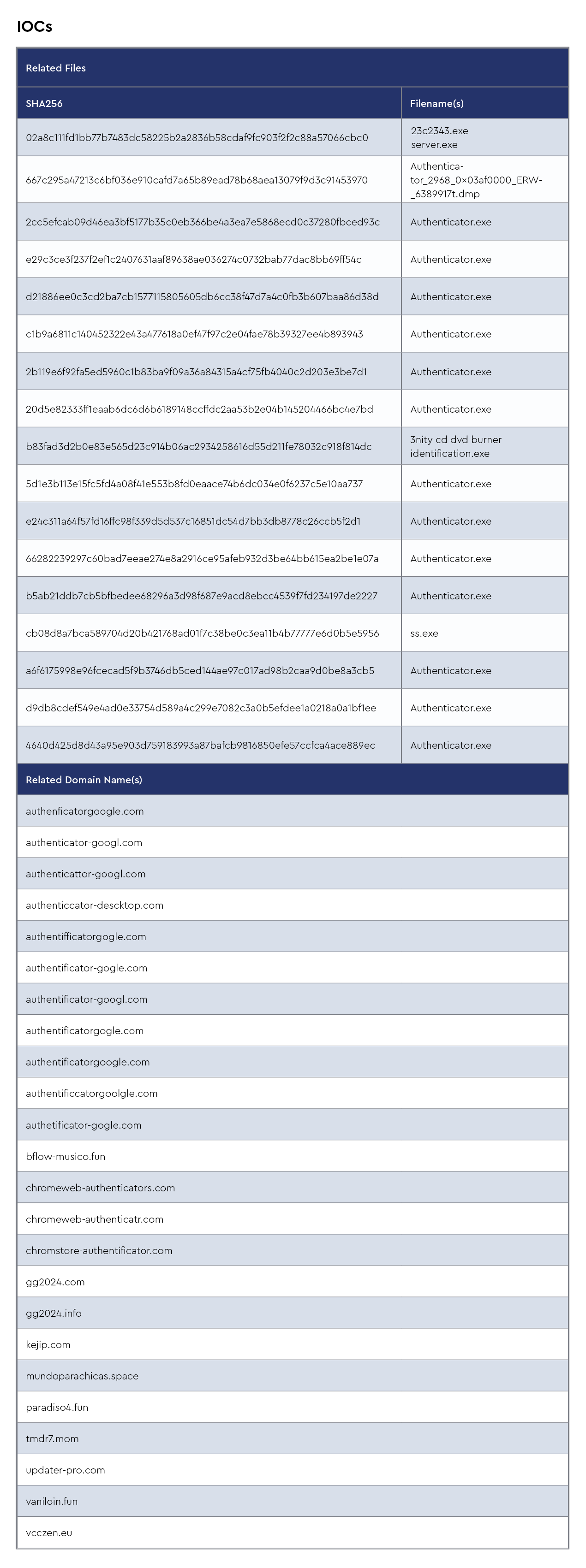
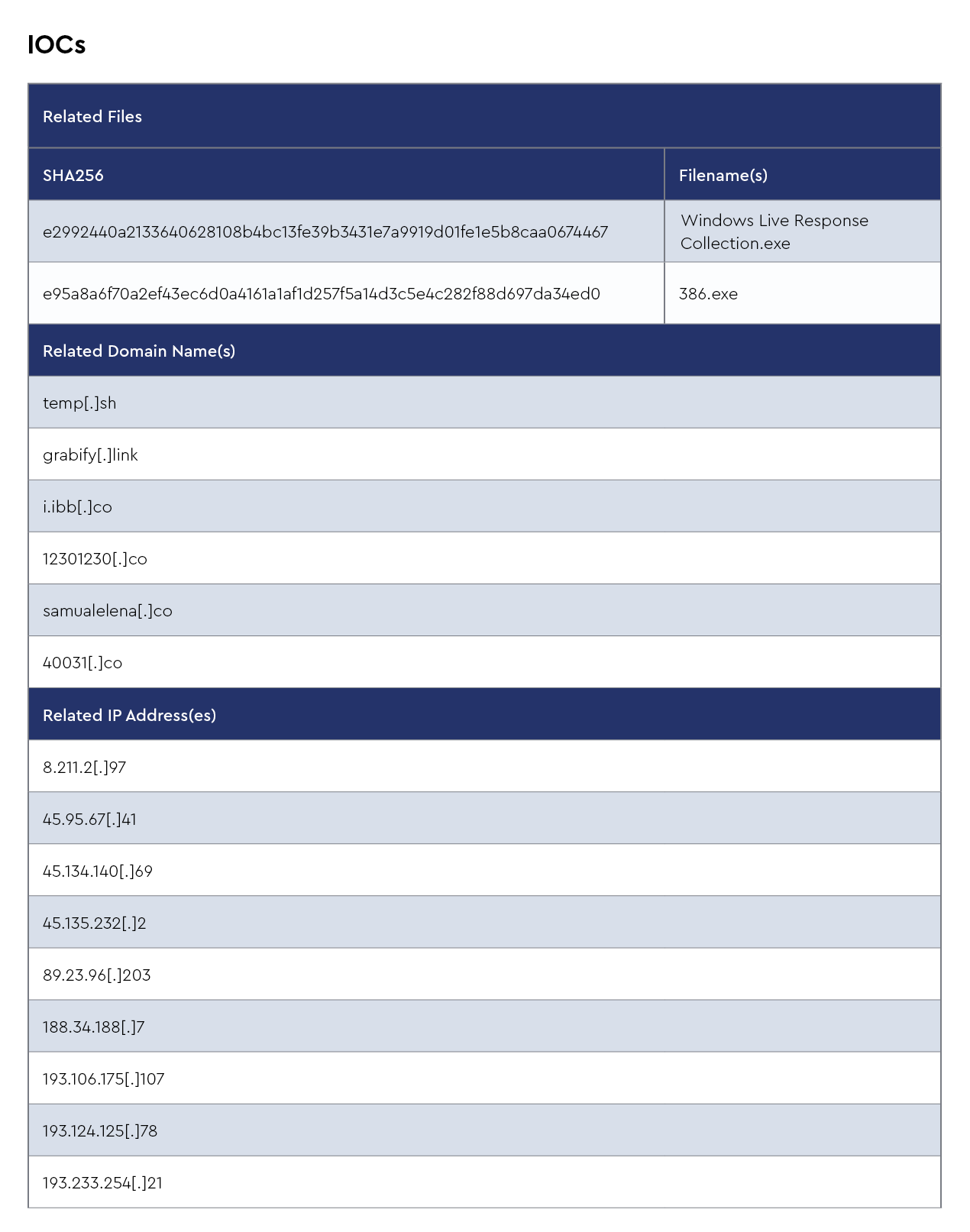
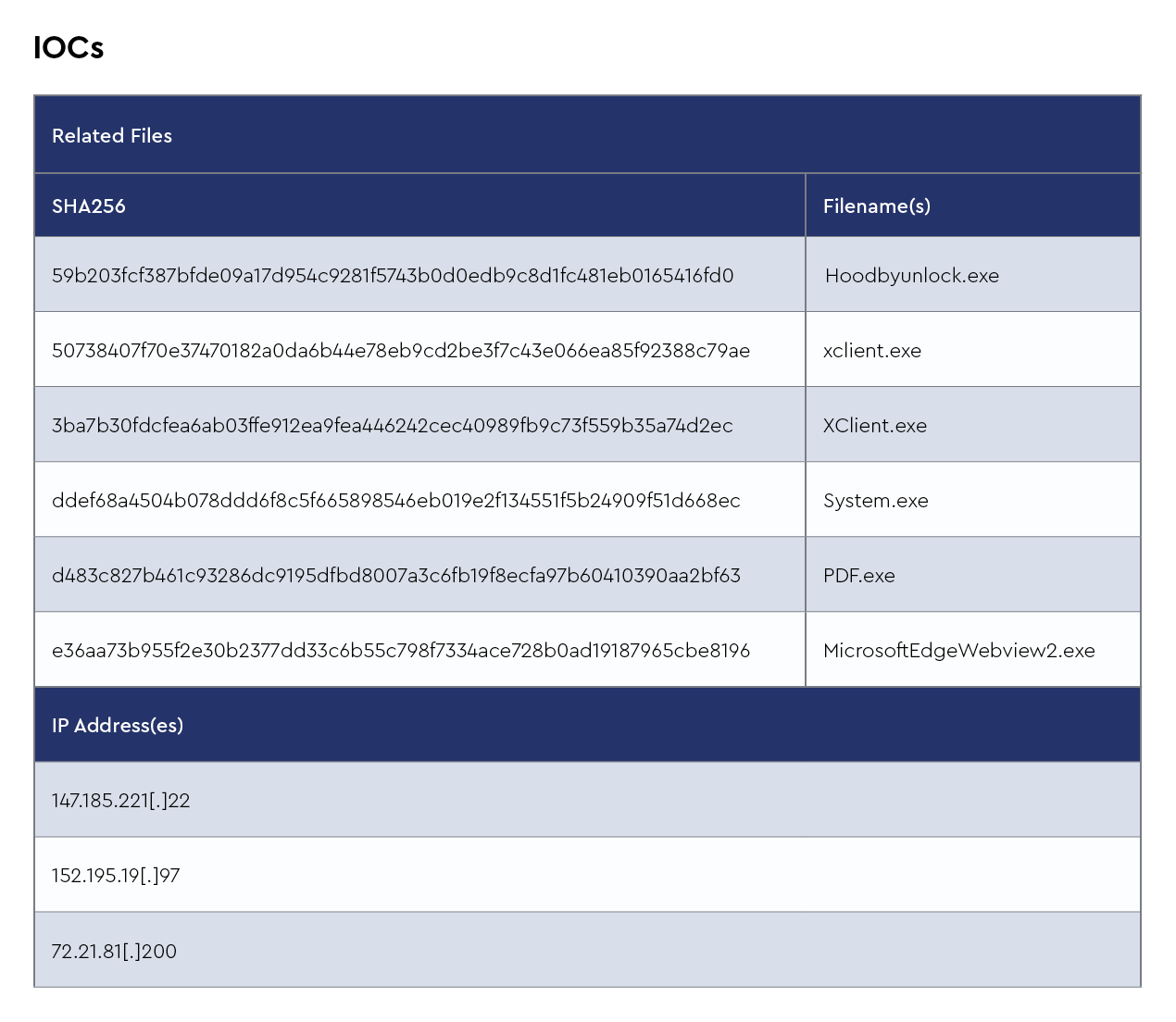
IOCs
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected.
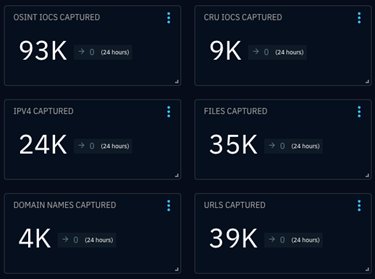
