Monthly Threat Brief: January 2024
Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU).
In this threat brief, we will provide raw data statistics, intel on specific threats, and a list of new detection signatures added to the ConnectWise SIEM™ throughout the month of January.
For a more detailed explanation of the overall trends and analysis of these numbers, check out our annual and quarterly threat reports. For comparison, December’s threat brief can be found here.
January 2024 stats
IOCs
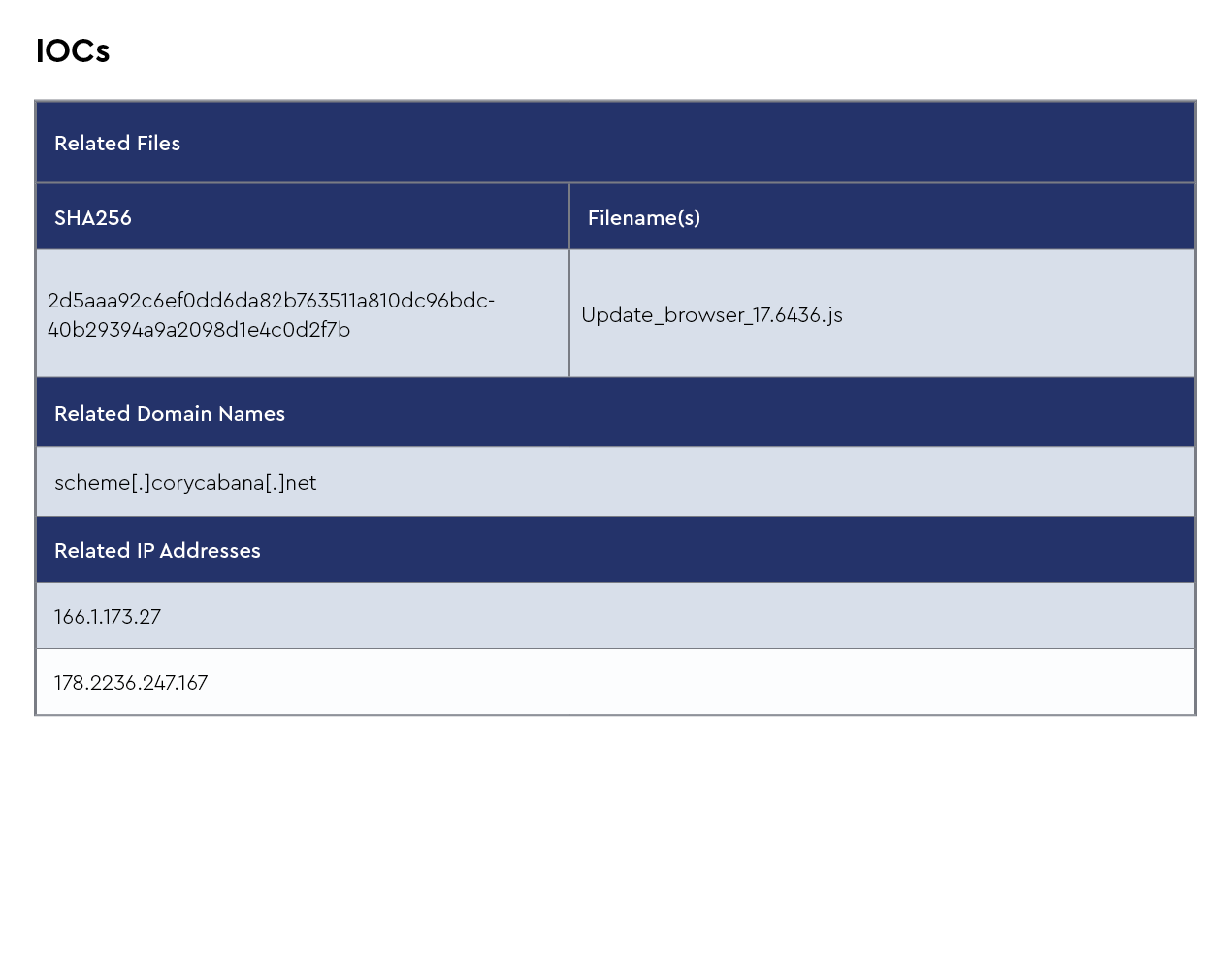
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected. We intend to launch streaming threat feeds based on this data later this year, so stay tuned!
