The ConnectWise Cyber Research Unit™ (CRU) Monthly Threat Brief has been reformatted to provide even more relevant and actionable threat intelligence for managed service providers (MSPs) and their clients. This new structure ensures a clearer, more concise breakdown of key cyberthreats, helping security teams stay ahead of evolving risks.
Each month, this report will now feature:
- Top stories: A recap of the cybersecurity stories shared by the CRU from the past month
- Top vulnerabilities: The most exploited or recently disclosed vulnerabilities and their potential impact
- Top malware targeting MSPs: An overview of the most active malware observed by the ConnectWise security operations center (SOC) affecting MSPs and their customers
New malware approach: The Diamond Model of Intrusion Analysis
To improve the clarity and actionability of our malware intelligence, we’ve reformatted the malware section to follow key principles of the Diamond Model of Intrusion Analysis. This model structures threat intelligence by mapping adversary behaviors across four key areas:
- Adversary: The threat actors or groups deploying the malware
- Infrastructure: The command-and-control (C2) servers, domains, and delivery mechanisms used
- Capabilities: The malware’s functionalities, such as credential theft, persistence, or lateral movement
- Victimology: The industries, regions, or specific targets being affected
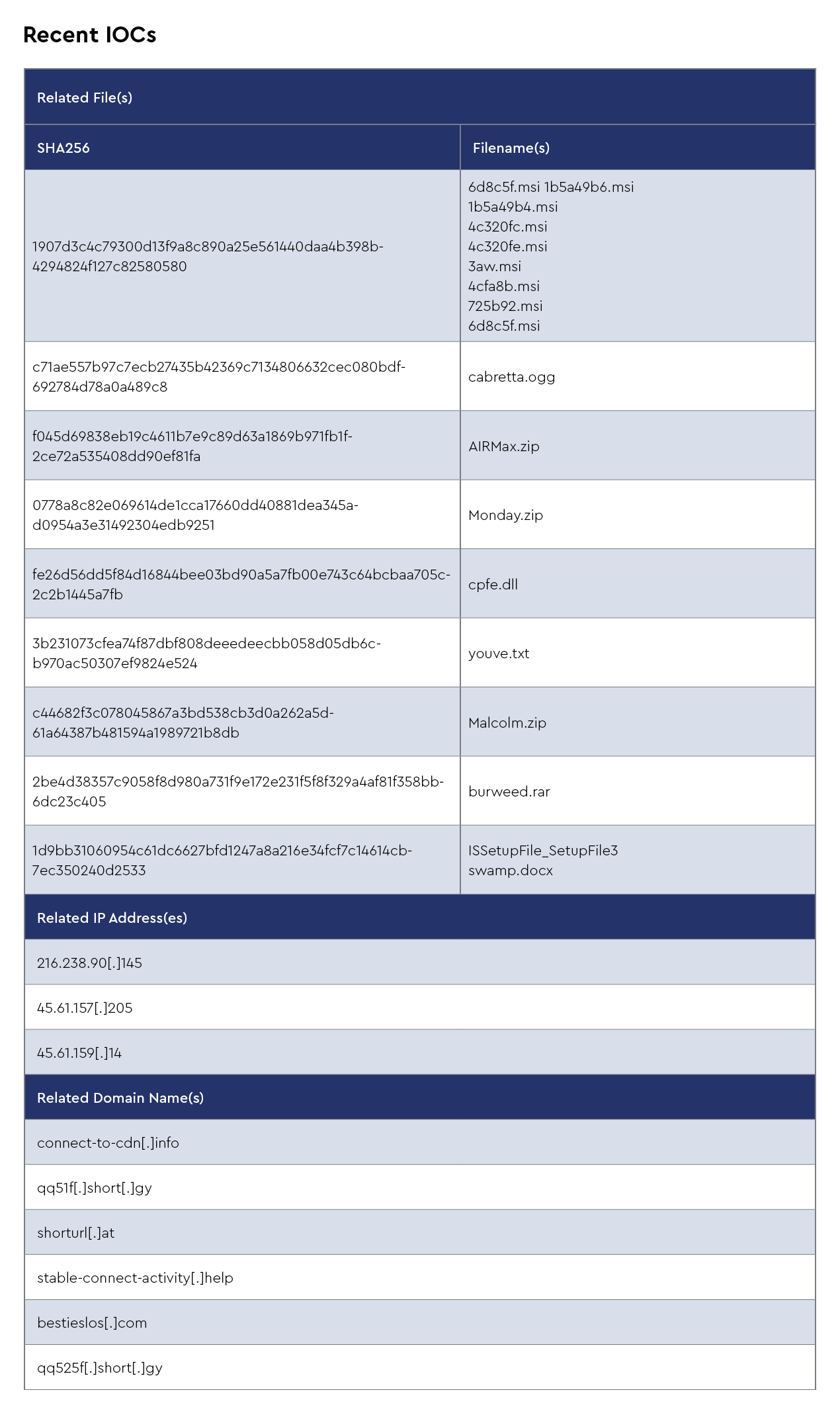
This structured approach enhances the context of each malware threat, making it easier for MSPs to understand who is attacking them, how they are doing it, and what defenses can be implemented. By combining this with indicators of compromise (IoCs), this reformat provides a more comprehensive and operational threat intelligence resource.
Top stories for February 2025
CVE-2025-21293: Microsoft Entra ID Privilege Escalation PoC Released
A proof-of-concept (PoC) exploit for CVE-2025-21293 has been released, highlighting a critical privilege escalation vulnerability in Microsoft Entra ID domain services. Patched in Microsoft’s January 2025 updates, this flaw allows attackers to gain SYSTEM privileges by abusing excessive permissions assigned to the “Network Configuration Operators” group. By inserting a malicious performance counter DLL into specific registry subkeys, attackers can execute arbitrary code when monitoring tools such as PerfMon.exe or WMI access the counters.