Figure 1: Summary of IOCs collected in August 2024
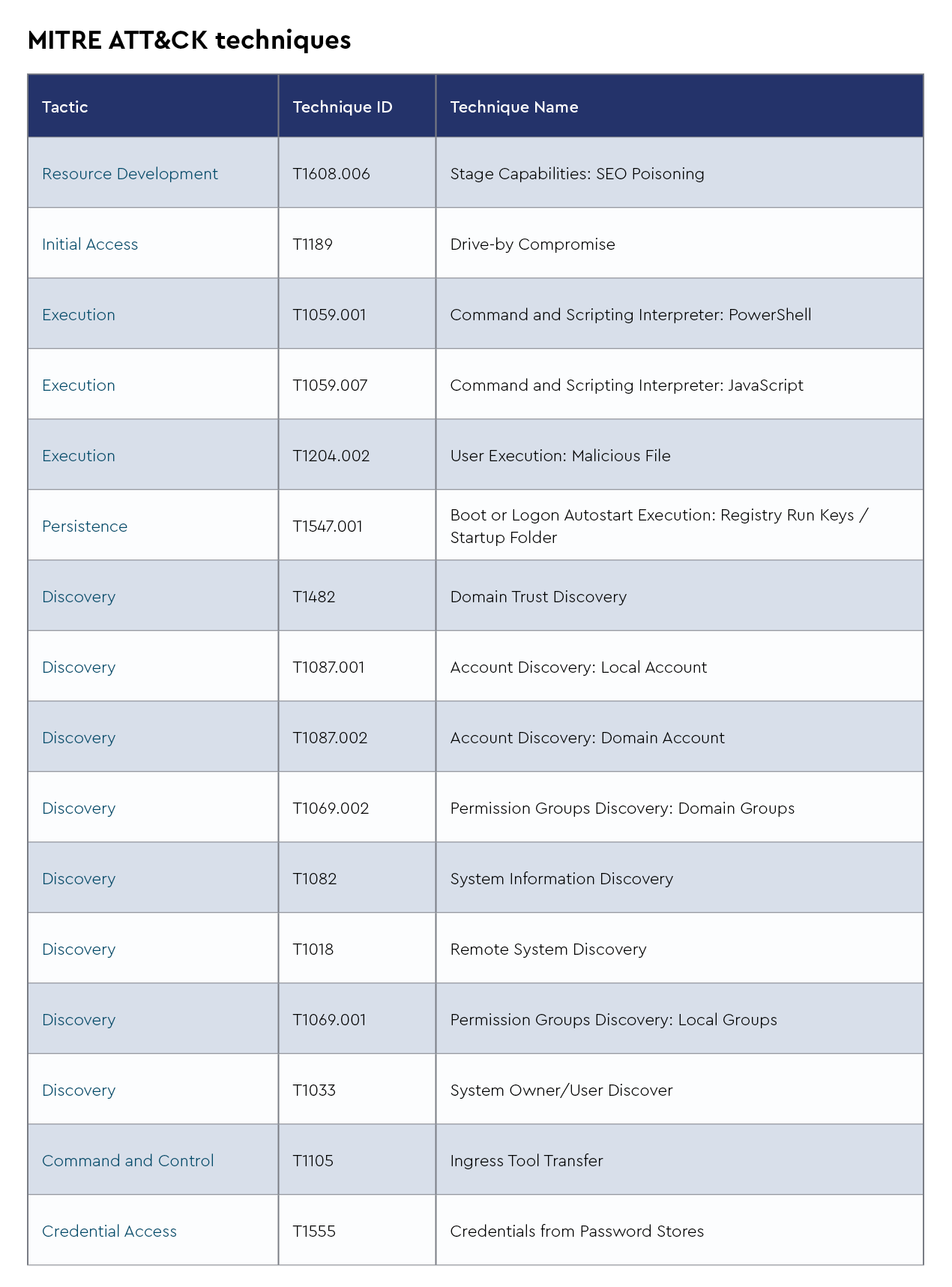
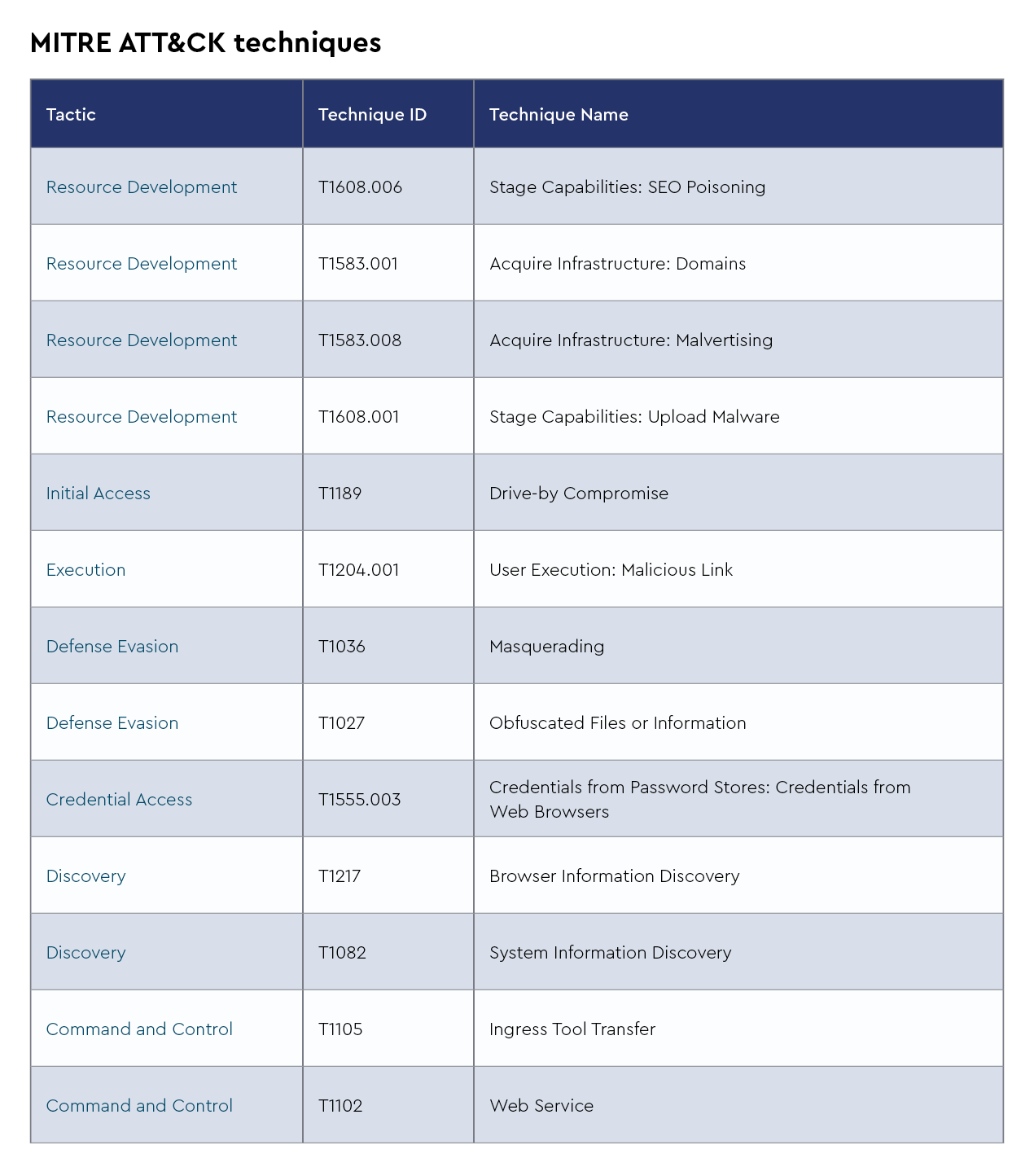
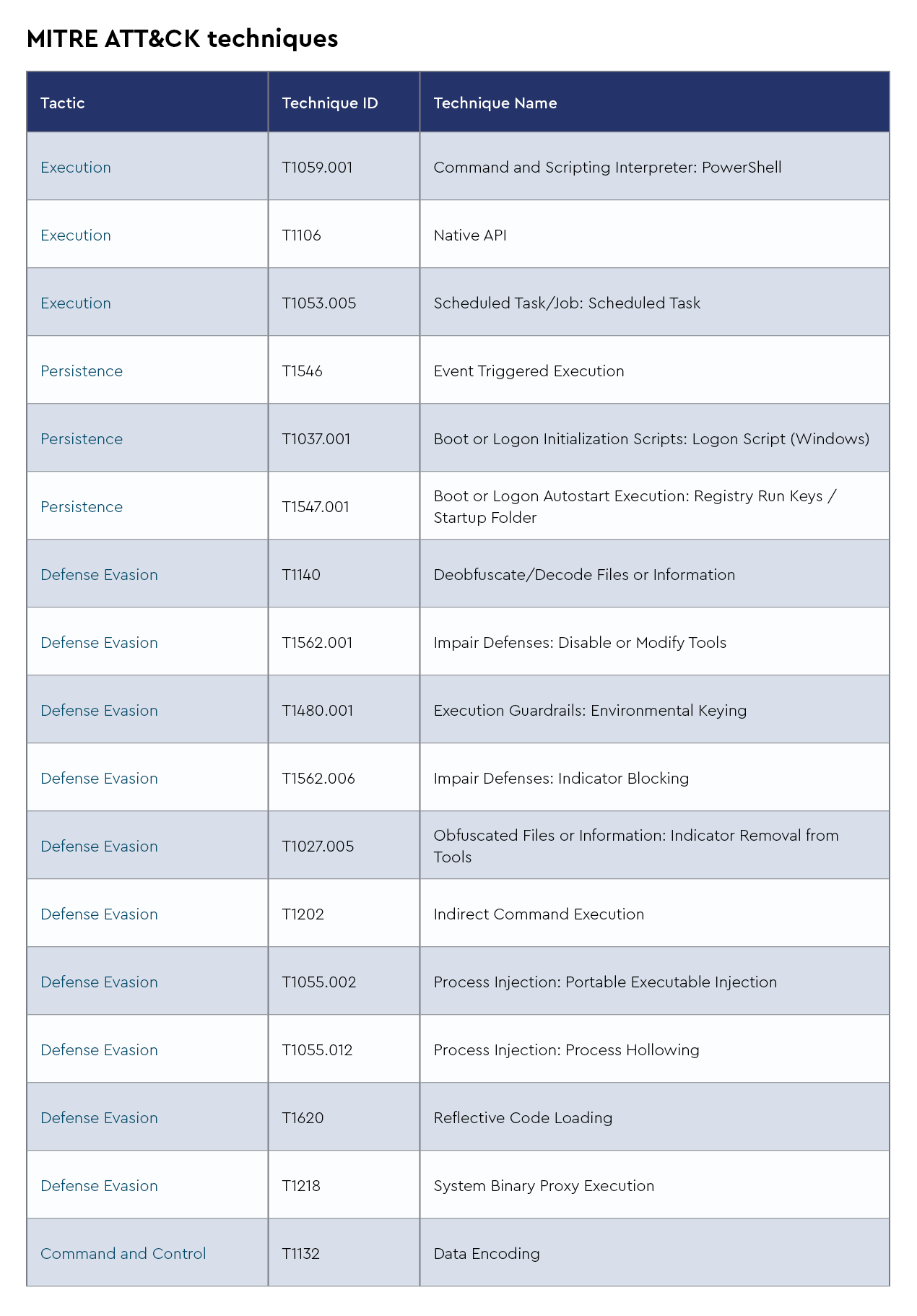
TTPs
