Monthly Threat Brief: March 2024
Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU).
In this threat brief, we will provide raw data statistics, intel on specific threats, and a list of new detection signatures added to the ConnectWise SIEM™ throughout the month of March.
For a more detailed explanation of the overall trends and analysis of these numbers, check out our annual and quarterly threat reports. For comparison, February’s threat brief can be found here.
March 2024 stats
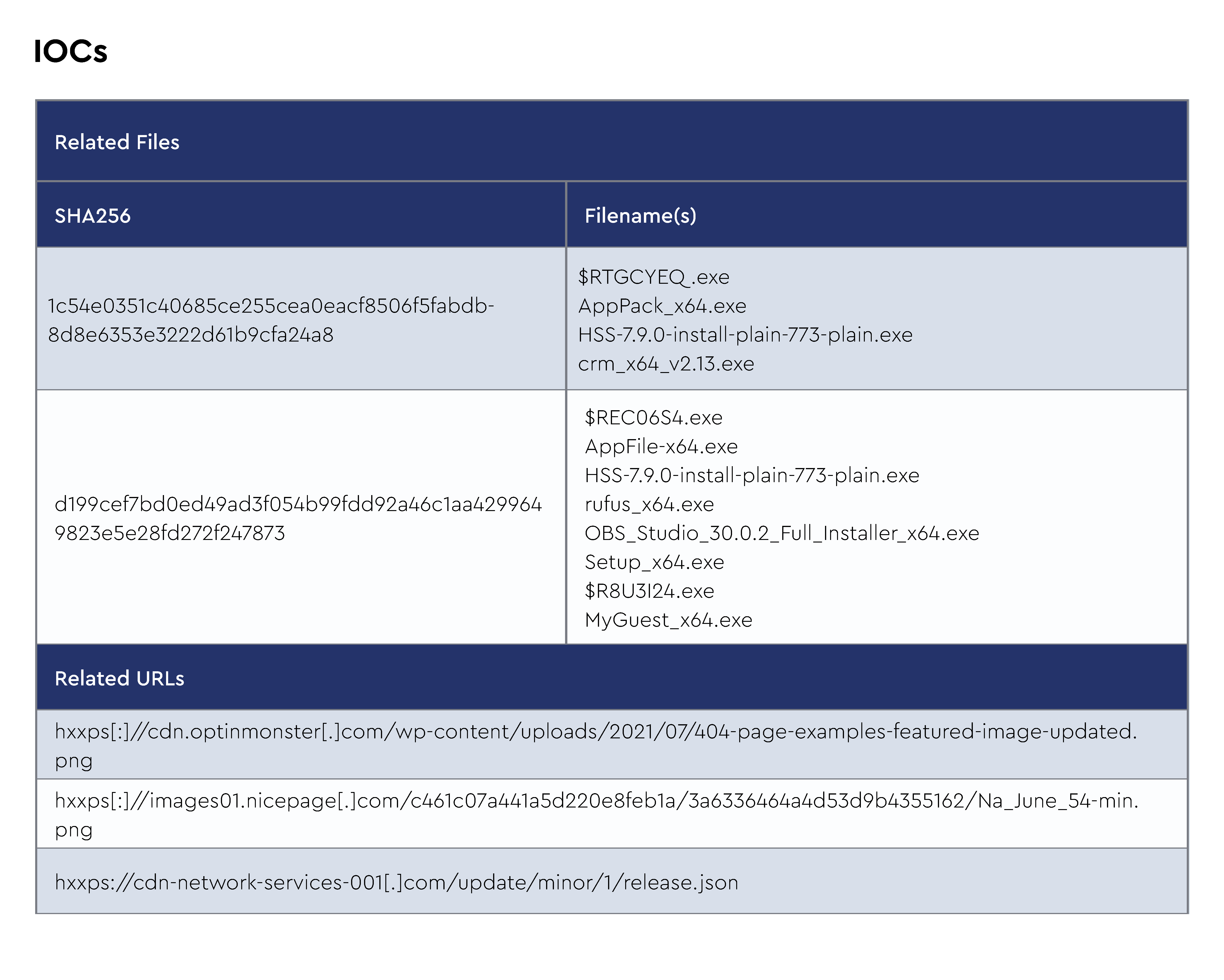
IOCs
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected. We intend to launch streaming threat feeds based on this data later this year—stay tuned!