Security researchers and threat actors have taken an interest in the PoC, with increased scanning activity detected against vulnerable systems. Microsoft’s patch removes dangerous registry permissions, mitigating the issue, but unpatched systems remain at risk. Organizations should apply updates immediately or, if delayed, restrict group memberships and monitor for suspicious registry modifications to detect exploitation attempts.
What this means for MSPs
MSPs must ensure their clients promptly apply the patch to prevent privilege escalation attacks. Given Microsoft Entra ID’s critical role in authentication and access control, any delay in mitigation increases risk. MSPs should monitor registry activity for anomalies, enforce least privilege principles, and use endpoint detection and response (EDR) tools to detect potential exploitation attempts before they escalate.
PayPal "New Address" Phishing Scam Grants Attackers Remote Access
A sophisticated phishing campaign is abusing PayPal's legitimate "New Address" verification emails to deceive users into calling fraudulent support numbers. Attackers exploit PayPal's address update process by adding a new shipping address to their own account, triggering an automatic email from "service@paypal[.]com" to the victim. The scam works by inserting a fake message in the “Address 2” field, falsely claiming an unauthorized purchase has been made and urging the recipient to call a provided phone number. Because these emails originate from PayPal's actual servers, they pass email security checks, making them highly convincing.
Victims who call the scammer’s number are connected to fraudsters posing as PayPal support, who claim their account is compromised. The attackers then manipulate users into installing remote access software, such as ScreenConnect™, under the guise of account recovery assistance. Once installed, the attackers gain control of the victim's system, potentially leading to data theft, malware deployment, or unauthorized financial transactions. The abuse of PayPal’s legitimate email system allows this scam to bypass traditional phishing detection, increasing its effectiveness.
What this means for MSPs
MSPs should educate clients on recognizing phishing tactics that leverage legitimate domains to appear credible. Users must avoid clicking on links or calling numbers provided in unsolicited emails and instead verify account changes by logging in directly through PayPal’s official website. Security teams should implement endpoint monitoring for unauthorized remote access tools and reinforce user awareness training to prevent social engineering attacks.