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for July 2024—provided for comparison—and August 2024.
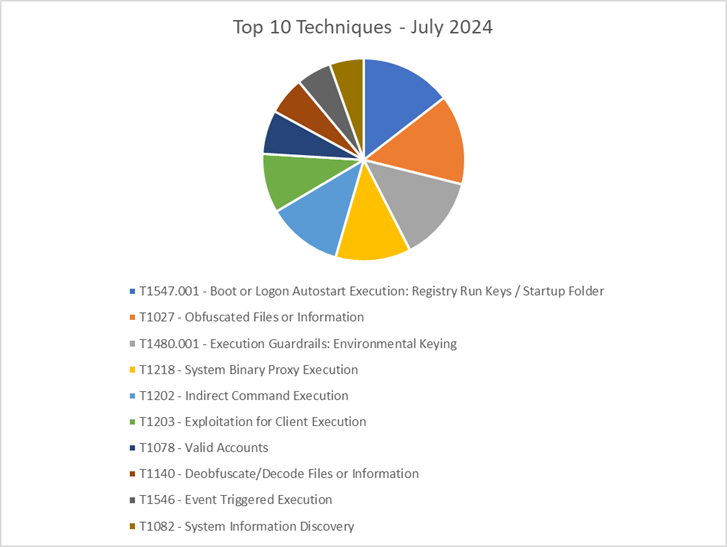
Figure 2: Top 10 MITRE ATT&CK techniques observed in July 2024
