The ACSC Essential 8 risk mitigation strategies explained
Australians report cybersecurity incidents to cyber.gov.au every 10 minutes, and two out of five SMBs have experienced cyberthreat incidents worthy of reporting. Additionally, experts say that IT solutions providers are becoming the new favourite target of threat groups.
These are worrying stats that clearly show it's not a matter of if but when you or a client become a target to cyberthreats. It's especially troubling for IT solution providers when you consider that 50% of SMBs learn about cybersecurity from technology partners and business peers—essentially, what you know is what your client knows. Therefore, it's crucial to be on top of the latest trends, strategies, and best practices to combat the current threat landscape to protect your business and clients from the potentially devastating effects of a cyberattack
To help Australian companies meet these ever-evolving threats, the Australian Cyber Security Centre (ACSC) released the Essential Eight mitigation strategies, designed solely to help businesses proactively protect themselves. However, the strategies have led to more questions than answers in some cases.
In this first of a nine-part blog series, you'll get an overview of the Essential Eight framework and strategies and steps for implementing these critical controls.
What is the ACSC Essential 8?
The ACSC Essential Eight is a prioritised set of mitigation strategies or controls for building cyber resilience and protecting Australian businesses from cyberattacks. Originally published by the Australian Signals Directorate (ASD) in 2017, it is now maintained under the banner of the ACSC as a subset of the Strategies to Mitigate Cyber Security Incidents framework.
Unlike many frameworks, which are vendor agnostic, the ACSC Essential Eight is tightly focused on providing guidance on protecting Microsoft Windows-based internet-connected networks. This does not mean the mitigation strategies cannot be applied to other platforms or operating systems; it is just that they are not the focus of the Essential Eight.
Lastly, under the ACSC Essential Eight banner, there is no direct external, third-party independent certification requirement. However, you may find this framework must be implemented due to external regulatory or contractual needs.
The ACSC Essential 8 explained
The term essential in Essential Eight refers to the Relative Security Effectiveness Rating of the controls in the Strategies to Mitigate Cyber Security Incidents framework. Each of the 37 controls in this framework is rated on an effectiveness scale from limited to essential. The Essential Eight are the eight controls with a rating of essential.