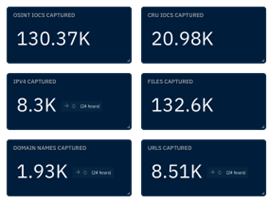
Figure 1: Summary of IOCs collected in January 2024
TTPs
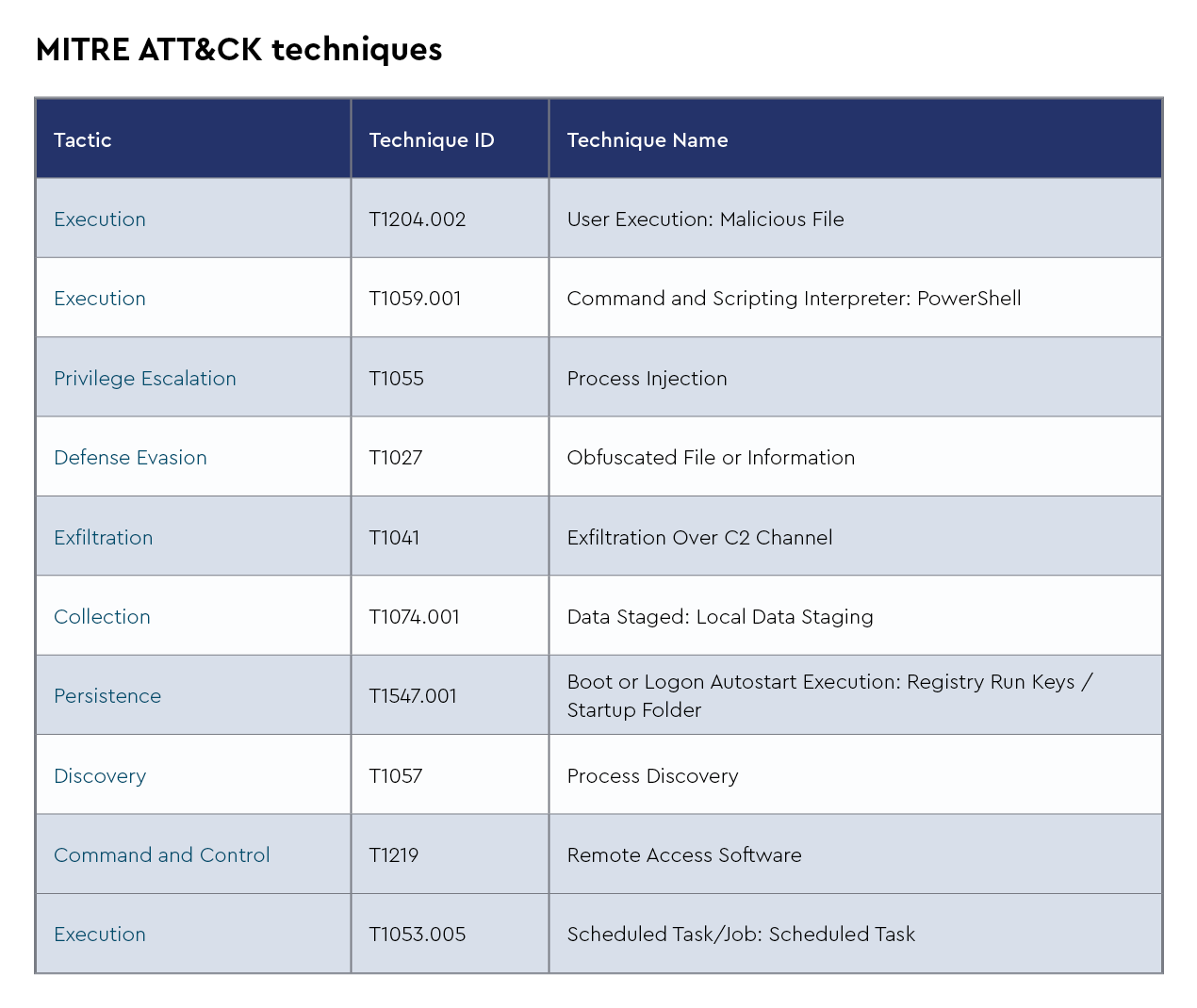
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for December 2023—provided for comparison—and January 2024.
