Monthly Threat Brief: November 2024
Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU). In this threat brief, we will provide raw data statistics, intel on specific threats, and a list of new detection signatures added to the ConnectWise SIEM™ throughout the month of November.
For a more detailed explanation of the overall trends and analysis of these numbers, check out the 2024 MSP Threat Report. For comparison, October’s threat brief can be found here.
November 2024 stats
IOCs
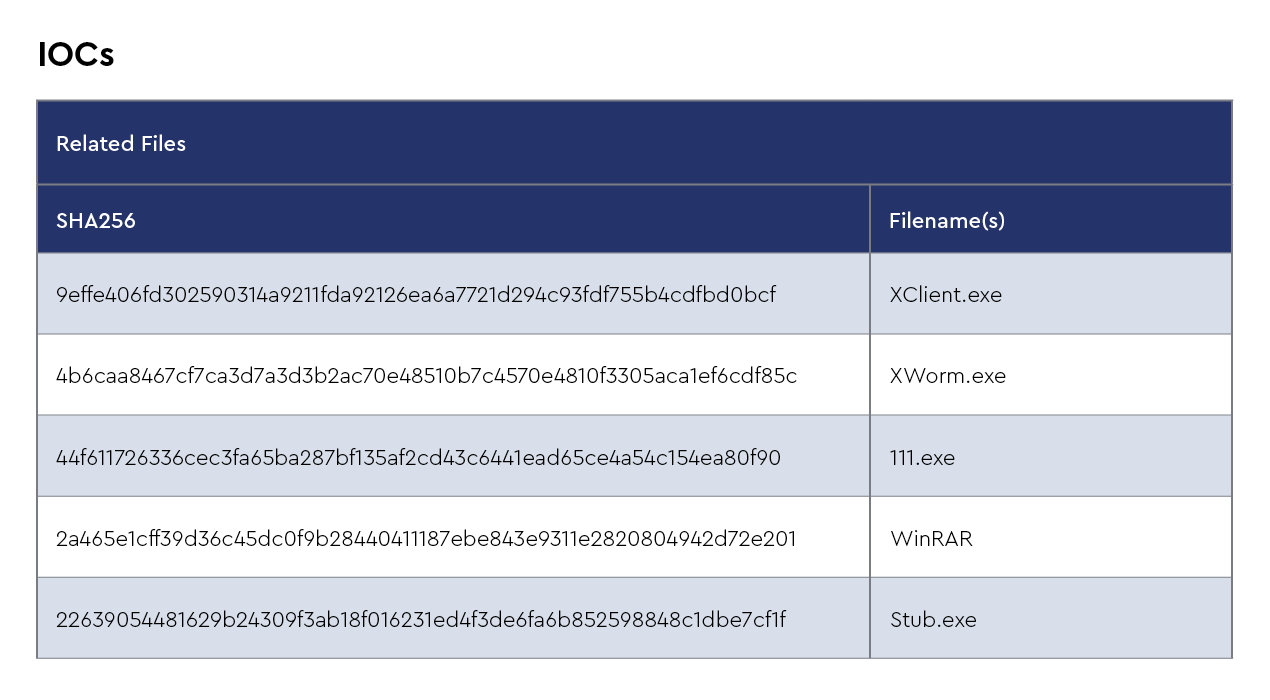
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected.
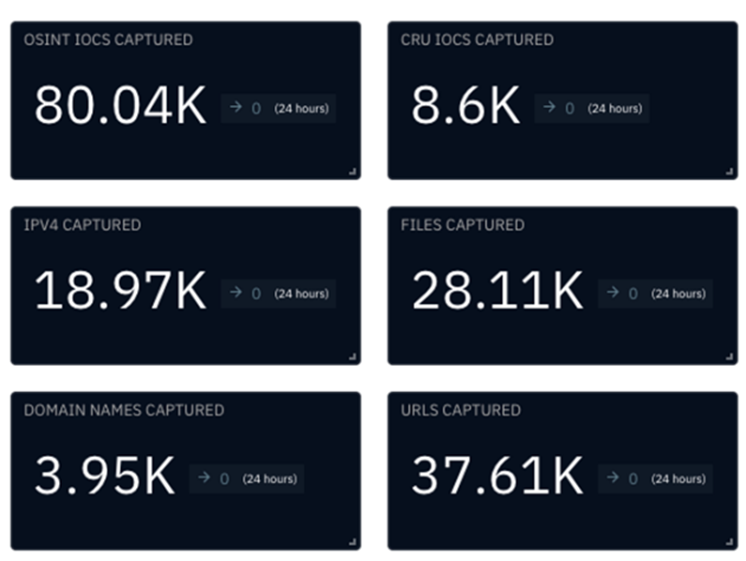
Figure 1: Summary of IOCs collected in November 2024
TTPs
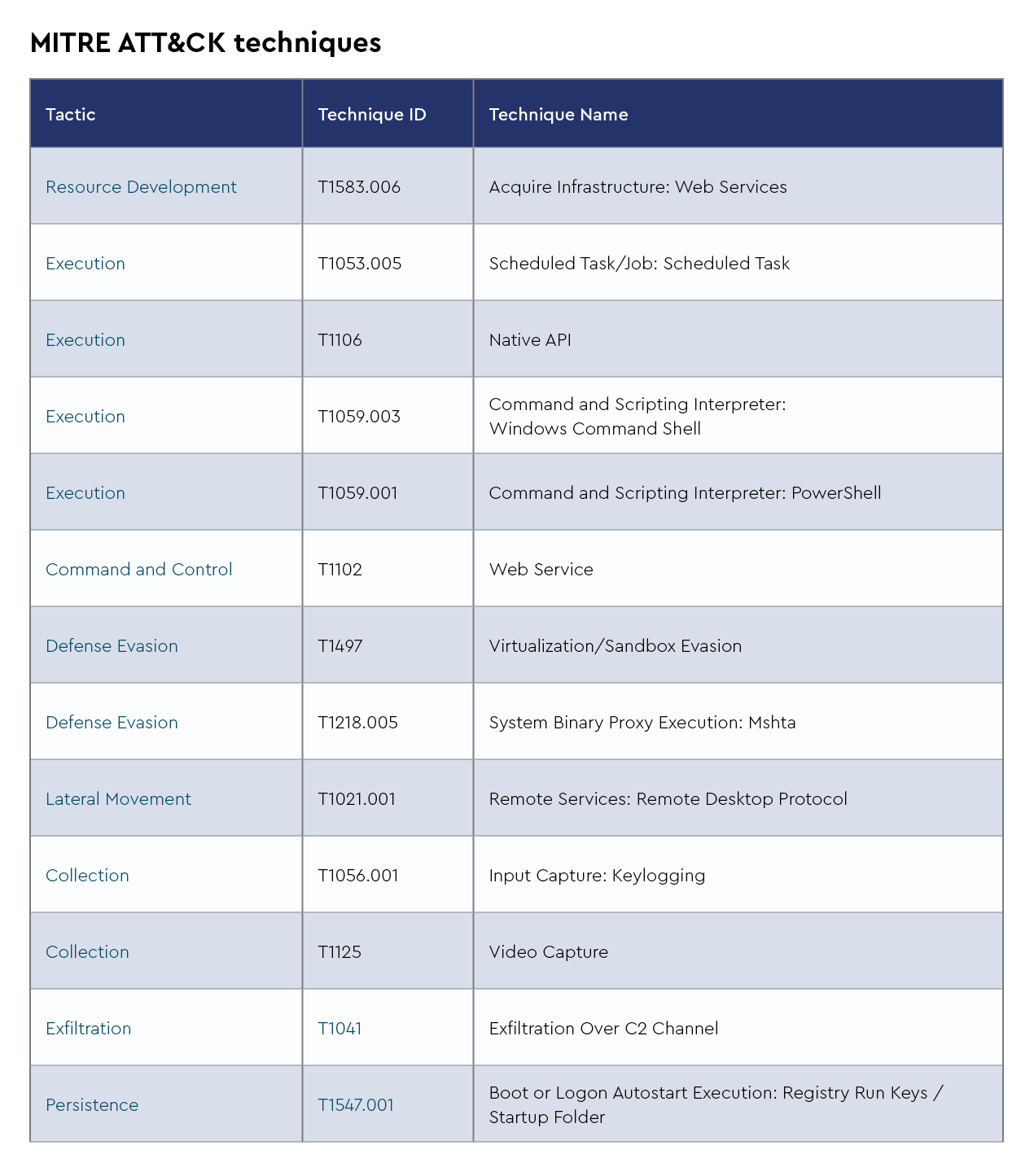
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for October 2024—provided for comparison—and November 2024.