ClickFix Social Engineering Attacks Continue to Evolve
The ClickFix initial access technique, which tricks users into executing malicious code under the guise of fixing an error or completing a bot verification check, has surged in prevalence. Attackers increasingly refine these methods to evade detection while maintaining their effectiveness. A common variation uses the Windows mshta.exe utility to download and execute malware, often with misleading comments to reassure victims. Recent modifications include PowerShell wildcards and redundant backslashes to further obfuscate execution paths. This technique has been linked to the Emmenhtal loader, a payload previously analyzed by Orange Cyberdefense.
Other observed threats leveraging ClickFix include MintsLoader, which uses domain generation algorithms (DGA) to download secondary payloads, and HijackLoader, a widely abused loader delivered via malvertising and fake installers. Attackers now generate new DGA domains daily instead of weekly, making blocking efforts more difficult. HijackLoader continues to rely on DLL sideloading techniques, using legitimate software such as Waterfox to execute malicious code. These methods enable further payload deployment, including known infostealers such as Lumma and remote access tools such as SectopRAT.
What this means for MSPs
ClickFix attacks bypass traditional security controls by relying on user interaction, making user education and endpoint restrictions critical. MSPs should consider disabling the Windows Run dialogue via group policy or registry settings to prevent users from manually executing malicious commands. Additionally, security solutions must monitor process execution patterns, PowerShell abuse, and registry modifications to detect early-stage exploitation attempts.
Top vulnerabilities in February 2025
CVE-2025-24472
CVE-2025-24472 is a high-severity authentication bypass vulnerability affecting Fortinet's FortiOS and FortiProxy products. Specifically, it impacts FortiOS versions 7.0.0 through 7.0.16 and FortiProxy versions 7.0.0 through 7.0.19, as well as 7.2.0 through 7.2.12. This vulnerability allows remote attackers to gain super-admin privileges by sending specially crafted cooperative security fabric (CSF) proxy requests.
This past month, the CRU observed CVE-2025-24472 being used for initial access. The threat actors then attempted to run mimikatz to steal passwords and escalate privileges.
CVE-2024-55591
CVE-2024-55591 is a critical authentication bypass vulnerability affecting Fortinet's FortiOS and FortiProxy products. This flaw allows remote attackers to gain super-admin privileges by sending specially crafted requests to the Node.js websocket module.
This past month, the CRU observed CVE-2024-55591 being used for initial access. The threat actors then attempted to run mimikatz to steal passwords and escalate privileges.
CVE-2025-21391
This vulnerability allows attackers to escalate privileges and delete files within Windows storage. It has a CVSS base score of 7.1 and is marked as important in severity. Though its impact is somewhat limited to file deletions, it has been actively exploited in the wild, making it a priority for patching.
CVE-2025-21418
This zero-day vulnerability provides SYSTEM-level privileges through an elevation of privilege exploit targeting the Windows ancillary function driver for WinSock. It carries a CVSS base score of 7.8 and has been actively exploited, making it a serious concern for organizations running unpatched Windows systems.
CVE-2025-21194
This vulnerability, previously disclosed by Quarkslab, allows attackers to bypass security mechanisms under specific conditions. It has a CVSS score of 7.1 and is rated as important, but its complexity reduces its likelihood of widespread exploitation.
CVE-2025-21377
This vulnerability allows an attacker to spoof NTLM authentication, potentially leading to credential theft or unauthorized access. It has a **CVSS score of 6.5** and is rated as important, but it is considered more likely to be exploited due to its minimal interaction requirements.
CVE-2025-21376
A critical severity vulnerability (CVSS 8.1) in the lightweight directory access protocol (LDAP) can lead to remote code execution. Exploitation requires sending malicious requests to an LDAP server and winning a race condition to trigger a buffer overflow, making it a high-risk issue that could be exploited in real-world attacks.