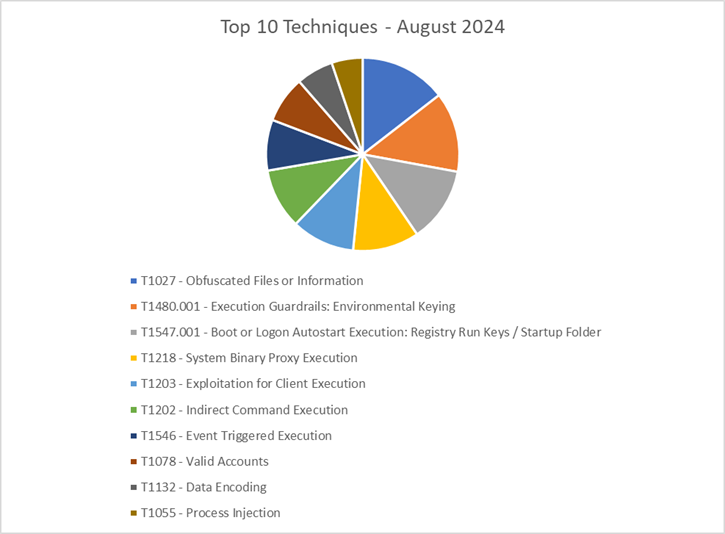
Figure 3: Top 10 MITRE ATT&CK techniques observed in August 2024
Latest threats
Each month, we highlight threats that we have seen targeting our MSP partners and their clients.