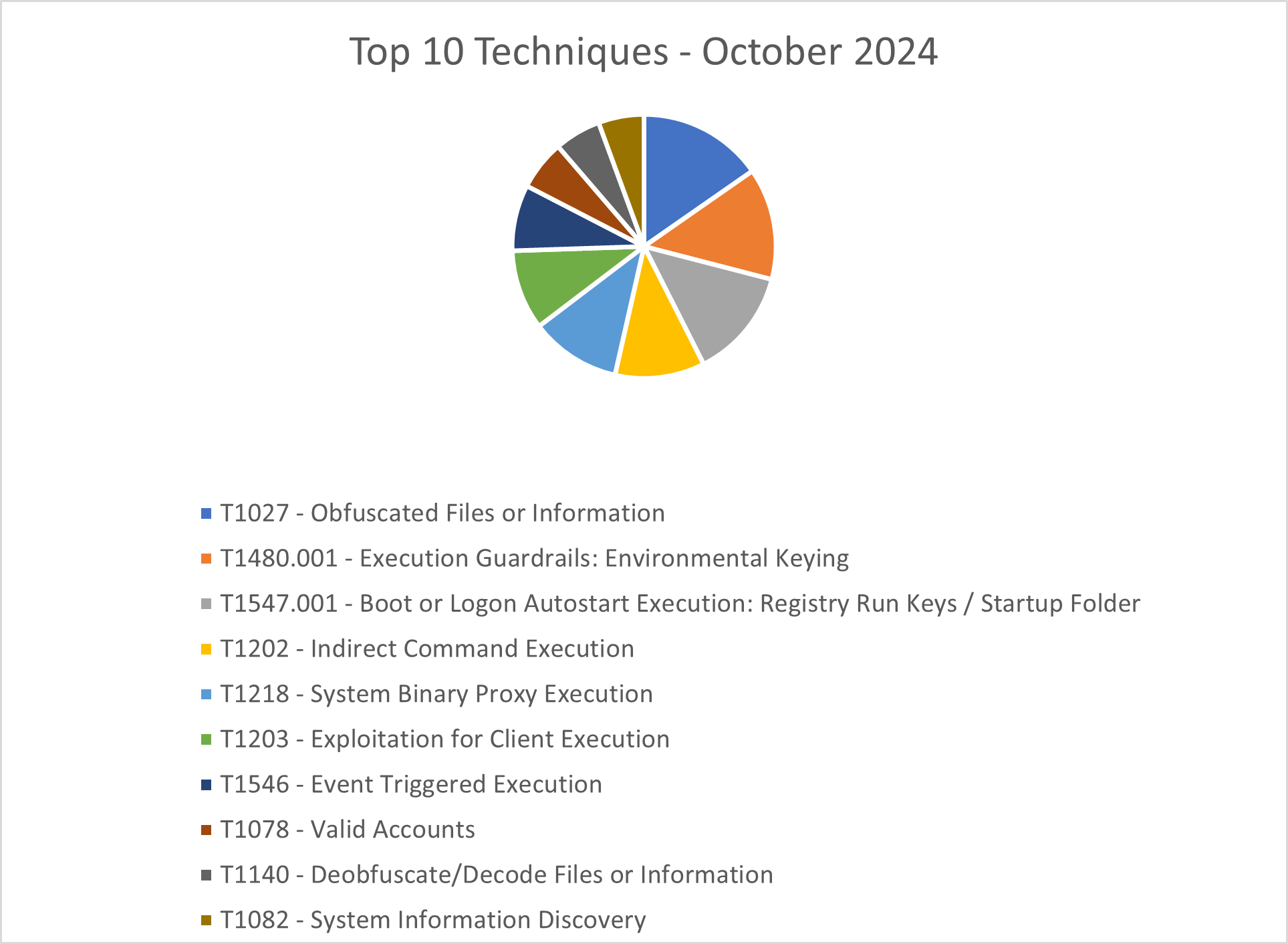
Figure 2: Top 10 MITRE ATT&CK techniques observed in October 2024
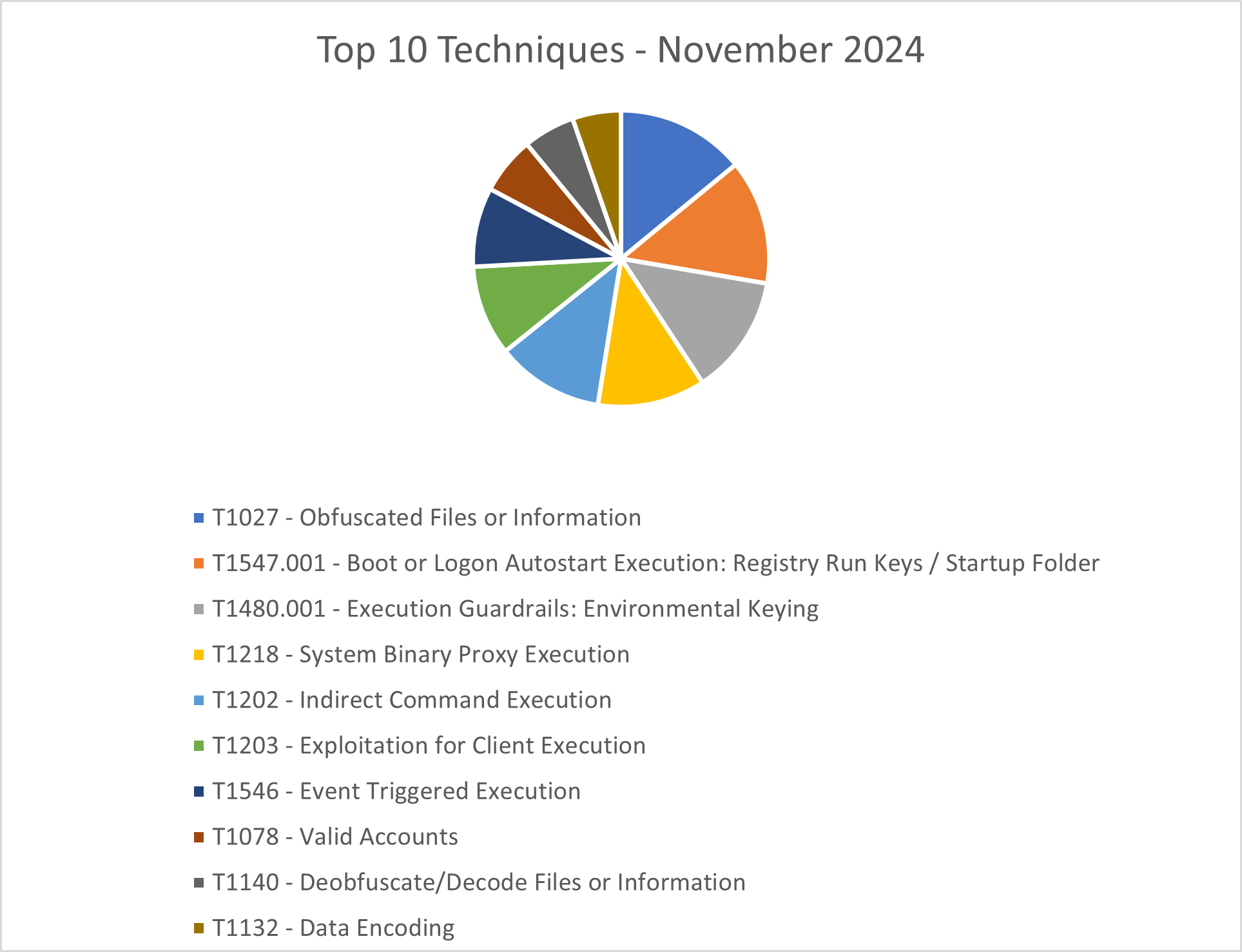
Figure 3: Top 10 MITRE ATT&CK techniques observed in November 2024
Latest threats
Each month, we highlight threats that we have seen targeting our managed service provider (MSP) partners and their clients.
Malware
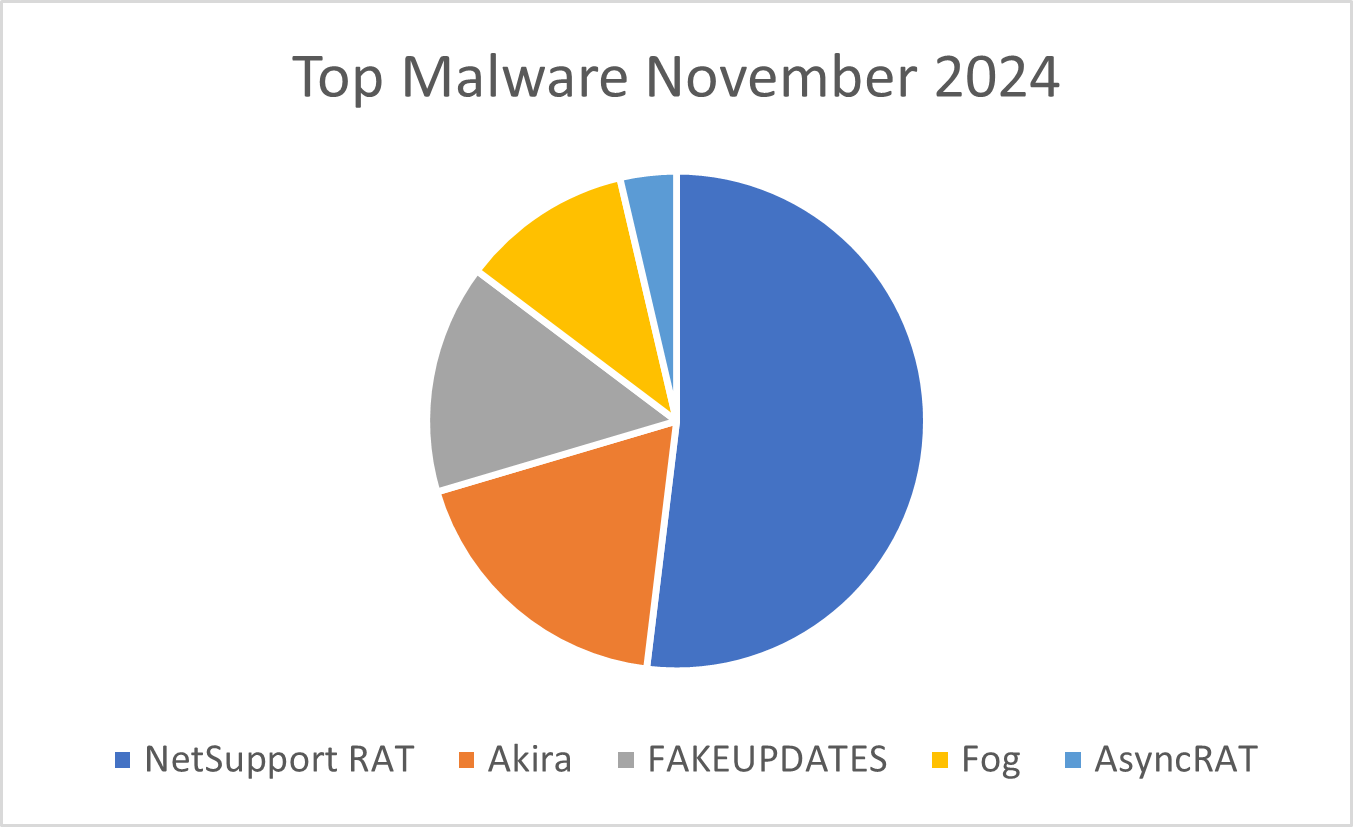
Figure 4: Top five malware observed in November 2024
NetSupport Manager RAT
NetSupport Manager RAT is a program that enables users to manage and control other computers over a network. It functions as a “remote access trojan,” and while it’s intended for legitimate uses such as technical support and corporate network management, it can also be misused.
The software offers various features, such as:
- Remote desktop control: Gives an administrator full access to the target computer’s screen and inputs
- File transfer: Allows moving files between the computers
- System inventory: Provides details about the target computer’s hardware and software
- Hardware and software monitoring: Tracks system performance and installed applications
- Chat functionality: Facilitates communication between the administrator and the target computer user
NetSupport Manager RAT operates by installing a client component on the target computer and a control component on the administrator’s computer. These components communicate via a network connection, enabling the administrator to access and control the target computer. However, remote administration tools, including NetSupport Manager RAT, can be used for malicious purposes. Cybercriminals frequently use similar software to infiltrate computers, steal confidential information, or carry out harmful activities without the user’s knowledge or consent.