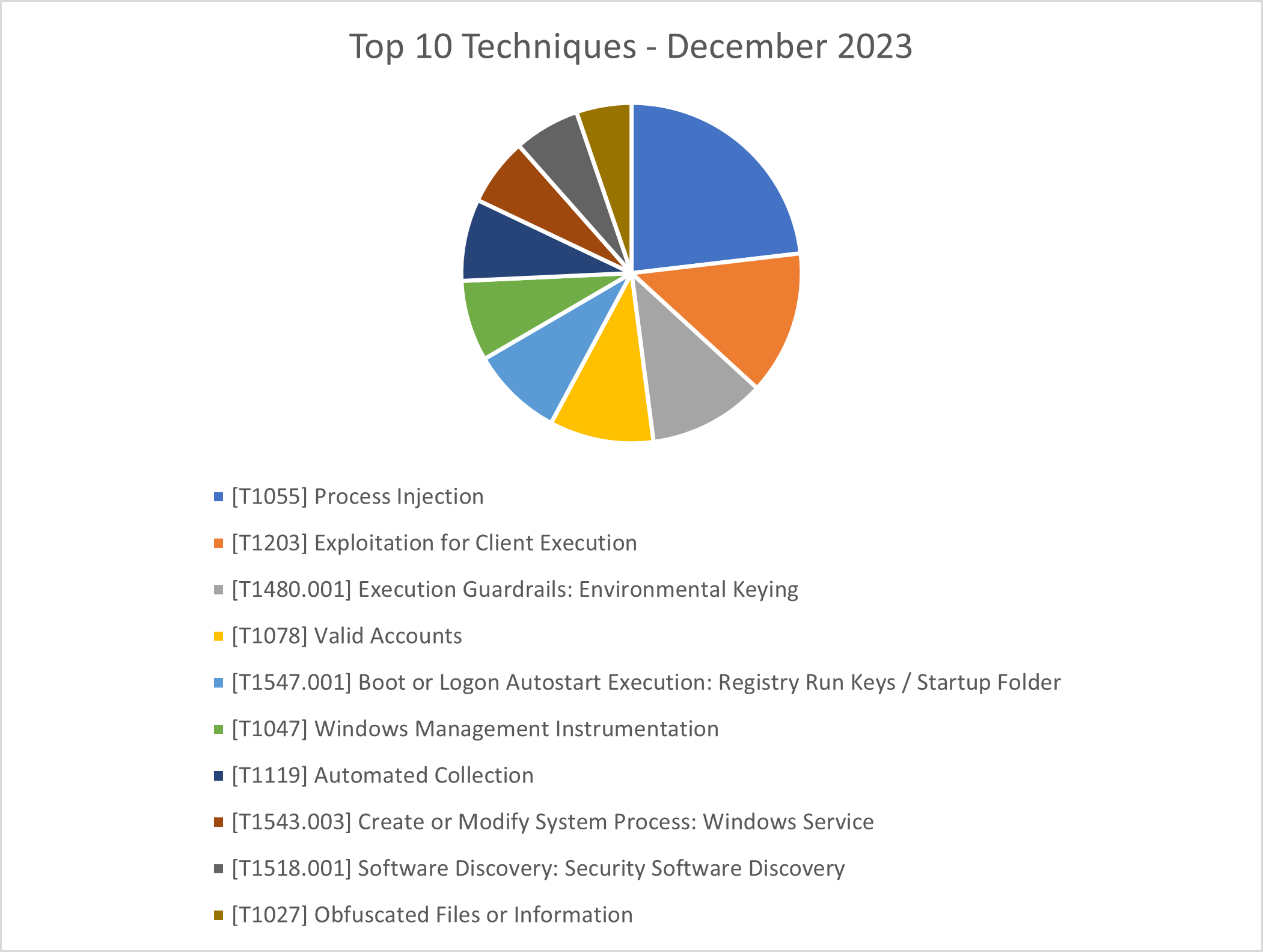
Figure 2: Top 10 MITRE ATT&CK techniques observed in December 2023
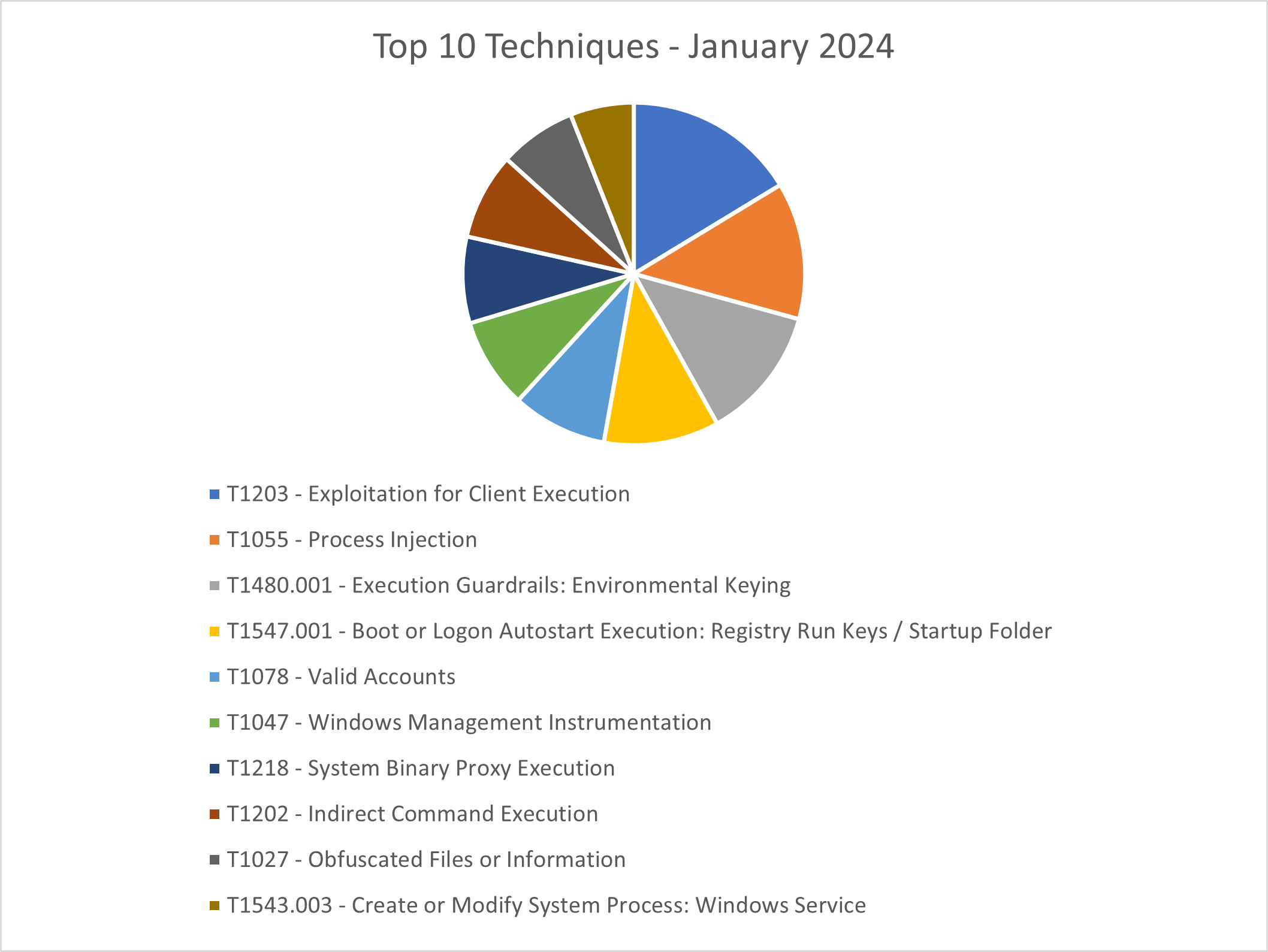
Figure 3: Top 10 MITRE ATT&CK techniques observed in January 2024
Latest threats
Each month, we highlight threats that we have seen targeting our MSP partners and their clients. This month, the ConnectWise SOC saw multiple incidents of SOCGholish and NetSupport RAT.