Malware
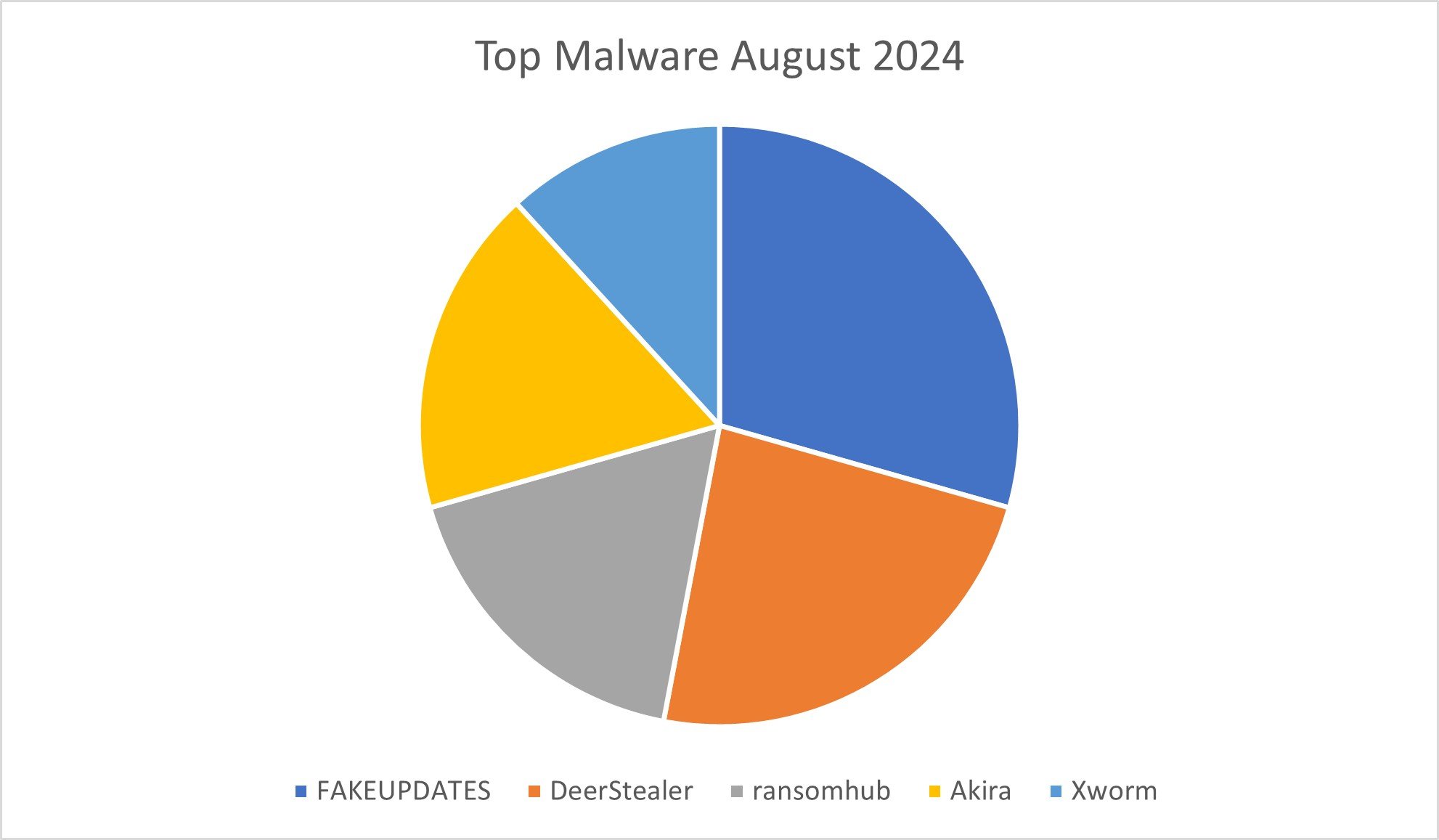
Figure 4: Top five malware observed in August 2024
FAKEUPDATES/FakeUpdates
FakeUpdates, also known as SocGholish, is a prevalent malware campaign that emerged around 2018, characterized by its use of social engineering techniques to trick users into downloading malicious software disguised as legitimate updates. This malware is primarily delivered through compromised websites, where users are prompted with fake update notifications, typically for common software such as Adobe Flash Player or browser updates. These prompts are designed to appear authentic, exploiting users’ trust and urgency to keep their software up-to-date.
Once the user initiates the download, the malware installs a backdoor on the system, providing attackers with remote access and control. FakeUpdates is often used as a delivery mechanism for additional payloads, including ransomware, banking trojans, and information stealers. The attackers leverage this access to exfiltrate sensitive data, deploy further malware, or use the compromised systems for broader campaigns. The widespread use of compromised legitimate websites and the convincing nature of the fake update prompts make FakeUpdates a significant threat, capable of impacting a wide range of users and organizations. Its persistence and adaptability in evading detection underscore the importance of robust cybersecurity practices and user education to mitigate such threats.
DeerStealer
DeerStealer is a recently identified information-stealing malware that has gained attention for its use of fake Google Authenticator websites to trick users into downloading its malicious payload. This campaign primarily relies on social engineering tactics, where threat actors create counterfeit Google ads that lead users to seemingly legitimate websites. Once the malware is downloaded, it operates by collecting sensitive information, including system details, browser data, and credentials. DeerStealer uses XOR encryption to securely transmit the stolen data back to its command-and-control server, making it difficult to detect and analyze. The malware is believed to be a variant or evolution of the XFiles malware family, as it shares some code and techniques with this older malware strain.
We recently reported that DeerStealer was being distributed through malicious Google search ads, which impersonate Google Authenticator software download sites. Victims are redirected through a series of URLs before landing on a phishing page that closely resembles an official Google site. This type of [T1608.006] SEO poisoning and [T1583.008] malvertising is increasingly affecting our managed service provider (MSP) partners and their clients. The malicious campaign has highlighted the ongoing challenges of malvertising and the need for heightened vigilance against such social engineering tactics.
Ransomhub
RansomHub is a relatively new and growing ransomware-as-a-service (RaaS) platform that provides tools and infrastructure for cybercriminals to launch ransomware attacks. Similar to other RaaS groups, RansomHub operates by recruiting affiliates who carry out the attacks, while the core group focuses on developing and refining the ransomware software. Affiliates are given access to ransomware payloads, communication platforms, and negotiation tools to demand ransom from victims. The group typically targets corporate networks and critical infrastructure, leveraging double extortion tactics—encrypting data and threatening to release it publicly if ransoms are not paid.