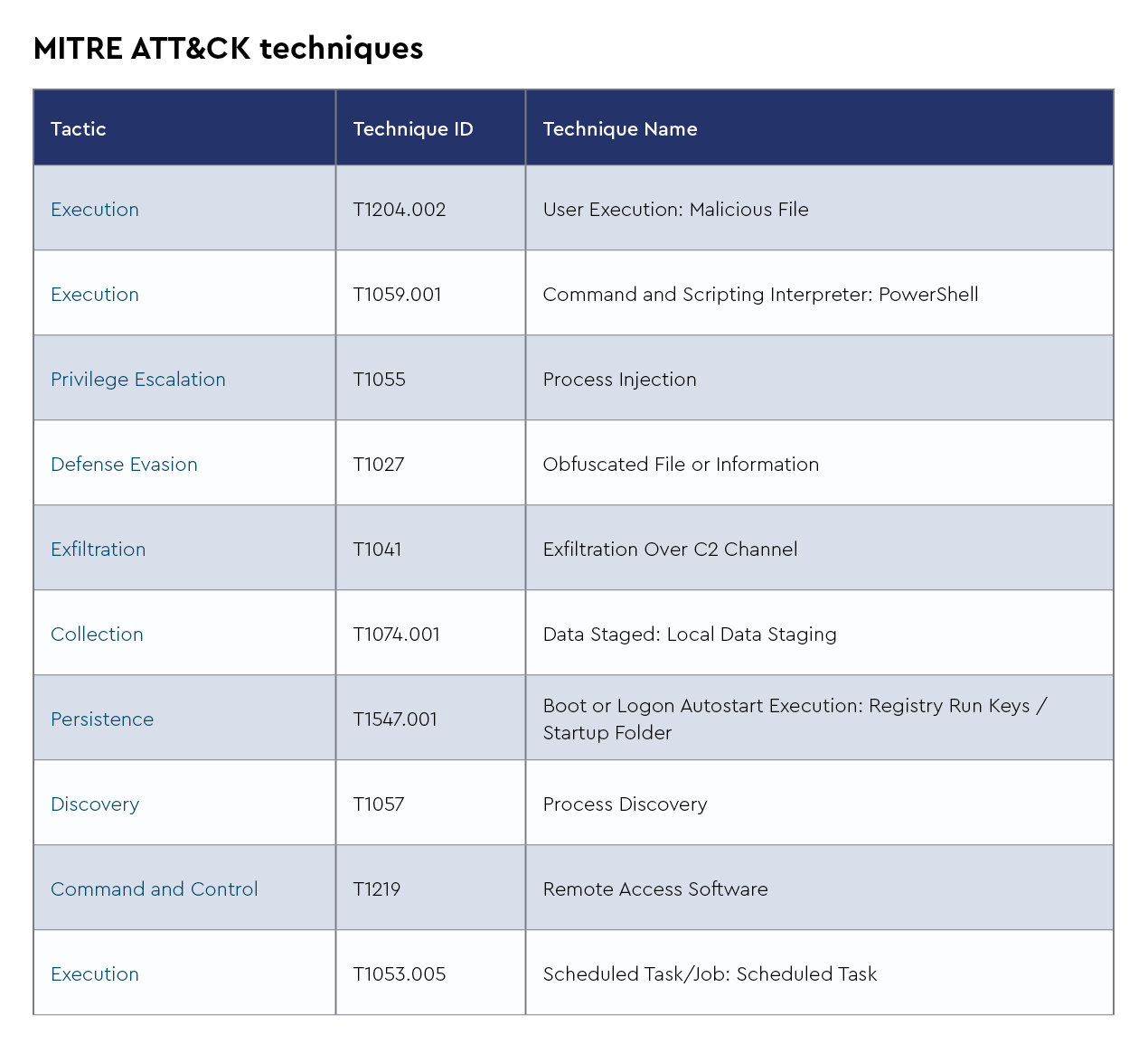
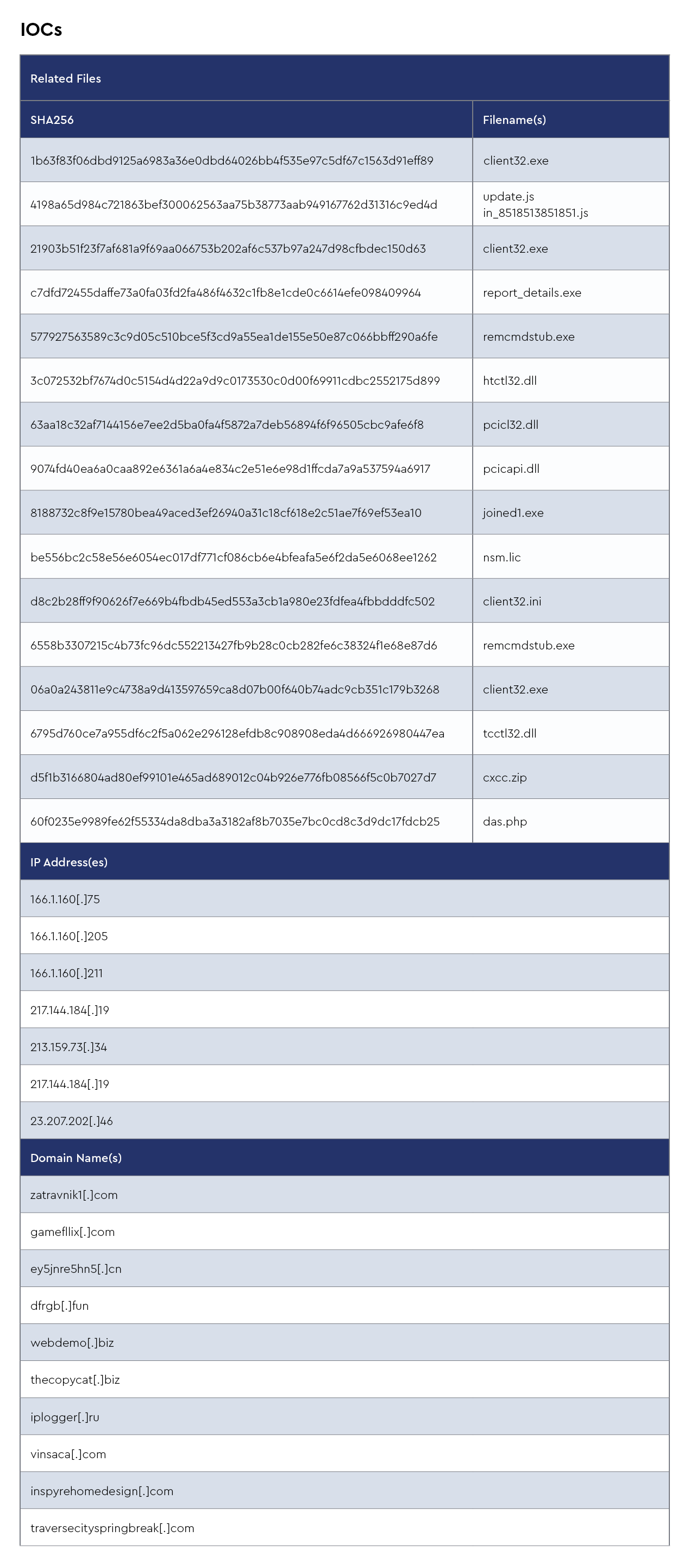
Akira
Akira is a ransomware group that emerged in early 2023, operating under the ransomware-as-a-service (RaaS) model. It quickly gained attention due to its effective use of double extortion techniques, where attackers not only encrypt victim data but also exfiltrate sensitive information, threatening to leak it if ransom demands are not met.