CVE-2025-21400
This RCE vulnerability in SharePoint Server is rated as important with a CVSS score of 8.0. While it is more likely to be exploited, an attacker needs site owner permissions to execute the attack, making privilege escalation a prerequisite for exploitation.
Top five malware observed in February 2025
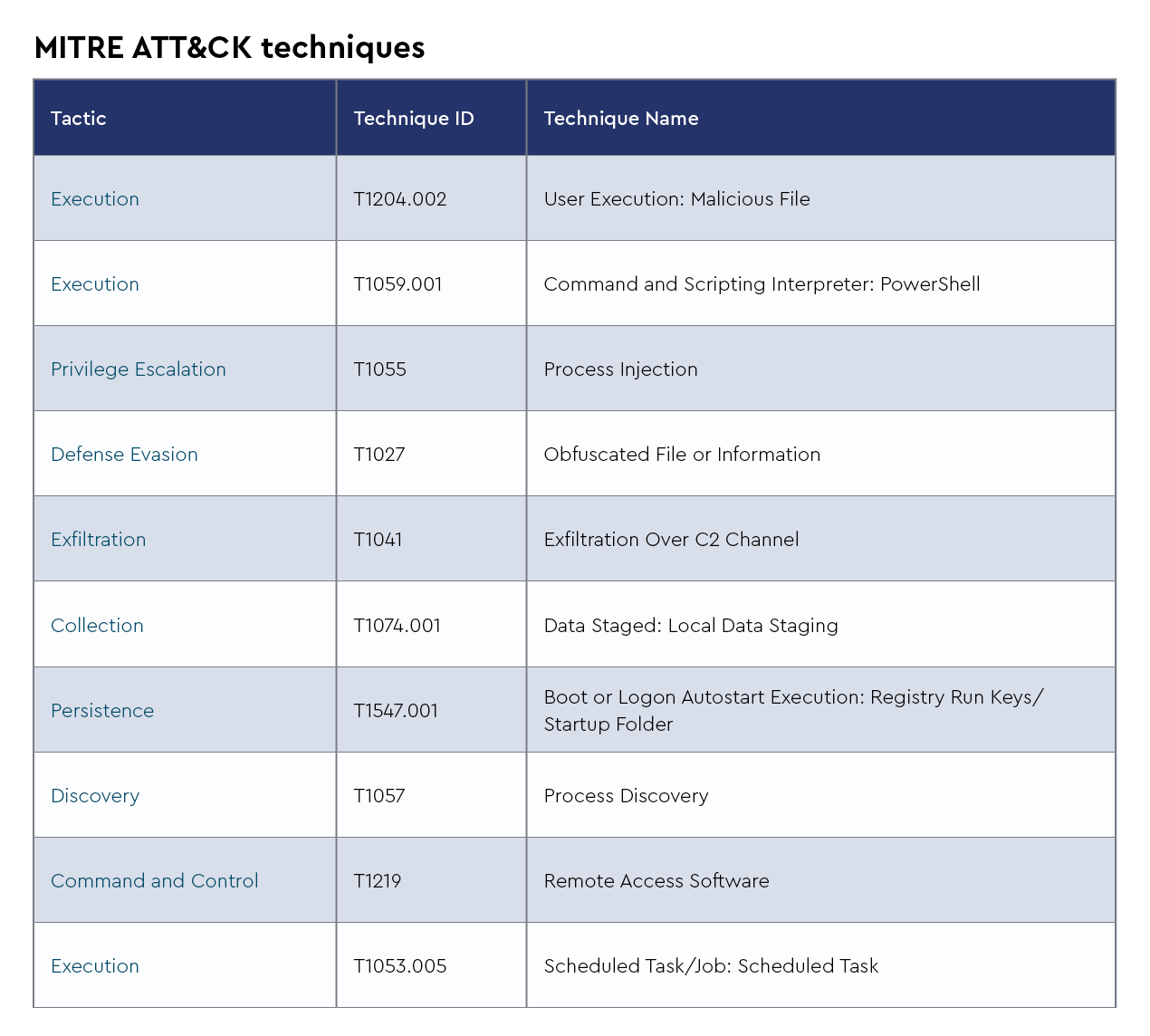
1. HijackLoader
HijackLoader is a modular malware loader first identified in mid-2023, designed to deliver various malicious payloads. Recent intelligence indicates that HijackLoader has incorporated advanced evasion techniques, including process hollowing and user account control (UAC) bypass, to enhance its stealth capabilities. The CRU has observed HijackLoader being used in a malvertising campaign to load RedLine Stealer, an infostealer, and Sectop RAT, a remote access trojan.