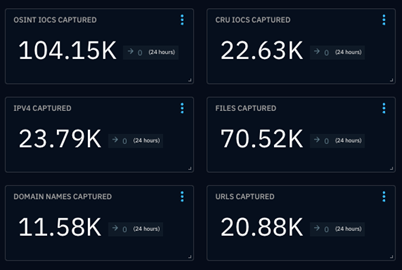
Figure 1: Summary of IOCs collected in March 2024
TTPs
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for February 2024—provided for comparison—and March 2024.
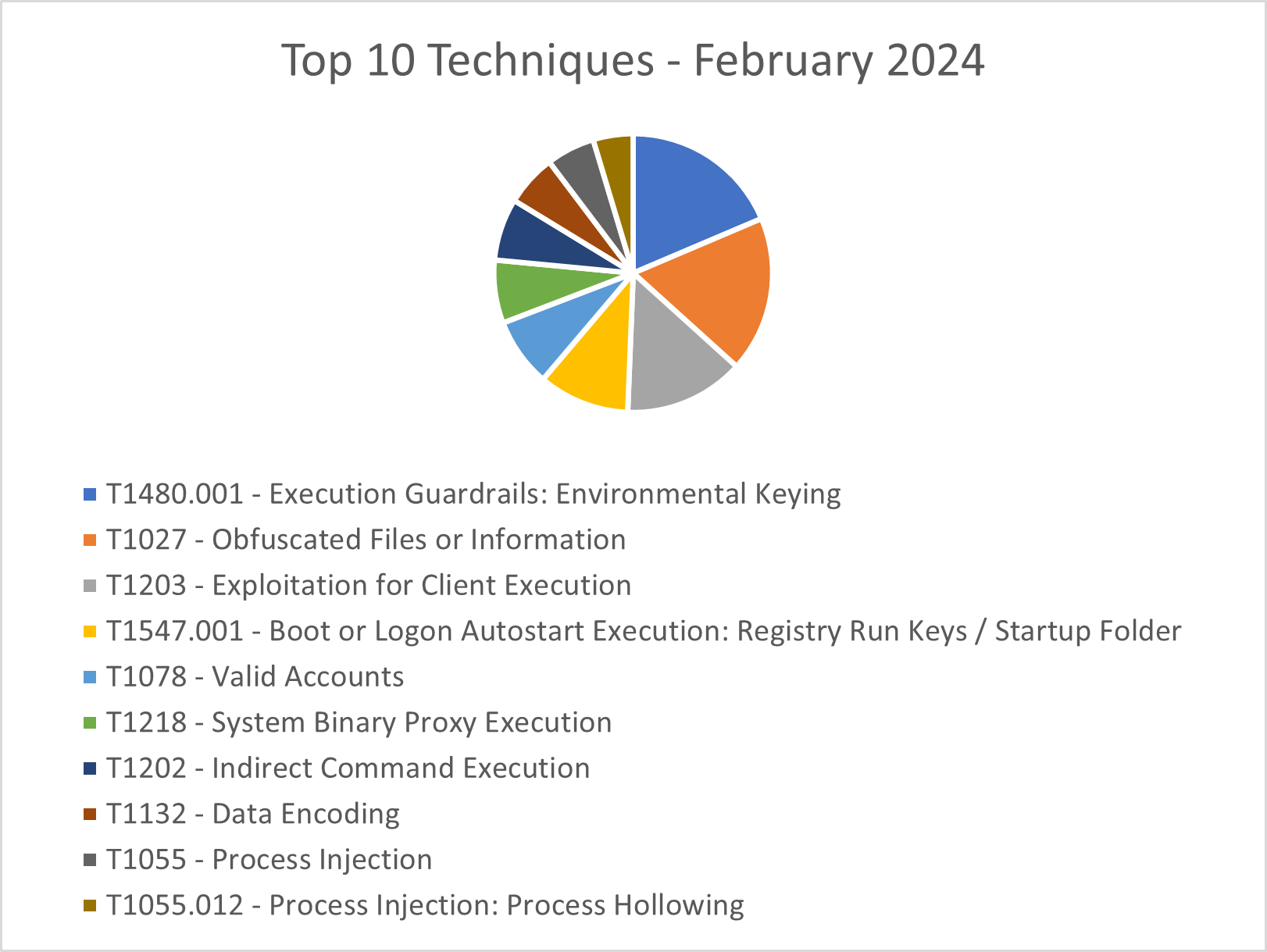
Figure 2: Top 10 MITRE ATT&CK techniques observed in February 2024
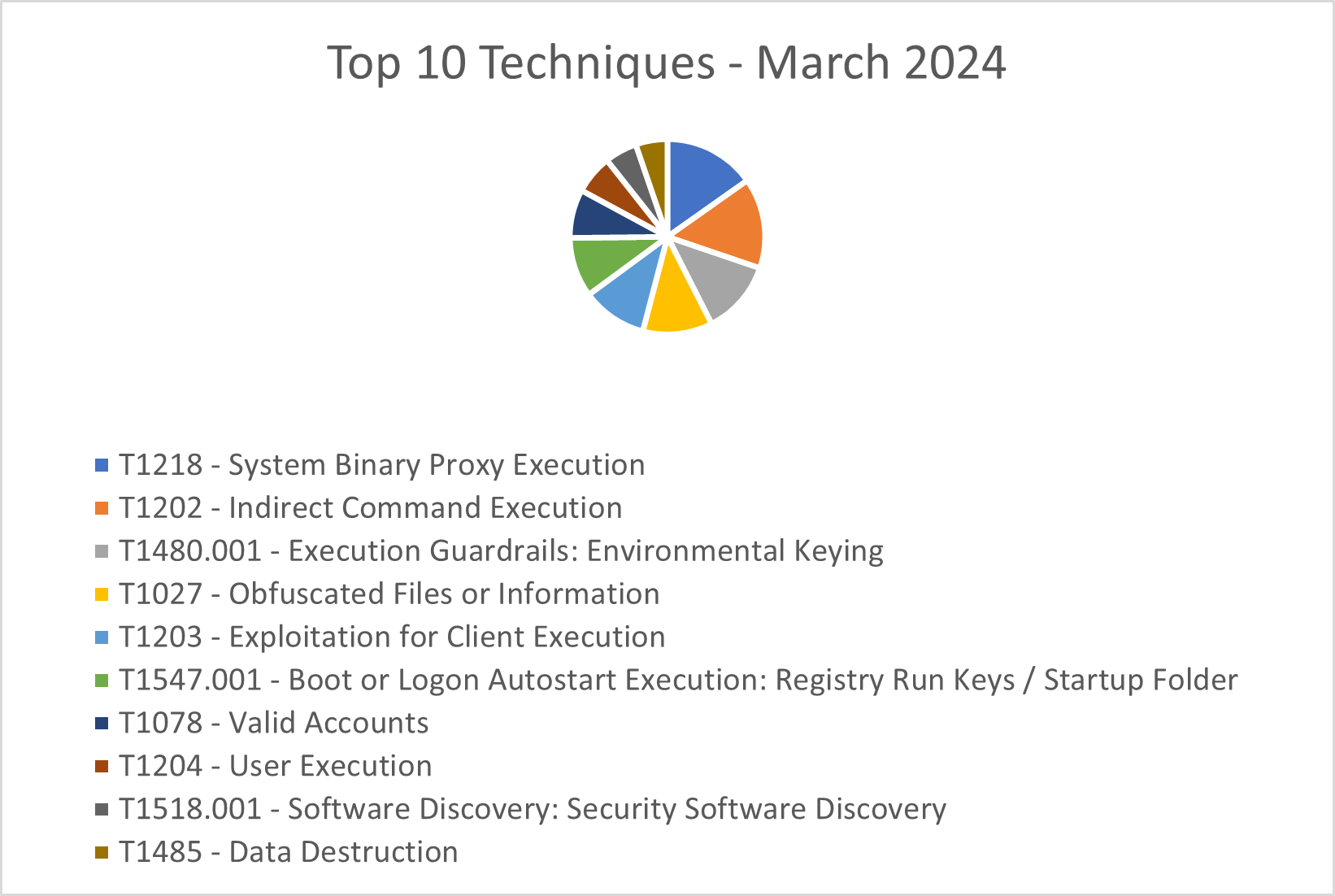
Figure 3: Top 10 MITRE ATT&CK techniques observed in March 2024
Latest threats
Each month we highlight threats that we have seen targeting our MSP partners and their clients. This month, the ConnectWise SOC saw multiple incidents of GhostPulse and Gootloader—both of which are loaders used during initial access to download additional malware
Rusty Loader
The CRU has been tracking a series of malware droppers written in Rust known as Rusty Loader. As a malware dropper, Rusty Loader’s purpose is to download and install additional malware. It appears to primarily be used to load a malicious version of Brute Ratel, an adversary emulation command and control software designed for penetration testers, but frequently used by threat actors for remote administration.
Rusty Loader employs multiple defense evasion techniques to avoid detection, as well as several anti-sandbox techniques to make it more difficult to analyze. Rusty Loader seems to primarily spread through [T1189] Drive-by Compromise using [T1608.006] SEO Poisoning and [T1583.008] Malvertising. When it first loads, it checks to see if it is being run in a debugger or if the filename has been changed, and then it looks at CPU