While the Essential Eight outlines a minimum, or fundamental, set of mitigation measures an organisation needs to implement to defend their environment, additional mitigation strategies and security controls must be considered. Learn more in the ACSC Strategies to Mitigate Cyber Security Incidents framework and the ACSC Information Security Manual (ISM).
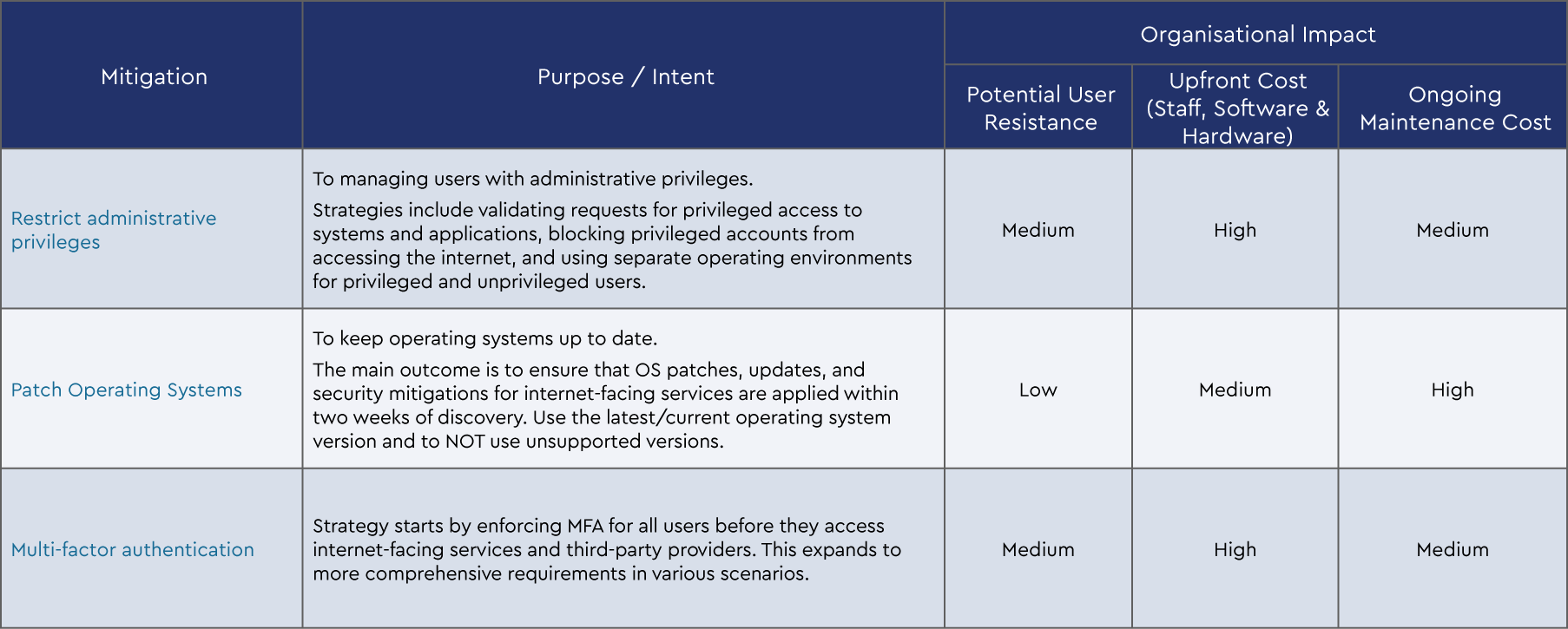
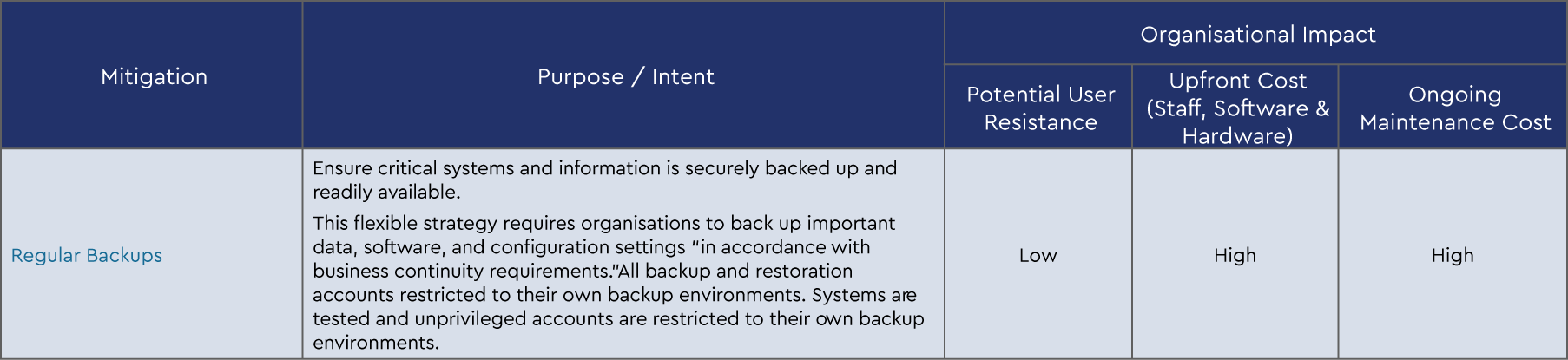
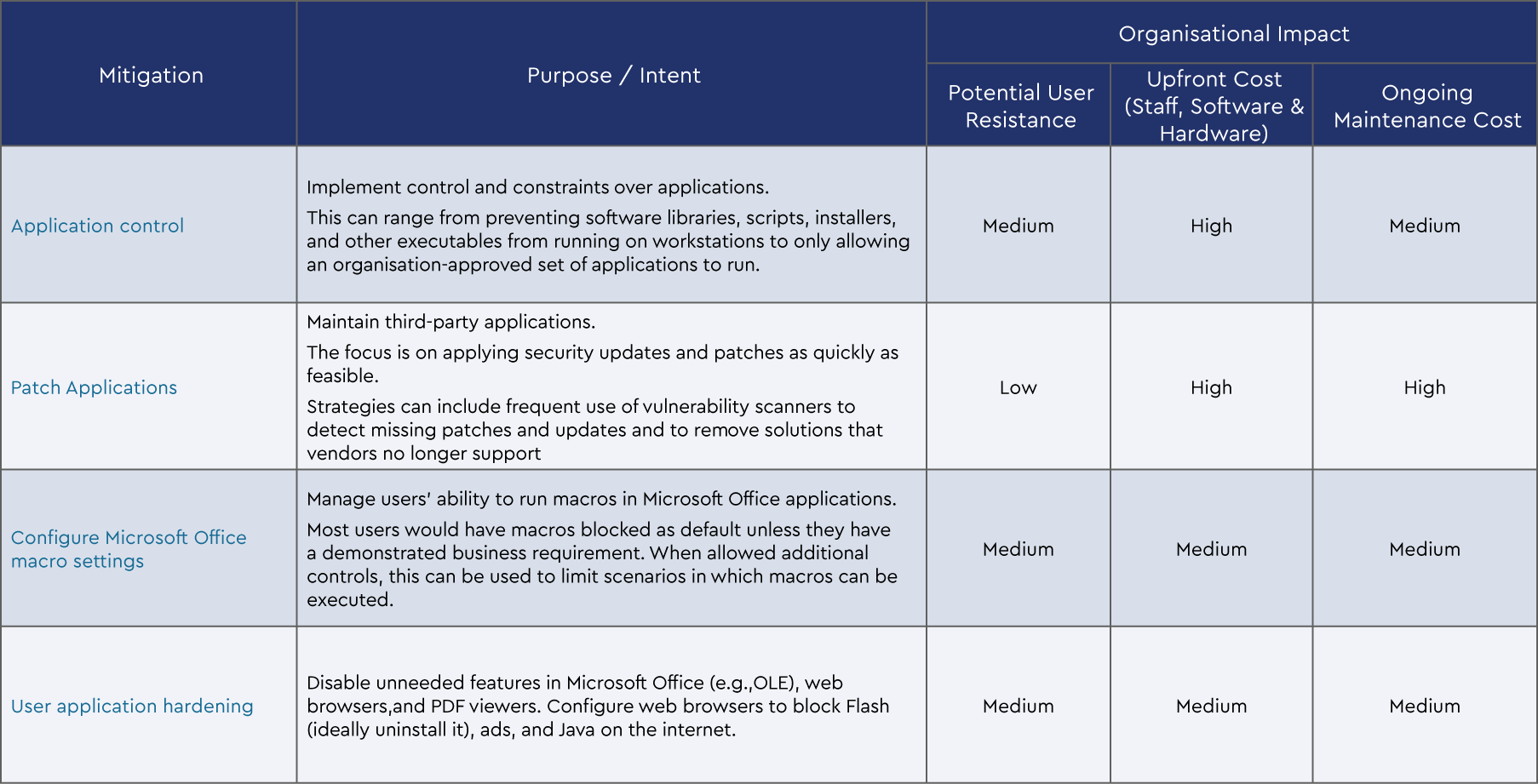
The Essential 8 Mitigation strategies are as follows:
- Application control
- Patch applications
- Configure Microsoft Office macro settings
- User application hardening
- Restrict administrative privileges
- Patch operating systems
- Multi-factor authentication
- Regular backups
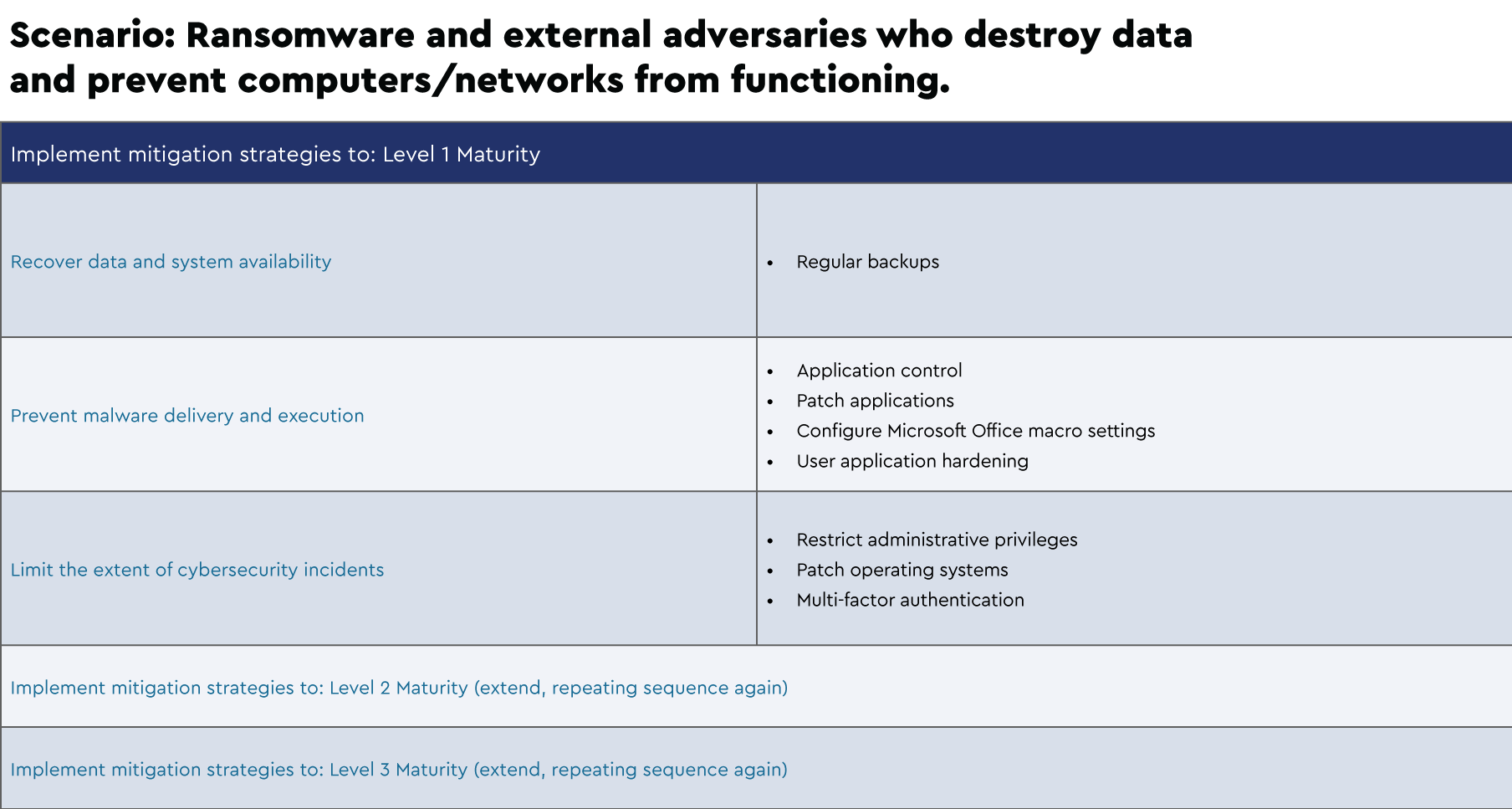
Each strategy is broken up into three levels of maturity based on the increasing level of the adversary tradecraft the business is defending against. We can summarise the Essential Eight mitigation strategies and the intent of each strategy as follows:
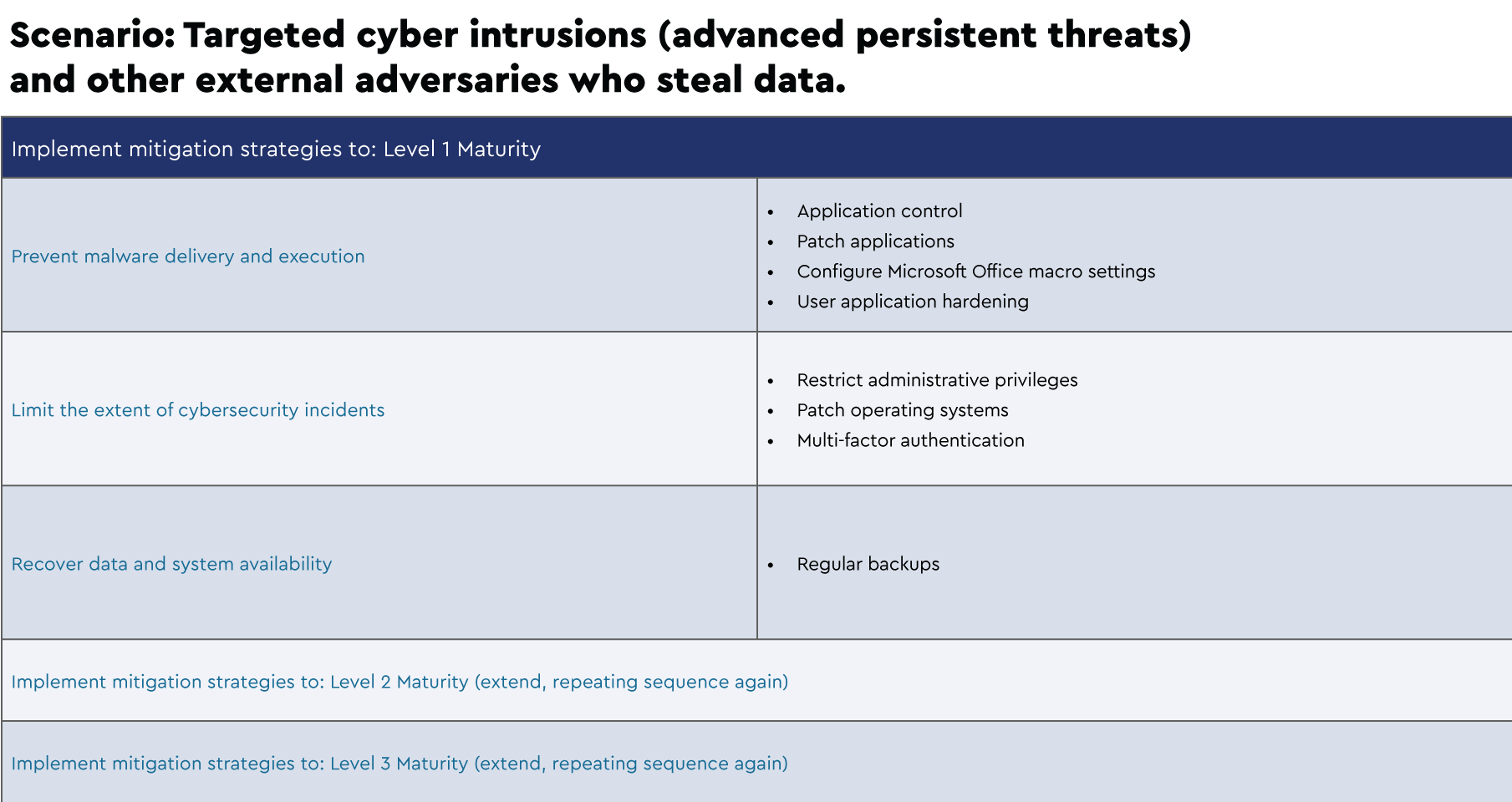
Focus: Mitigation Strategies to Prevent Malware Delivery and Execution
Focus: Mitigation Strategies to Limit Extent of Cyber Security Incidents
Focus: Mitigation Strategies to Recover Data and System Availability
The Essential 8 Maturity Levels