Adversary
- Aliases: DOILoader, GHOSTPULSE, IDAT Loader, SHADOWLADDER, win.hijackloader
- Last used by: Multiple MSIX FakeBAT Malvertising campaigns in 2024, Cisco Webex Infostealer campaign in 2024, Multiple ClickFix campaigns in 2025
Infrastructure
Victimology
- Recently targeted business sectors: Retail, nonprofit organizations, healthcare, entertainment, IT services
Capabilities

2. Lumma Stealer
Lumma Stealer is an information-stealing malware, first identified in August 2022. It’s designed to extract sensitive data such as passwords, browser information, and cryptocurrency wallet details. The CRU has recently observed it being distributed through deceptive methods, including fake CAPTCHA verification pages—a tactic known as "ClickFix"—malicious links on platforms such as GitHub, and cracked software downloads.
Adversary
- Aliases: LummaC2 Stealer, win.lumma, LummaC2, Lumma
- Last used by: Slavic Nation Empire (SNE), Multiple ClickFix campaigns
Infrastructure

Victimology
- Recently targeted business sectors: MSPs, financial services, heavy industries, food and beverage
Capabilities
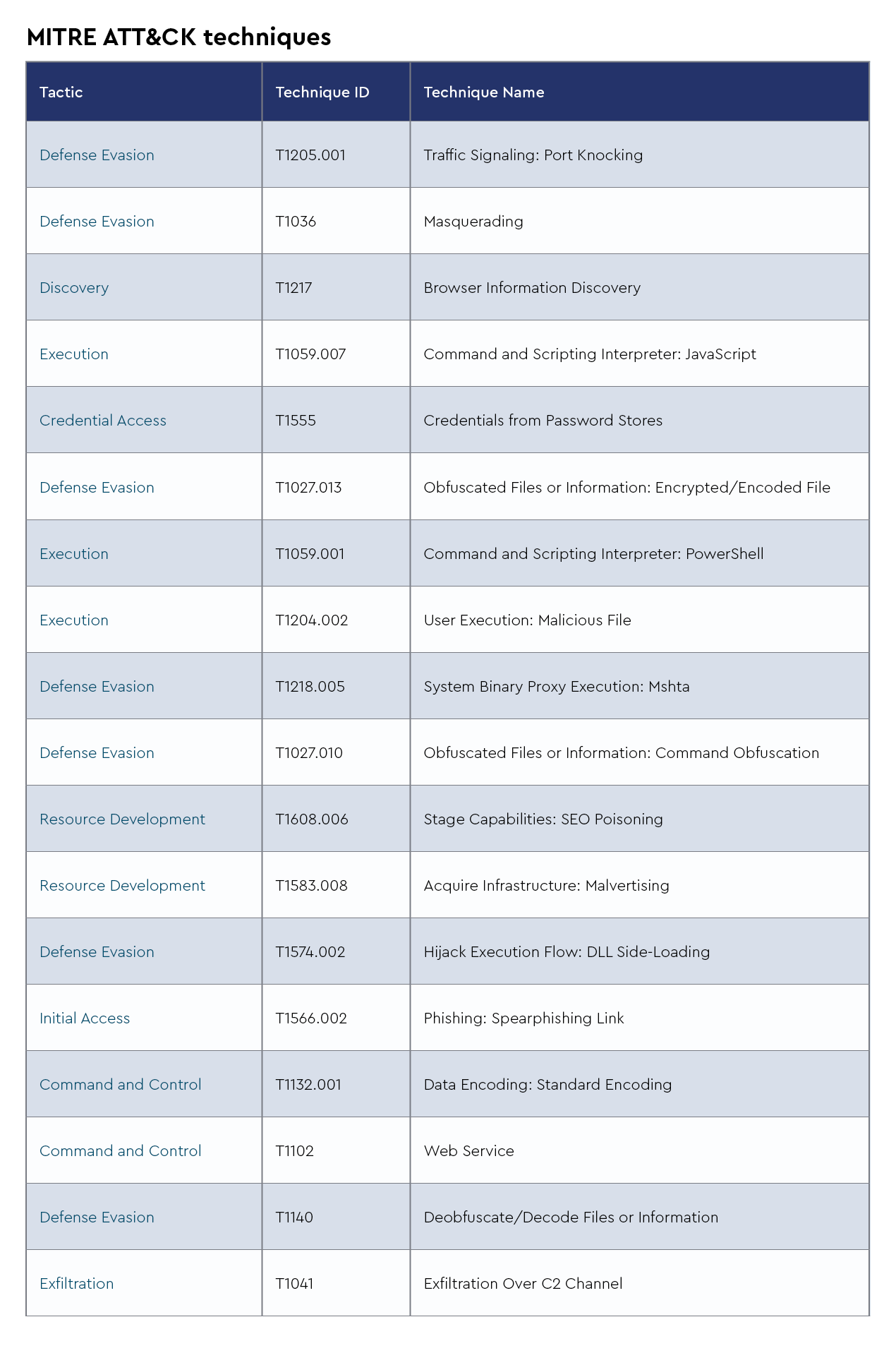
3. Emmenhtal
Emmenhtal is a stealthy malware loader, first identified in early 2024, designed to distribute various malicious payloads, including information stealers, such as Lumma. Emmenhtal employs advanced evasion techniques, such as using legitimate Windows tools (living off the land binaries and scripts, or LOLBAS) to execute malicious scripts, making detection challenging. Recently, the CRU has observed Emmenhtal being distributed alongside Lumma using the ClickFix technique, underscoring the evolving sophistication of these malware campaigns.