and user information to try to determine if it is being run inside a sandbox. If it determines that it is being run in a sandbox, then instead of running, it loads a 404 image from different sources, such as hxxps[:]//cdn.optinmonster[.]com/wp-content/uploads/2021/07/404-page-examples-featured-image-updated.png

Figure 4: 404 image example
Some of the filenames we have seen this loader using include “HSS-7.9.0-install-plain-773-plain.exe” which seems to be mimicking VPN software, “Hotspot Shield 7.9.0”, as well as “OBS_Studio_30.0.2_Full_Installer_x64.exe” which is impersonating some common video recording and streaming software. This method of impersonating commonly used free software is similar to the method we observed last year when threat actors were spreading a malicious version of “Advanced IP Scanner.”
Xz Official Package Compromised (CVE-2024-3094)
xz is a commonly used open-source compression tool commonly used in Linux and other Unix-based operating systems such as macOS. It is common enough that xz is the format typically used to package the Linux kernel, making it a requirement to even boot a Linux system.
At the end of March, a backdoor was discovered in the official xz-utils package. The malicious code began appearing in the official repo in a commit pushed on February 23, 2024 and was discovered a little over a month later on March 28.
The malicious code was pushed by a maintainer known as “Jia Tan.” Jia Tan began submitting patches to xz in October 2021 and then began a social engineering campaign in the xz-devel mailing list, gaining trust and regularly contributing to the project. They were officially given access to become a maintainer in September 2022. We found a detailed timeline available here.
The actual backdoor is very indirect and is only exploitable under very specific circumstances, allowing a remote unprivileged user to connect to a system via public SSH ports. The malicious version of xz was included in Fedora Rawhide, Fedora 40, and some testing, unstable, and experimental distributions of Debian. The malicious code compromised the build process in such a way that a normal user downloading and compiling the code would not end up with the backdoor; however, the build process used as part of different Linux distributions would. Overall, the backdoor was discovered quickly enough that the impact was limited.
New ConnectWise SIEM signatures
Several new ConnectWise SIEM detection signatures were added in March 2024. These include:
- [O365] full_access_as_app Role Granted
Technique detected: [T1484] Domain Policy Modification
Description: This alert is designed to detect the assignment of the 'full_access_as_app' EWS (Exchange Web Services) role to an instance of an application (i.e., a service principal). This role includes access to all Exchange mailboxes and can be used for malicious purposes. We recommend verifying whether this assignment is expected. The application assigned this role can be seen in Discover under the "modifiedProperties" nested field under the "NewValue" subfield above the Service Principal Display Name.