Akira’s ransomware payloads are often customized for each attack, and the group has been observed targeting a wide range of industries, including healthcare, finance, and education. They exploit vulnerabilities in remote access services such as VPNs and RDP to gain initial access to networks, often after weak or compromised credentials have been used.
Recent intelligence indicates that Akira has been increasing the frequency and scale of its attacks. The group is known for its aggressive negotiation tactics, sometimes demanding multi-million-dollar ransoms. Reports have linked Akira to attacks in multiple countries, targeting both small and large organizations. They have been particularly focused on Western targets, where they believe ransoms are more likely to be paid. Akira’s adaptability and ability to evade detection by disabling security tools during attacks make them a growing threat on the ransomware scene.
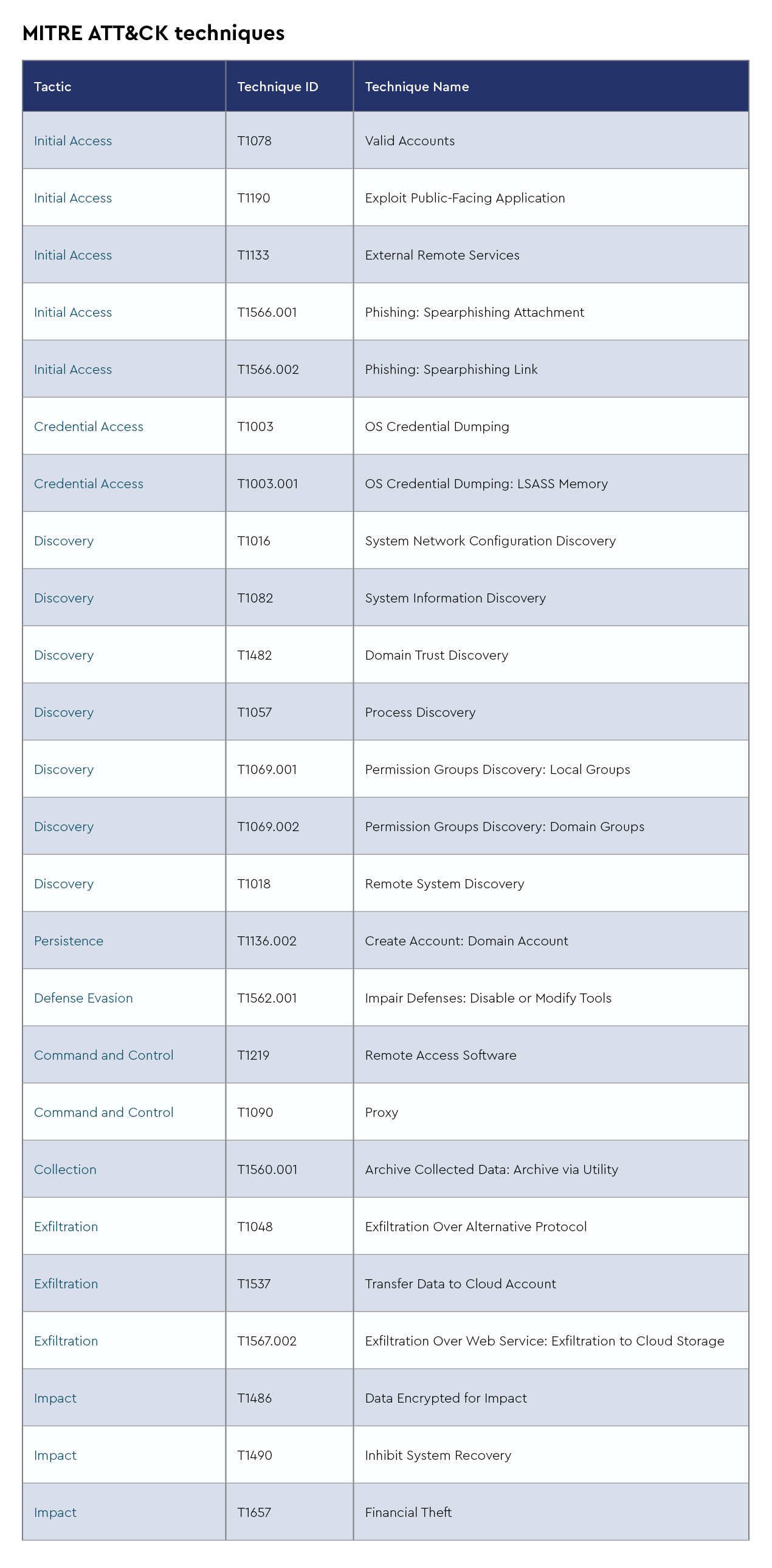
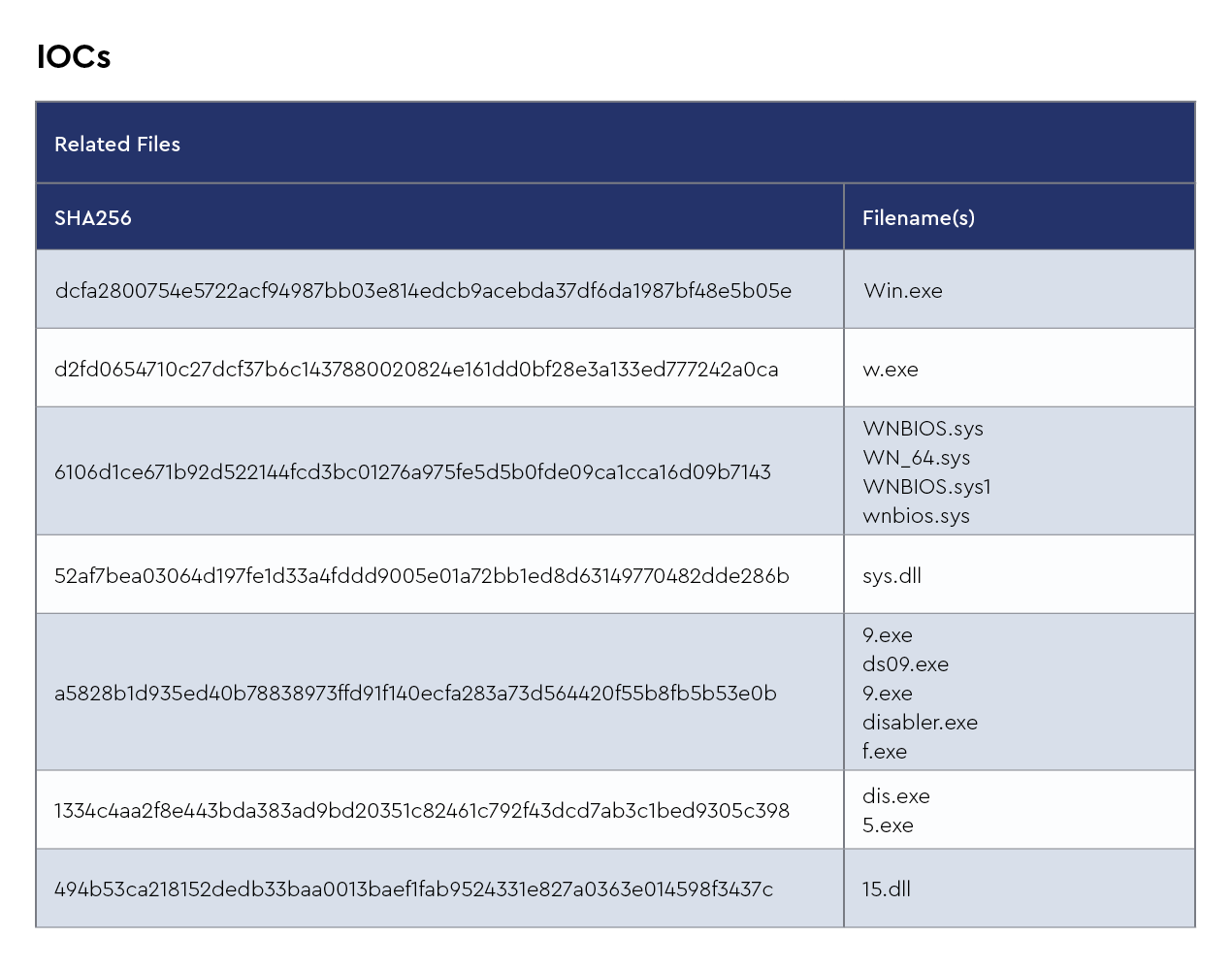
FAKEUPDATES/FakeUpdates/SOCGholish
FakeUpdates, also known as FAKEUPDATES or SocGholish, is a prevalent malware campaign that emerged around 2018, characterized by its use of social engineering techniques to trick users into downloading malicious software disguised as legitimate updates. This malware is primarily delivered through compromised websites, where users are prompted with fake update notifications, typically for common software such as Adobe Flash Player or browser updates. These prompts are designed to appear authentic, exploiting users’ trust and urgency to keep their software up-to-date.
Once the user initiates the download, the malware installs a backdoor on the system, providing attackers with remote access and control. FakeUpdates is often used as a delivery mechanism for additional payloads, including ransomware, banking trojans, and information stealers. The attackers leverage this access to exfiltrate sensitive data, deploy further malware, or use the compromised systems for broader campaigns.