Recent intelligence suggests that RansomHub has been ramping up its operations, with more sophisticated techniques emerging. They’ve been linked to using advanced evasion techniques, including encryption schemes that make payload detection harder, and exploiting zero-day vulnerabilities to breach networks. Recent activity indicates a shift in focus towards critical sectors such as healthcare and financial institutions, suggesting that the group is targeting organizations likely to pay larger ransoms. There’s also speculation that RansomHub is experimenting with supply chain attacks to increase its impact radius, a concerning trend in recent ransomware operations. CISA recently released an advisory concerning this growing threat.
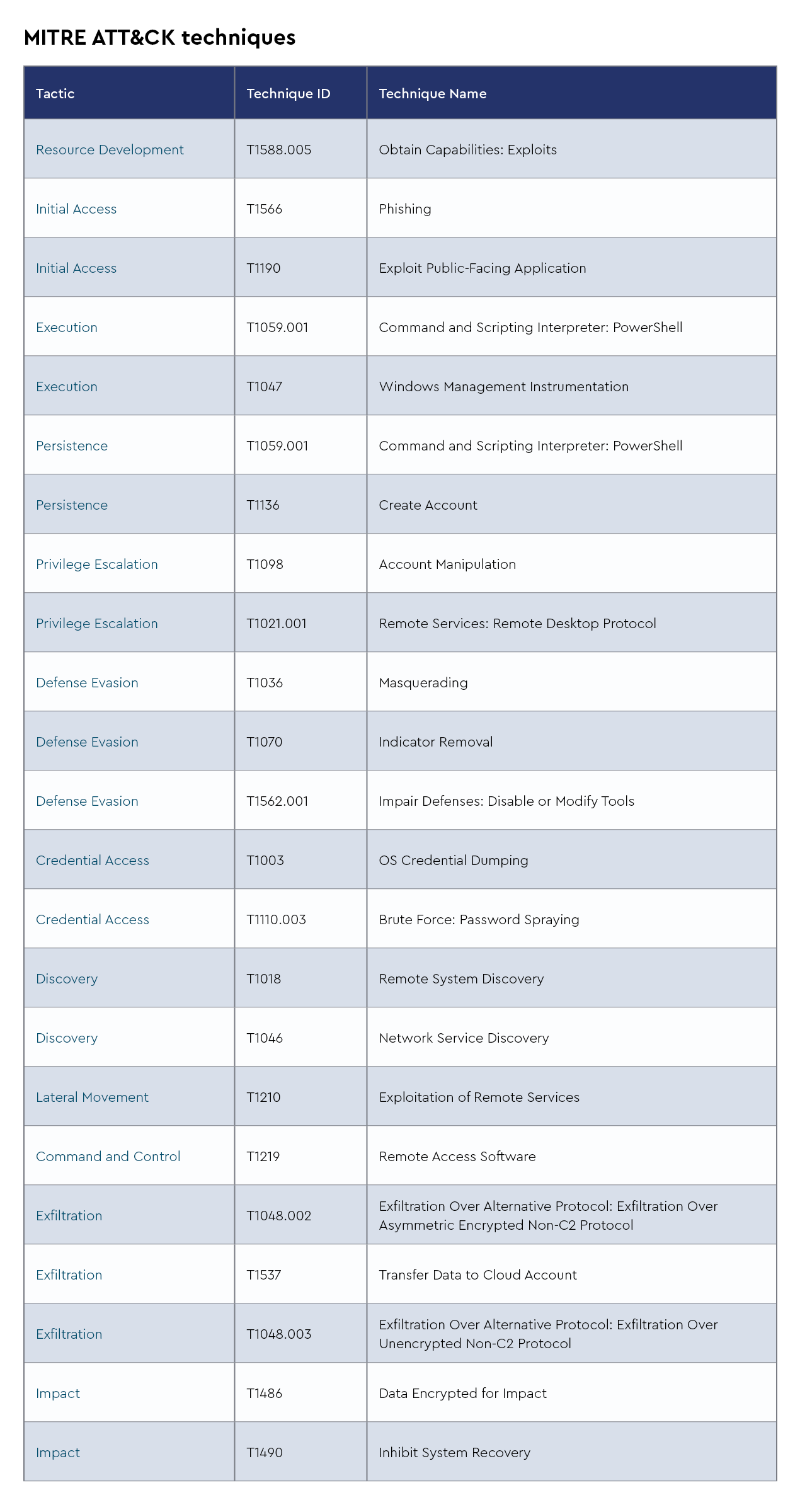
Akira
Akira is a ransomware group that emerged in early 2023, operating under the RaaS model. It quickly gained attention due to its effective use of double extortion techniques, where attackers not only encrypt victim data but also exfiltrate sensitive information, threatening to leak it if ransom demands are not met. Akira’s ransomware payloads are often customized for each attack, and the group has been observed targeting a wide range of industries, including healthcare, finance, and education. They exploit vulnerabilities in remote access services such as VPNs and RDP to gain initial access to networks, often after weak or compromised credentials have been used.
Recent intelligence indicates that Akira has been increasing the frequency and scale of its attacks. The group is known for its aggressive negotiation tactics, sometimes demanding multi-million-dollar ransoms. Reports have linked Akira to attacks in multiple countries, targeting both small and large organizations. They have been particularly focused on Western targets, where they believe ransoms are more likely to be paid. Akira’s adaptability and ability to evade detection by disabling security tools during attacks make them a growing threat on the ransomware scene.