- [CRU][Windows] Potentially Unwanted Proxyware – EarnApp
Technique detected: [T1496] Resource Hijacking
Description: This event notification triggers when an executable known to be related to usage of EarnApp is observed. This application offers users monetary compensation in exchange for usage of their internet connection. This leads to a network connection being used as a Residential Proxy, which can be used to proxy malicious activity, causing traffic from this device to potentially be flagged as malicious. It may also indicate a user violating company policy.
- [CRU][Windows] Potentially Unwanted Proxyware – Honeygain
Technique detected: [T1496] Resource Hijacking
Description: This event notification triggers when an executable known to be related to usage of the Honeygain is observed. This is proxyware that offers a user money in exchange for use of their internet connection. Installing it leads to a network connection being used as a Residential Proxy, which can be used to proxy malicious activity, causing traffic from this device to potentially be flagged as malicious.
- [CRU][Windows] Potentially Unwanted Proxyware - Peer2Profit
Technique detected: [T1496] Resource Hijacking
Description: This event notification triggers when an executable known to be related to usage of the Peer2Profit is observed. This is proxyware that offers a user money in exchange for use of their internet connection. Installing it leads to a network connection being used as a Residential Proxy, which can be used to proxy malicious activity, causing traffic from this device to potentially be flagged as malicious.
- [CRU][Windows] Potentially Unwanted Proxyware - Pawns.app
Technique detected: [T1496] Resource Hijacking
Description: This event notification triggers when a library (dll) or executable known to be related to the usage of the Pawns.app is observed. This is proxyware that offers a user money in exchange for use of their internet connection. Installing it leads to a network connection being used as a Residential Proxy, which can be used to proxy malicious activity, causing traffic from this device to potentially be flagged as malicious.
- [CRU][Windows] Potentially Unwanted Proxyware - Infatica SDK
Technique detected: [T1496] Resource Hijacking
Description: This event notification triggers when either a library file (dll) or executable known to be related to the usage of the Infatica SDK is observed. This SDK allows developers to integrate proxyware capabilities into their applications. When installing an application a user may be prompted to allow use of their internet connection in exchange for free access to premium features. Opting in leads to a network connection being used as a Residential Proxy, which can be used to proxy malicious activity, causing traffic from this device to potentially be flagged as malicious.
- [CRU][Windows] Potentially Unwanted Proxyware - Bright Data SDK
Technique detected: [T1496] Resource Hijacking
Description: This event notification triggers when either a library file (dll) or executable known to be related to the usage of the Bright Data SDK is observed. This SDK allows developers to integrate proxyware capabilities into their applications. When installing an application a user may be prompted to allow use of their internet connection in exchange for free access to premium features. Opting in leads to a network connection being used as a Residential Proxy, which can be used to proxy malicious activity, causing traffic from this device to potentially be flagged as malicious.
- [CRU][Windows] Cscript or Wscript Execution Javascript File with MS-DOS Short Name
Technique detected: [T1059.007] Command and Scripting Interpreter: JavaScript
Description: During execution, Gootloader samples copy one stage to disk and persistently executes it using cscript.exe. During this procedure, the cscript.exe command line references the malicious script using an 8.3 short filename, which is an uncommon pattern.
- [CRU][Windows] Gootloader Payload C2 IOC - xmlrpc.php in powershell script block
Technique detected: [T1071.001] Application Layer Protocol: Web Protocols
Description: Gootloader campaigns are known for dropping payloads that use C2s with xmlrpc.php in the URL. This will show up in PowerShell logs and will likely be observed along with obfuscated code. False positives could potentially occur with PowerShell scripts for remote activity with a WordPress site.