The widespread use of compromised legitimate websites and the convincing nature of the fake update prompts make FakeUpdates a significant threat, capable of impacting a wide range of users and organizations. Its persistence and adaptability in evading detection underscore the importance of robust cybersecurity practices and user education to mitigate such threats.
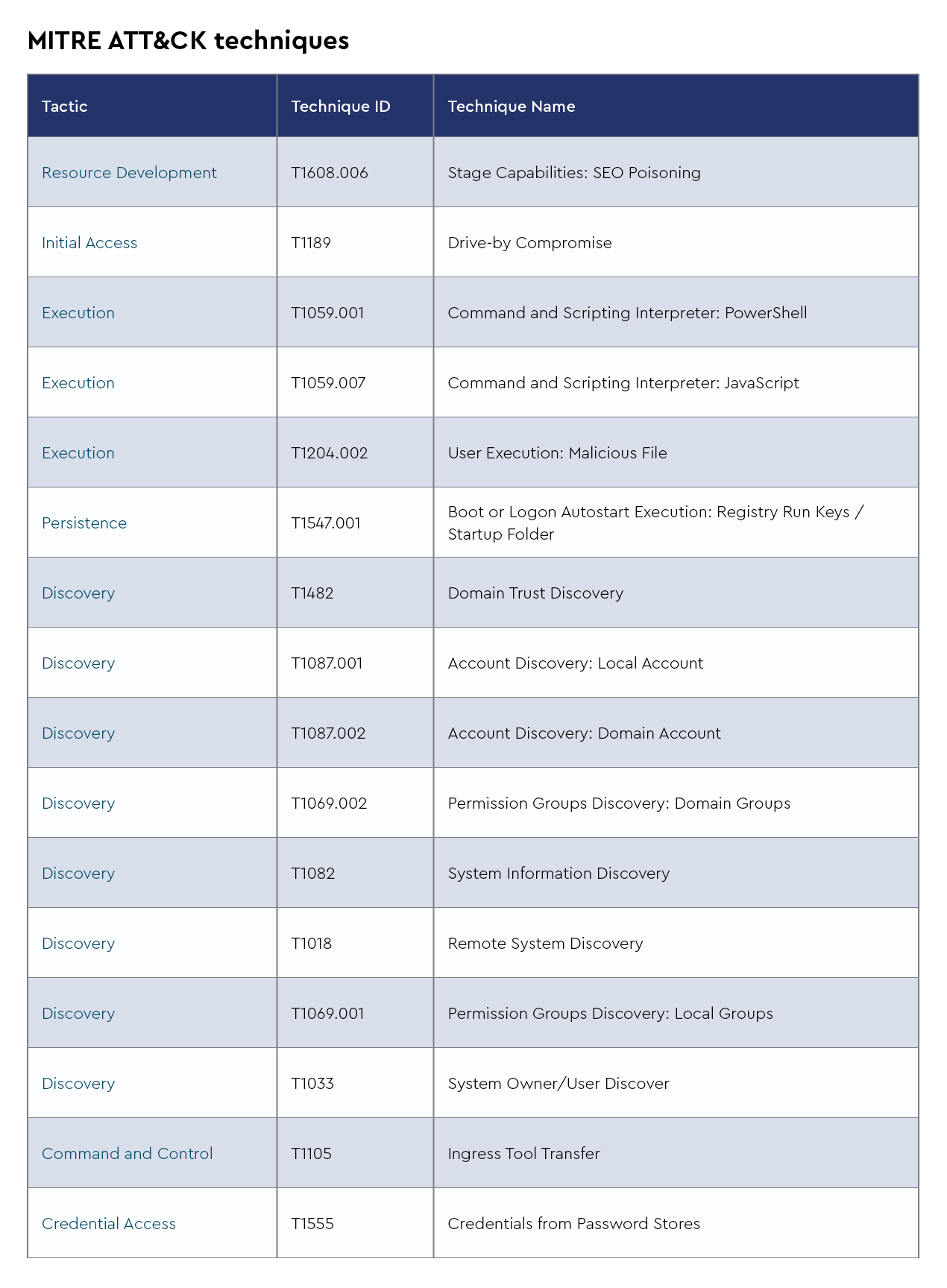
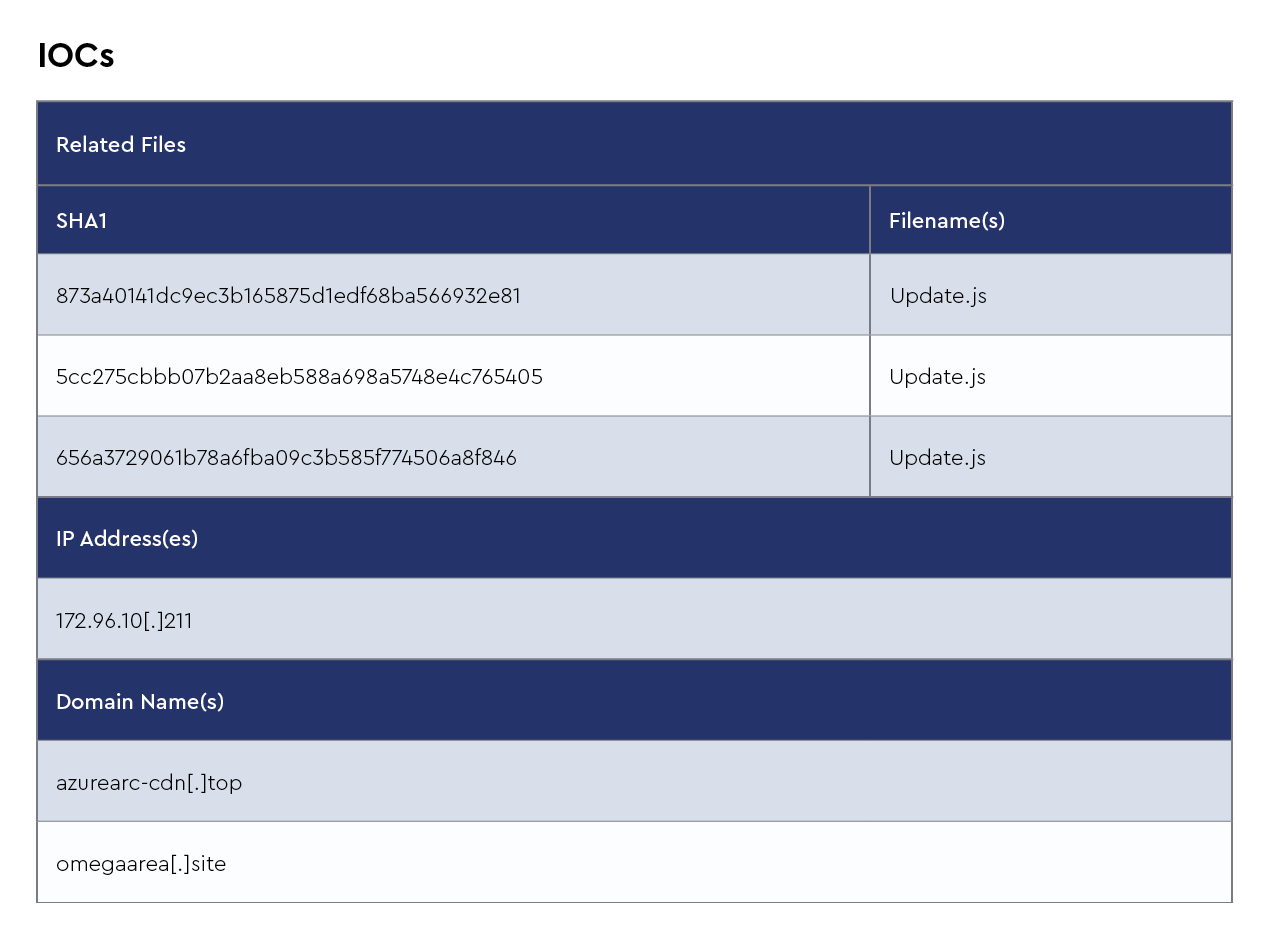
Fog
Fog ransomware is a new and emerging ransomware strain identified in May 2024 by Arctic Wolf Labs. This malware primarily targets US-based educational institutions and recreation centers, leveraging compromised VPN credentials for initial access. The attackers use techniques such as pass-the-hash attacks and credential stuffing to establish control, often gaining access to Windows servers via remote desktop protocol (RDP) and deploying the ransomware payload. Some key characteristics include:
- Encryption behavior: Fog encrypts victim files and appends extensions such as .FOG or .FLOCKED, and the ransomware is multithreaded, using a number of logical processors to optimize encryption speed
- Backup removal: It disables critical recovery mechanisms, including shadow copies and backup systems such as Veeam, making data recovery challenging without paying the ransom
- System manipulation: Fog terminates specified processes and stops services to ensure it can encrypt files without interference
- Command and control: Unlike many ransomware families, Fog does not currently rely on a public extortion portal, although some evidence suggests a move toward double extortion tactics involving data theft
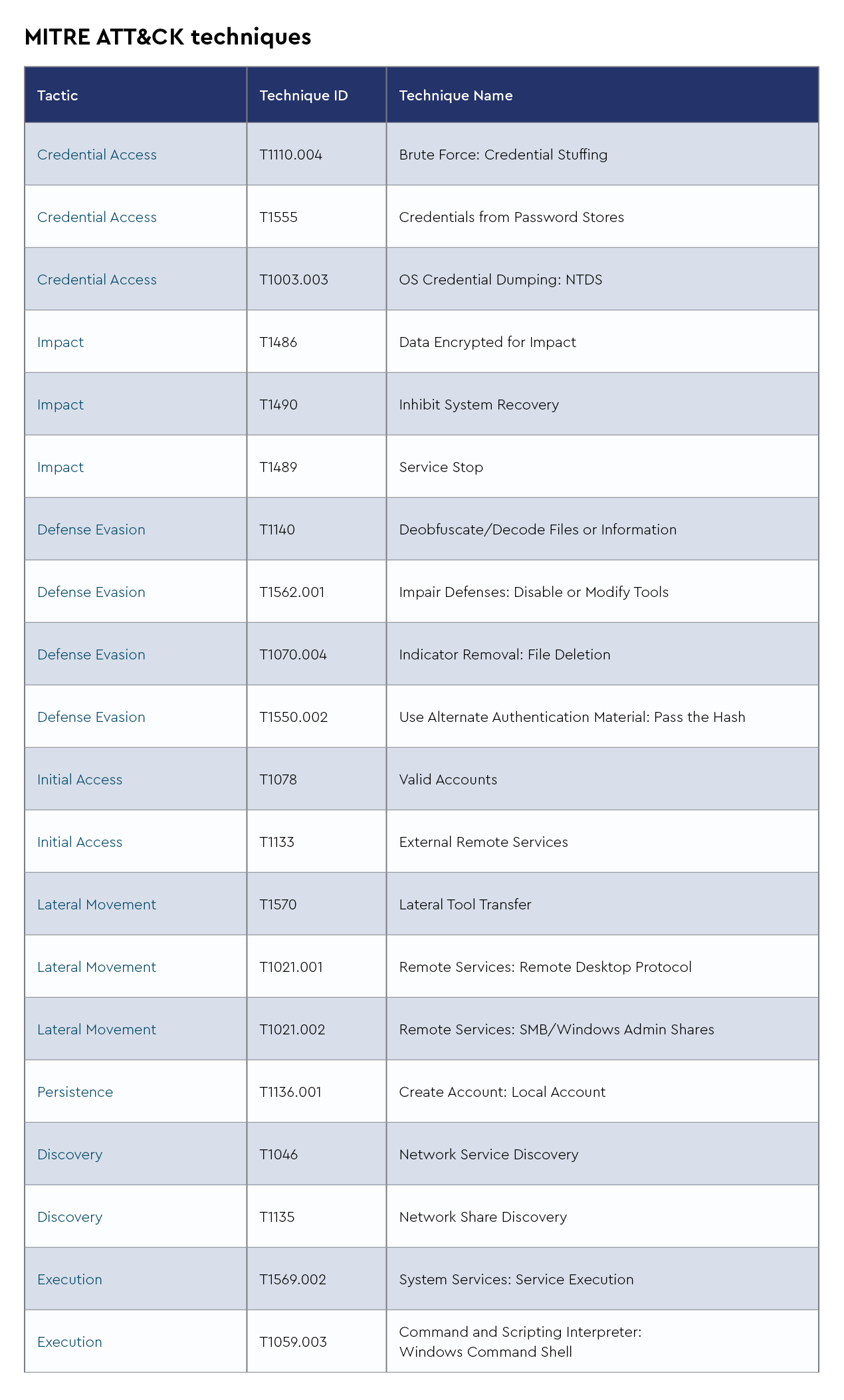
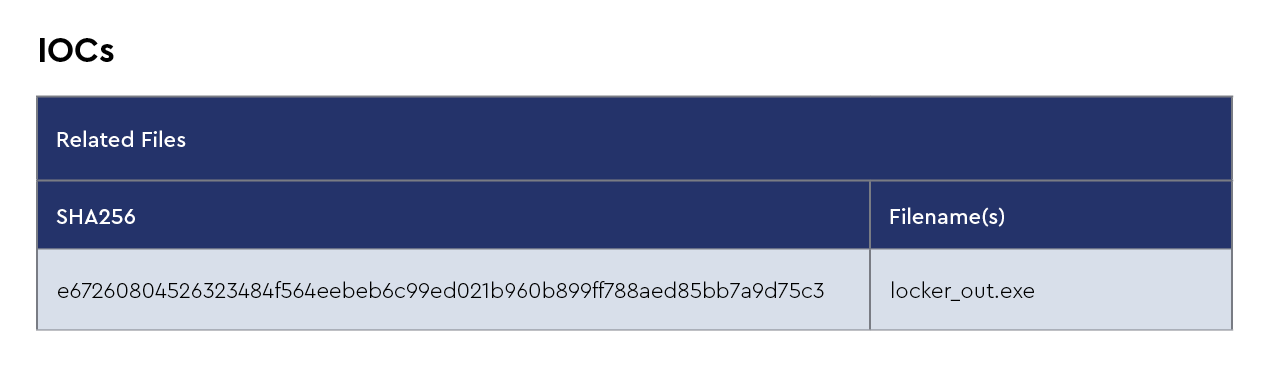
AsyncRAT
AsyncRAT is a remote access trojan that allows unauthorized individuals to gain remote control over compromised computers. It is a versatile and powerful tool used by cybercriminals to carry out various malicious activities.
AsyncRAT provides a wide range of features, including remote desktop control, file management, keylogging, webcam and microphone access, and the ability to execute arbitrary commands on the compromised system. It can be distributed through various means, such as phishing emails, malicious downloads, or exploiting vulnerabilities in software.