SOCGholish
SOCGholish, also known as FakeUpdate(s), is a downloader written in JavaScript that lures victims into downloading malware by pretending to be a software update. It typically relies on [T1189] drive-by compromise for [TA0001] initial access. As a downloader, its primary purpose is to download other malware and has been used to download and deploy Dridex, NetSupport, DoppelPaymer, and others. More specifically, we have recently observed a number of SOCGholish infections downloading NetSupport RAT—see below—during January 2024.
NetSupport RAT
NetSupport Manager is a legitimate remote-control utility first released in 1989. The legitimate application has been modified and re-purposed by malicious threat actors and renamed NetSupport RAT. It supports file transfers, chat with support, inventory management, and remote-control access. Threat actors will commonly attempt to re-purpose legitimate tools for nefarious purposes as a [TA0005] defense evasion tactic.
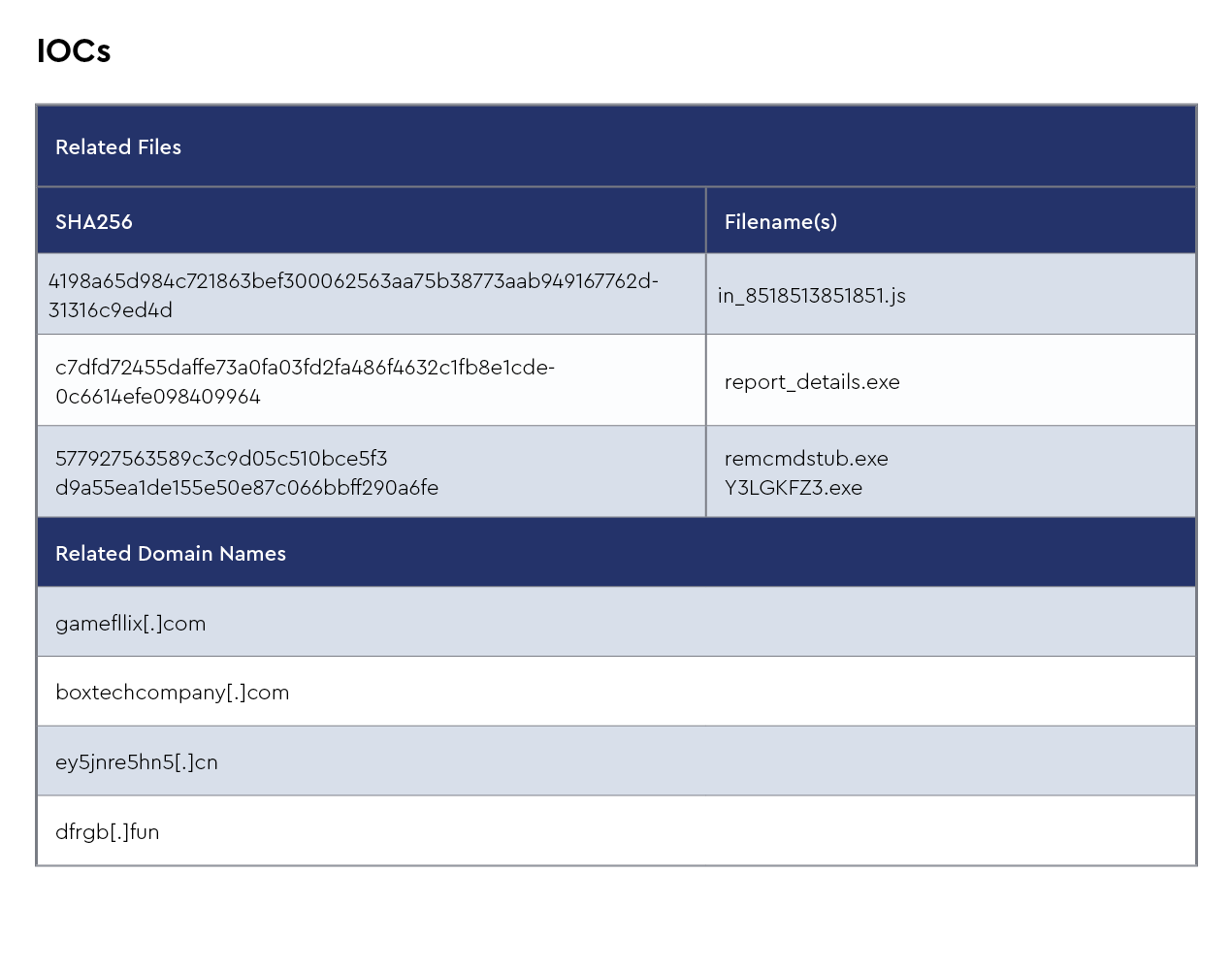
New ConnectWise SIEM signatures
Several new ConnectWise SIEM detection signatures were added in January 2024. These include:
- [CRU][Windows] Lateral movement using DCOM Excel.Application
Technique detected: [T1021.003] Remote Services: Distributed Component Object Model
Description: Excel’s ActivateMicrosoftApp() method allows the user shell access because Microsoft still supports activation of some end-of-life (EOL) software, such as FoxPro, Office Project, and Schedule Plus. It is unlikely that any of these legacy applications will be installed on modern environments, but an attacker could still abuse this vulnerability for lateral movement and persistence techniques.
Prerequisites for this attack include:
- Requires local admin privilege on the target
- Requires Microsoft Excel installed on the target
- Ability to remotely write a file in the system PATH
The location where users most commonly have write permission to the PATH is C:\Users<User>\AppData\Local\Microsoft\WindowsApps.