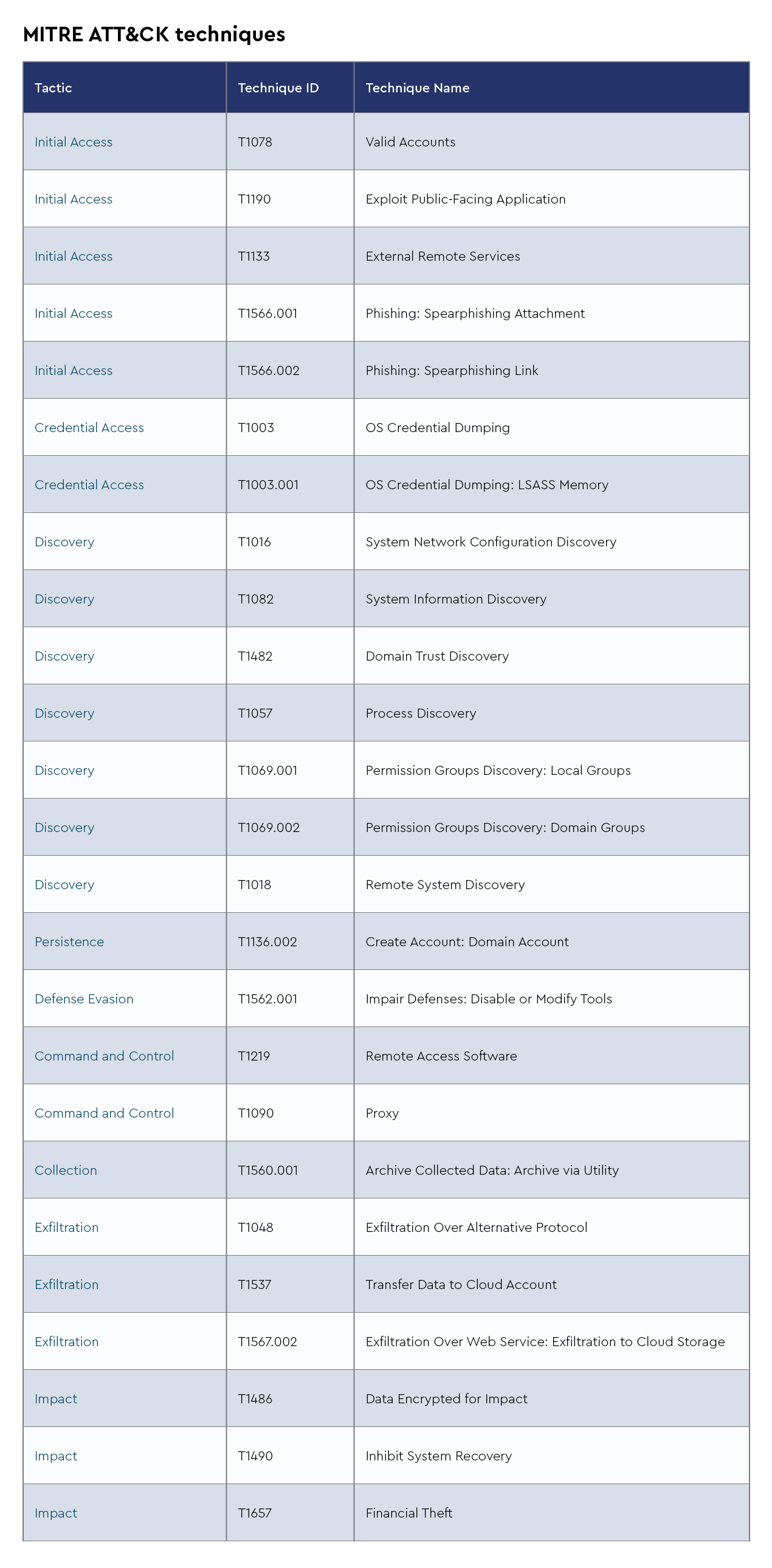
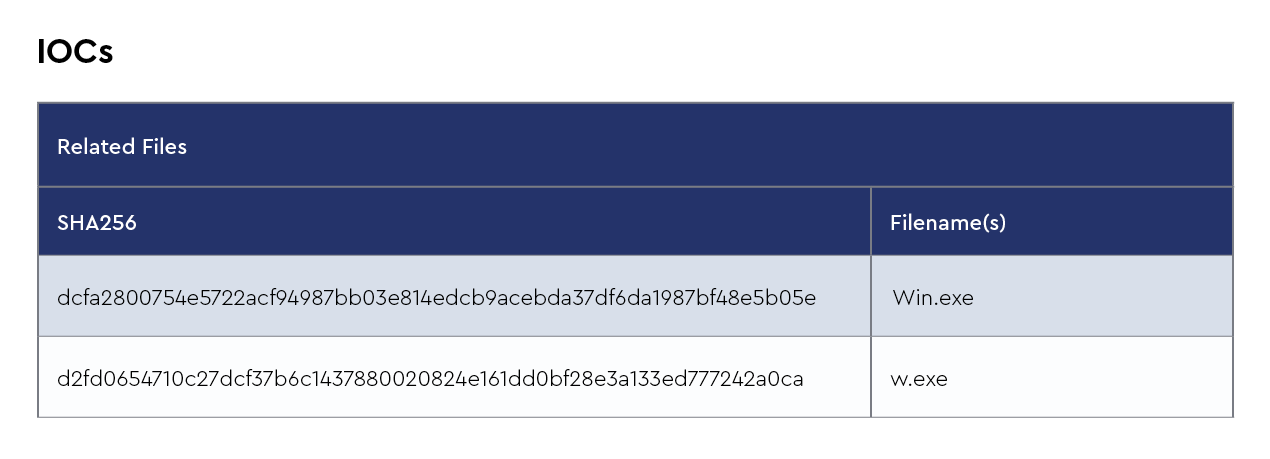
XWorm
XWorm is a remote access trojan (RAT) that has been gaining traction among cybercriminals due to its versatility and stealth. Distributed primarily through phishing emails and malicious attachments, XWorm enables attackers to take full control of an infected system. Once installed, it provides remote access, allowing for keylogging, screen capturing, data exfiltration, and the ability to run arbitrary commands. XWorm is lightweight, which makes it harder to detect, and it’s often obfuscated to avoid antivirus detection. It can spread laterally within a network, making it particularly dangerous for corporate environments.
Recent intelligence suggests that XWorm has been updated with additional functionalities, including more advanced evasion techniques and modular components that make it adaptable to various attack scenarios. Cybercriminals are increasingly using it in targeted attacks, often against organizations with weak email security controls. There have been reports of its use in financial sector attacks, where XWorm was deployed to steal credentials and banking information. Furthermore, the malware has been spotted in campaigns linked to both espionage and financial gain, indicating its growing popularity among different threat actors. Its evolving capabilities and widespread availability on underground forums make it a persistent and adaptable threat.
Monthly newsletter summary
The following is a summary of articles shared in the CRU newsletter during the month of August.
Massive DDoS Attack Leads to Extended Microsoft 365 and Azure Outage
A recent distributed denial of service (DDoS) attack on Microsoft’s Azure services led to a major outage, exacerbated by a misconfiguration in its DDoS protection setup. The attack flooded Azure’s network with malicious traffic, and while defenses were activated, a configuration error amplified the issue, causing extensive global service disruptions for several hours. Key services, including Azure app services and parts of Microsoft 365, were impacted. The incident highlights the need for continuous testing and improvement of DDoS defenses, urging businesses and MSPs to regularly audit and refine their cybersecurity strategies to prevent similar vulnerabilities.