Adversary
- Aliases: IDATDropper, PEAKLIGHT, win.emmenhtal
- Last used by: Slavic Nation Empire (SNE), Multiple ClickFix campaigns
Infrastructure

Victimology
- Recently targeted business sectors: Entertainment, business development, community service/non-profit, financial services, law services
Capabilities
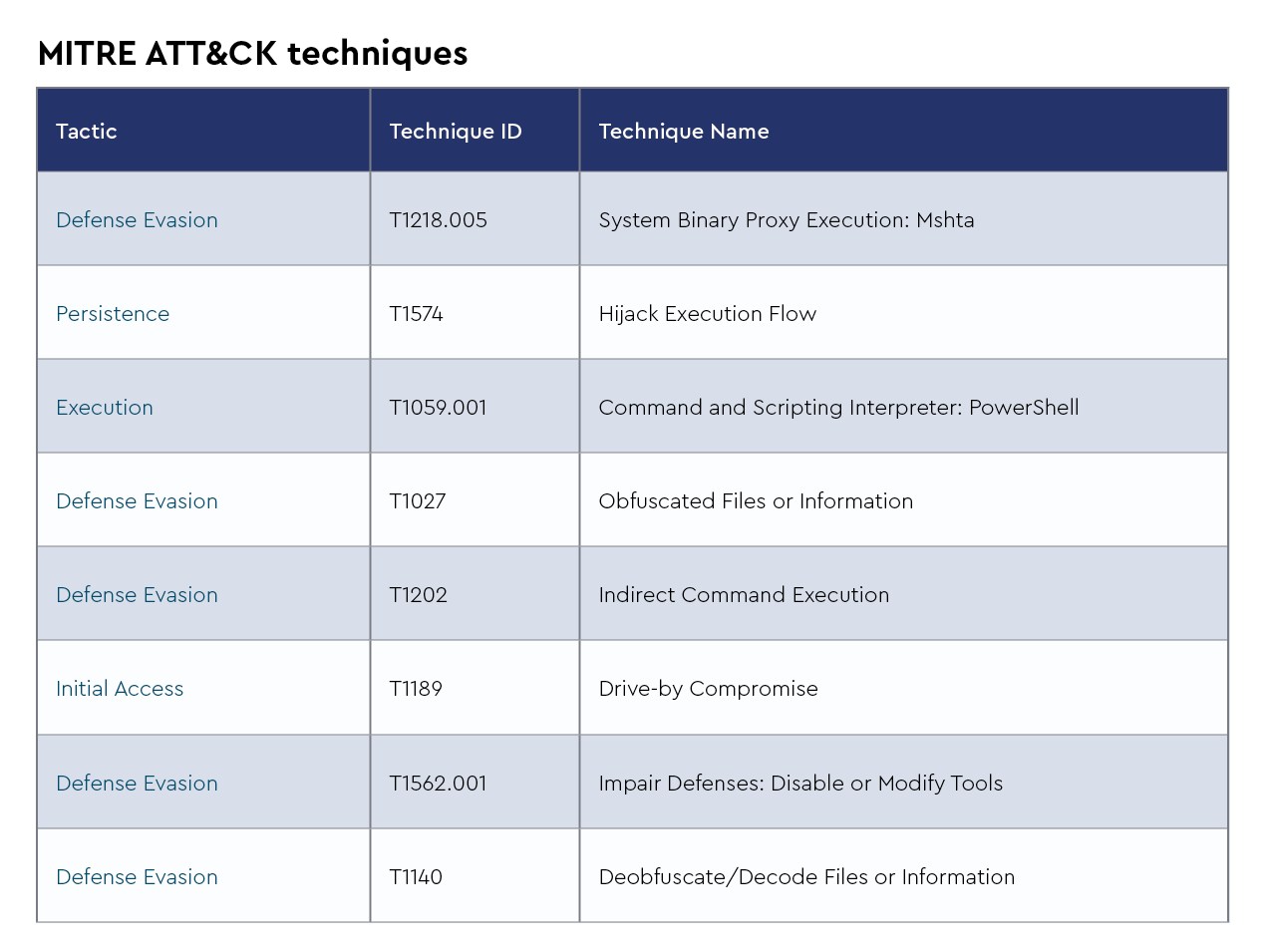
4. Vidar
Vidar Stealer is an information-stealing malware that extracts sensitive data such as credentials, browser information, and cryptocurrency wallet details. It has been distributed through deceptive methods, including fake CAPTCHA verification pages—a tactic known as "ClickFix"—and compromised websites. Notably, recent campaigns have involved the use of ClearFake, a variant of ClickFix, to deliver Vidar Stealer, highlighting the evolving sophistication of these malware distribution techniques.