- [CRU][Windows] Cached MSI package executing Rundll32
Technique detected: [T1218] System Binary Proxy Execution
Description: Found in a resurgence of Qakbot in December 2023. An MSI installer package resulted in the execution of a dynamically linked file via rundll32.exe. Normal behavior of an MSI installer will cache the package under the path C:\Windows\Installer and then execute itself C:\Windows\system32\MsiExec.exe -Embedding <GUID>.
In addition to the normal behavior, Qakbot and other malware, such as Danabot, have been seen to proxy execute rundll32 via the cached package.
- [CRU][Windows] Suspicious Windows problem reporting (wermgr.exe) loaded DLL
Technique detected: [T1055] Process Injection
Description: In recent observations of Qakbot from December 2023, wermgr.exe was seen directly loading and using urlmon.dll.
urlmon.dll is primarily involved in handling URLs and related network functions, which resulted in wermgr.dll making outbound connections. This falls outside of normal behavior and image loads by wermgr.exe.
- [CRU][Windows] Conhost.exe renamed or executed From suspicious path
Technique detected: [T1036.005] Masquerading: Match Legitimate Name or Location
Description: This alerts on conhost.exe running from unexpected directories that aren’t System32. Malware will often run masquerading as a system process from other directories by renaming malicious binaries to those system process names.
- [CRU][Windows] conhost.exe headless execution
Technique detected: [T1202] Indirect Command Execution
Description:The true parent of a process can be obscured by running it as a child of conhost.exe with its headless parameter. With the exception of some common exclusions, this behavior is unusual and has been leveraged by malicious actors in several campaigns. Investigate the parent process of the conhost.exe call and the resulting events from the child of this conhost.exe process.