Once a computer is infected with AsyncRAT, the attacker gains complete control over the compromised system, enabling them to steal sensitive information, install additional malware, or use the compromised machine as a launching pad for further attacks. The trojan is designed to remain undetected by antivirus software and employs techniques to evade detection and maintain persistence on the compromised system.
Monthly newsletter summary
The following is a summary of articles shared in the CRU newsletter during the month of November.
New ADP-Branded Phishing Campaign Attempts Exploit of Old WinRAR Vulnerability
ConnectWise identified a phishing campaign impersonating ADP, distributing malicious ZIP files exploiting WinRAR vulnerability CVE-2023-38831. The attack uses fake login pages to deliver Vidar stealer malware via a crafted RAR archive containing decoy and malicious files. The exploit executes malware when users interact with seemingly benign files. Threat actors use this method to harvest sensitive data. To defend against such threats, apply software patches, train users to recognize phishing attempts, and use robust endpoint protection solutions to block malicious activities proactively.
Critical D-Link VPN Router Vulnerability Won’t Be Patched
D-Link has warned users to replace EOL VPN routers, including the DSR-150, DSR-250, DSR-500, and DSR-1000AC, due to an unpatchable RCE vulnerability allowing unauthenticated code execution. These routers pose a critical risk, enabling attackers to intercept network traffic or deploy malware. This highlights ongoing issues with outdated edge devices, which are prime targets for exploitation due to their high exposure and neglected updates. To mitigate risks, SMBs and MSPs should adopt proactive device lifecycle management, regular audits, and integrate edge devices into broader security frameworks.
The GoLo loader, written in Golang, facilitates Vidar and Lumma infostealers using anti-analysis techniques such as cursor tracking and random sleep intervals. It decrypts payloads using AES and dynamically selects injection targets by scanning binaries for specific markers (e.g., “NETFramew”). While often injecting into BitLockerToGo.exe, it adapts to other binaries via process hollowing, using standard API calls to replace their memory with malicious payloads. This adaptability highlights its flexibility for diverse malware deployment, stressing the importance of defenses such as monitoring suspicious activity and updating endpoint protections.