Adversary
- Aliases: vidar, Vidar Stealer
- Last used by: Slavic Nation Empire (SNE), Multiple ClickFix campaigns
Infrastructure

Victimology
- Recently targeted business sectors: Healthcare, event planning, real estate, manufacturing, construction
Capabilities
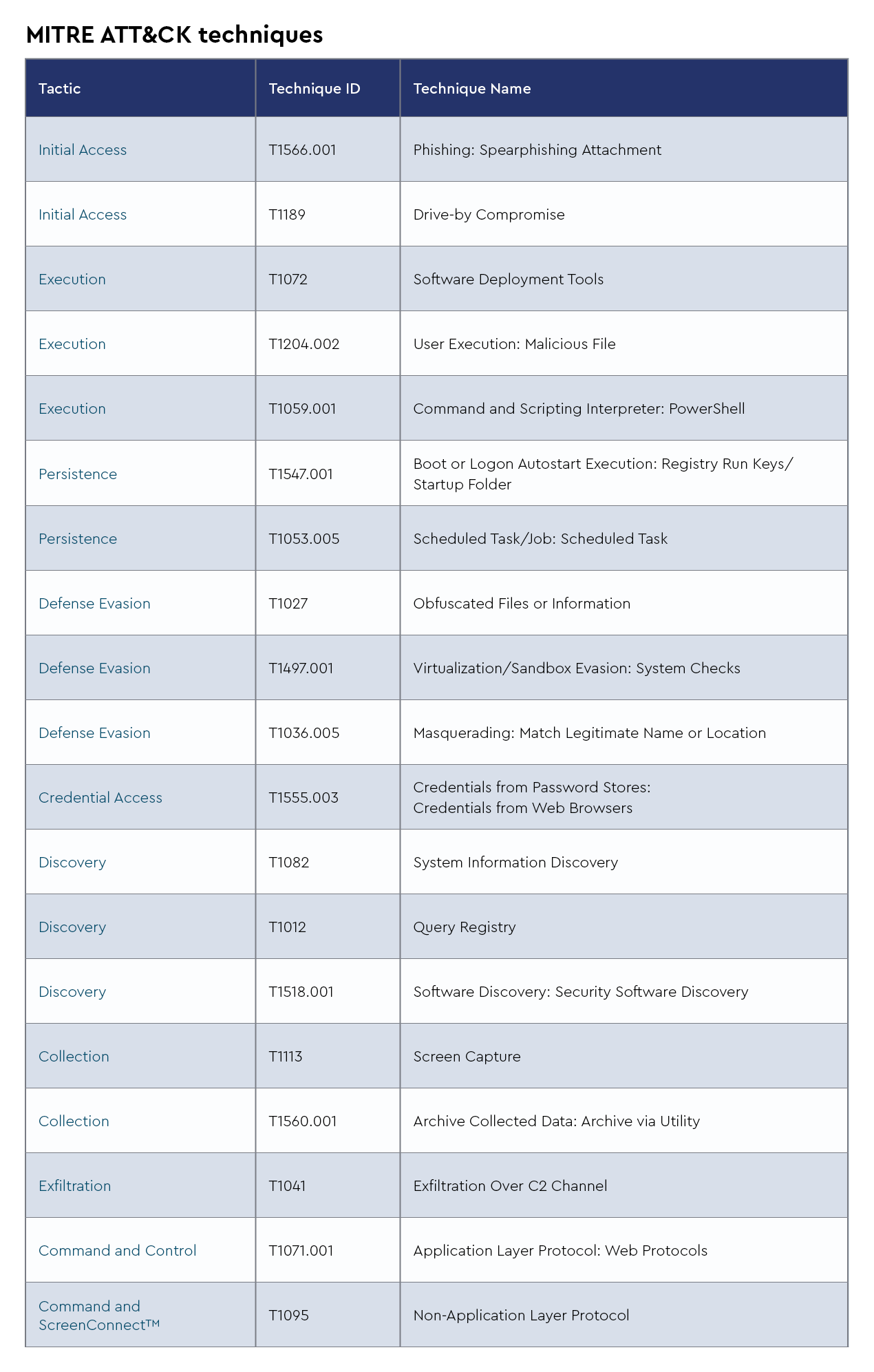
5. NetSupport Manager RAT
NetSupport Manager RAT is a remote access trojan that grants attackers full control over compromised systems, enabling activities such as screen monitoring, file manipulation, and execution of malicious commands. Recent intelligence from the CRU indicates a surge in NetSupport Manager RAT deployments via ClickFix campaigns, with threat actors leveraging fake error messages to trick users into executing malicious PowerShell scripts, leading to system compromise.
Adversary
- Aliases: Net Support RAT, NetSupport, NetSupportManager RAT
- Last used by: Slavic Nation Empire (SNE), Trading View crypto scam, Multiple ClickFix campaigns, TA571
Infrastructure

Victimology
- Recently targeted business sectors: Retail, healthcare, hospitality, law services, construction, manufacturing
Capabilities