To assist with implementing the Essential Eight, the ACSC has defined four maturity levels for each strategy based on increasing levels of tradecraft. Understanding the intent of these maturity levels can assist in determining the maturity level the organisation should be targeting.
Maturity Level Zero
As the starting point, this maturity level indicates significant weakness in the security posture for the strategy as the organisation is not meeting Level One, Level Two, or Level Three Maturity requirements.
Maturity Level One
Here you are defending against adversaries that are content to leverage commodity tradecraft that is widely available to gain access to and likely control systems.
Maturity Level Two
Here you are defending against adversaries operating with a modest step-up in capability from maturity level one. These adversaries are willing to invest more time in a target and, perhaps more importantly, in the effectiveness of their tools.
Maturity Level Three
Here you are defending against adversaries who are more adaptive and less reliant on public tools or techniques. They are more able to leverage opportunities provided by weaknesses in the security posture. This allows adversaries to extend their initial access and evade detection to solidify their presence in the environment.
How to implement the Essential 8
When setting out to implement the Essential Eight, organisations should first identify their maturity level based on their understanding of their own risk profile. Any security posture should always be implemented using a risk-based approach, and exceptions should be well documented, reviewed, and countered with compensating controls.
These strategies complement each other, so the same maturity level should be targeted for all eight mitigation strategies. In other words, all mitigation strategies should progressively be implemented at the same maturity level before starting to move to a higher level of maturity. It might be that an organisation already has portions of these controls in place, which can mean that implementation in some areas is more about tightening and extending those controls.
Below are examples of suggested implementation schedules that were extrapolated from the Strategies to Mitigate Cyber Security Incidents framework for several scenarios:
With this clearer understanding of the Essential Eight, how it helps protect your business and clients, and suggestions for implementing the framework, join us for the next blog in the series, where we'll discuss the first Essential Eight mitigation strategy, application control. We’ll cover the control and constraints you have over users' applications, including stopping software libraries, scripts, installers, and other executables from running on workstations to an organisation-approved set.