Fake Google Authenticator Ad Spreads DeerStealer Malware
A recent cyberthreat campaign used fake Google ads to distribute the DeerStealer malware via a fraudulent Google Authenticator app, demonstrating the growing use of malvertising by cybercriminals. The attackers created deceptive ads that mimicked legitimate ones, often bypassing Google’s security checks and directing users to malicious sites. Once users downloaded the fake app, DeerStealer was activated, stealing credentials, financial data, and personal information. The incident highlights the need for advanced threat detection and response mechanisms, collaboration on threat intelligence, and stronger cybersecurity measures for online advertising platforms to prevent similar attacks in the future.
SharpRhino Malware Targets IT Administrators
SharpRhino is a new malware strain attributed to the cybercriminal group Hunters International. It poses a significant threat to IT administrators by disguising itself as the popular networking tool Angry IP Scanner. Spread through typo-squatted websites, SharpRhino installs via a malicious executable that alters system settings for persistence and communicates with command and control servers for deeper infiltration. It can propagate across networks, deploying additional malicious tools, including a Rust-based encryptor that locks files and demands ransom via a Tor-based payment page. This campaign highlights Hunters International’s evolution in ransomware, with ties to Hive ransomware. It underscores the need for improved web filtering, vigilant IT practices, and robust backup strategies to mitigate such threats.
August 2024: Patch Tuesday Recap
This month’s Patch Tuesday saw Microsoft address 90 CVEs, including several critical elevation of privilege (EoP) vulnerabilities, such as CVE-2024-38202 and CVE-2024-38163, which exploit weaknesses in the Windows update stack, allowing attackers to bypass virtualization-based security (VBS). A key concern is CVE-2024-38063, a remote code execution (RCE) vulnerability in the Windows TCP/IP stack, enabling attackers to send malicious IPv6 packets for potential system compromise. Additionally, CVE-2024-38200 exposes NTLM hashes in Microsoft Office documents, risking pass-the-hash attacks. Microsoft recommends interim mitigations such as auditing backup operations, restricting NTLM usage, and closely monitoring systems until official patches are released. These vulnerabilities emphasize the importance of timely updates, strong access controls, and user education to prevent exploitation.
Guarding Against EDR Killers: Guidance for Enhanced Security
Sophos analysts recently discovered a new EDR-killing tool, “EDRKillShifter,” used during a RansomHub ransomware attack to disable endpoint protections. EDR killers, like EDRKillShifter, exploit vulnerabilities in legitimate drivers through a technique called “bring your own vulnerable driver,” or (BYOVD), which grants kernel-level access to tamper with security systems. EDRKillShifter uses vulnerable drivers such as RentDrv2 and ThreatFireMonitor to escalate privileges and turn off EDR protections. Other EDR killers, such as Terminator and AvNeutralizer, similarly exploit drivers to neutralize security measures. To protect against such threats, organizations should enable tamper protection in EDR solutions, block known vulnerable drivers, regularly update systems, and implement multi-layered defenses and network segmentation. Educating users and limiting admin privileges are also crucial to reducing risk.
New ConnectWise SIEM signatures
Several new ConnectWise SIEM detection signatures were added in August 2024. These include:
- [CRU] SolarWinds Web Help Desk Java Deserialization Remote Code Execution Vulnerability (CVE-2024-28986)
Techniques detected: [T1203]
Description: This detection identifies potential exploitation attempts of a critical Java deserialization vulnerability (CVE-2024-28986) in SolarWinds Web Help Desk (WHD). This flaw allows attackers to execute arbitrary code on vulnerable systems. While initially reported as unauthenticated, SolarWinds has been unable to reproduce the vulnerability without authentication. However, the critical nature of this vulnerability and its addition to CISA’s Known Exploited Vulnerabilities Catalog highlight the urgent need for patching.
- [CRU] Renamed BOINC Client Or BOINC Use Connected to Scheduled Task
Techniques detected: [T1036.005], [T1053.005]
Description: This detection rule identifies attempts to rename the BOINC client or its use in connection with a scheduled task, which may indicate malicious activity. Threat actors have been observed renaming the legitimate BOINC.exe or using it within scheduled tasks to evade detection. This tactic is often employed to leverage BOINC for unauthorized distributed computing or other malicious purposes.
- [CRU][Windows] Credential Access Tools
Techniques detected: [T1003]
Description: This detection identifies the potential usage of various credential access tools, including Mimikatz and other password dumping and recovery tools. These tools can be used by attackers to gain access to sensitive information, escalate privileges, and move laterally within a network. The alert is triggered by the presence of specific files or processes associated with these tools.
- [EA][O365] Potential Ransomware Activity
Techniques detected: [T1486]
Description: Requires Microsoft Defender for Cloud Apps. This enhanced alert forwards Microsoft alerts when Defender for Cloud Apps identifies a user’s files as similar to ransomware.
- [EA][CRU][Windows] Suspicious File Created in Fonts Directory
Techniques detected: [T1036.005]
Description: This alert triggers when a suspicious file type is downloaded into the C:\Windows\Fonts directory. Threat actors have been observed dropping malicious files into this directory. Examine the source of the file and any execution subsequent execution for validation of this activity.
- [VMware][Syslog] ESXi VM Destroyed by User
Techniques detected: [T1070], [T1485]
Description: This detection identifies when a virtual machine (VM) on a VMWare ESXi host is destroyed by a user. This alert is important because destroying a VM can potentially lead to data loss and service disruptions, or it could be an indication of malicious activity if performed by an unauthorized user.
- [VMware][Syslog] ESXi Snapshot Deletion
Techniques detected: [T1490], [T1485]
Description: This detection identifies Snapshot deletion events on VMware ESXi hosts. Unauthorized or unexpected deletions could indicate malicious activity. We recommend verifying that this activity was authorized or expected.
New IDS signatures added in August 2024:
[Connectwise CRU] Apache OFBiz Incorrect Authorization (CVE-2024-38856)
[ConnectWise CRU] EXPLOIT Progress WhatsUp Gold APM Unrestricted File Upload RCE (CVE-2024-5008)
[ConnectWise CRU] CVE--2024-4577 Windows PHP Vulnerability POST
[ConnectWise CRU] Possible CVE-2024-5217 Exploitation





