Ransomware Attack Disrupts Global Retail and Supply Chains
On November 21, 2024, Blue Yonder, a supply chain software provider, suffered a ransomware attack disrupting managed services for major clients, including Starbucks, Morrisons, and Sainsbury’s. The breach impacted payroll, scheduling, inventory management, and product availability, forcing manual operations and highlighting vulnerabilities in third-party cloud reliance. While no group claimed responsibility, recovery efforts are ongoing. With holiday demand amplifying the risks, the incident underscores the importance of robust cybersecurity and contingency planning to safeguard mission-critical supply chain infrastructure during high-pressure periods.
New ConnectWise SIEM signatures
Several new ConnectWise SIEM detection signatures were added in November 2024. These include:
- [EA][CRU][Windows] Suspicious file in Users Public directory
Techniques detected: [T1564.012] - Hide Artifacts: File/Path Exclusions
Description: Attackers have been observed placing tools and malicious executables in the \Users\Public directory due to loose permissions. Executables running from these directories should be investigated for malicious activity. Any files in videos, music, or pictures other than video, audio, or image files should be verified by the customer.
- [CRU][Windows] LSASS PID Enumeration Attempt Detection
Techniques detected: [T1003.001] OS Credential Dumping: LSASS Memory
Description: This detection identifies attempts to find the Process ID of the local security authority subsystem service (LSASS) on Windows systems, which may indicate credential harvesting or malicious reconnaissance. LSASS handles security policies, user authentication, and password changes, making its PID valuable for attackers aiming to dump its memory for credentials. Monitoring and alerting on LSASS PID enumeration helps detect potential credential theft or misuse of administrative privileges early.