- [CRU][Windows] Kuiper Ransomware Artifacts
Technique detected: [T1486] Data Encrypted for Impact
Description: Ransom note README_TO_DECRYPT.txt is written to multiple directories. Kuiper encrypted files have the extension .kuiper.
New IDS signatures added in March 2024
[ConnectWise CRU] FortiGate FortiOS Out-of-Bound Write (CVE-2024-21762)
[ConnectWise CRU] JetBrains TeamCity Authentication Bypass (CVE-2024-27198) M1
[ConnectWise CRU] JetBrains TeamCity Authentication Bypass (CVE-2024-27198) M2
[ConnectWise CRU] SolarMarker VNC Client Beacon
[ConnectWise CRU] SolarMarker VNC Server ACK Response
[ConnectWise CRU] SolarMarker VNC Server PSH/ACK Response
[ConnectWise CRU] SolarMarker VNC Server PSH/ACK Response
[ConnectWise CRU] Potential Java Invocation Abuse
[ConnectWise CRU] Adobe ColdFusion Deserialization of Untrusted Data (CVE-2023-38203)
[ConnectWise CRU] Progress OpenEdge Authentication Bypass (CVE-2024-1403)
[ConnectWise CRU] UTF-8 Overlong Encoding Bypass (..) 2bytes
[ConnectWise CRU] UTF-8 Overlong Encoding Bypass (..) 3bytes
[ConnectWise CRU] UTF-8 Overlong Encoding Bypass (..) 4bytes
[ConnectWise CRU] Java RMI Protocol (StreamProtocol)
[ConnectWise CRU] Java RMI Protocol (SingleOpProtocol)
[ConnectWise CRU] Java RMI Protocol (MultiplexProtocol)
[ConnectWise CRU] Java RMI Protocol (Call)
[ConnectWise CRU] Java RMI Protocol (Ping)
[ConnectWise CRU] Java RMI Protocol (DgcAck)
[ConnectWise CRU] Java RMI Protocol (ProtocolAck)
[ConnectWise CRU] Java RMI Protocol (ProtocolNotSupported)
[ConnectWise CRU] Java RMI Protocol (ReturnData)
[ConnectWise CRU] Java RMI Protocol (PingAck)
[ConnectWise CRU] Potential Java Invocation Abuse M2
[ConnectWise CRU] CommVault CommServe MS-SQL EoP
[ConnectWise CRU] CommVault CommServe MS-SQL Impersonation (sqladmin_cv)
[ConnectWise CRU] Microsoft Windows Themes Spoofing (CVE-2024-21320)
[ConnectWise CRU] SolarWinds Security Event Manager AMF Deserialization RCE (CVE-2024-0692)
[ConnectWise CRU] MALWARE SafeRAT C2 Shellcode Response
[ConnectWise CRU] MALWARE SafeRAT C2 Second Stage Request
[ConnectWise CRU] MALWARE Stealit Infostealer Exfiltration
[ConnectWise CRU] MALWARE Loda Loader C2 Beacon M1
[ConnectWise CRU] MALWARE Loda Loader C2 Beacon M2
[ConnectWise CRU] MALWARE Loda Loader C2 Beacon Response M1
[ConnectWise CRU] MALWARE Loda Loader C2 Beacon Response M2
[ConnectWise CRU] Metasploit TCP Shell Session
[ConnectWise CRU] MALWARE Silverfox backdoor
[ConnectWise CRU] Fortra FileCatalyst Workflow 5.x RCE (CVE-2024-25153)
[ConnectWise CRU] QNAP NAS Authentication Bypass (CVE-2024-21899)
[ConnectWise CRU] HUNTING SVG Smuggling
[ConnectWise CRU] Progress Kemp Loadmaster Unauthenticated Command Injection (CVE-2024-1212)
[ConnectWise CRU] .NET Framework Information Disclosure Vulnerability (CVE-2024-29059) M1
[ConnectWise CRU] .NET Framework Information Disclosure Vulnerability (CVE-2024-29059) M2
[ConnectWise CRU] .NET Framework Leaked ObjRefs (CVE-2024-29059)





